
The B2B platform for the best purchasing descision. Identify and compare relevant B2B manufacturers, suppliers and retailers
Close
Filter
Result configuration
Continents
Select continent
Locations
Result types
Company type
Select company type
Industries
Select industry
Company status
Select company status preset
Number of employees
Min.
Max.
Founding year
Ebryx (Pvt.) Ltd.
Lahore, Pakistan
E
51-100 Employees
2008
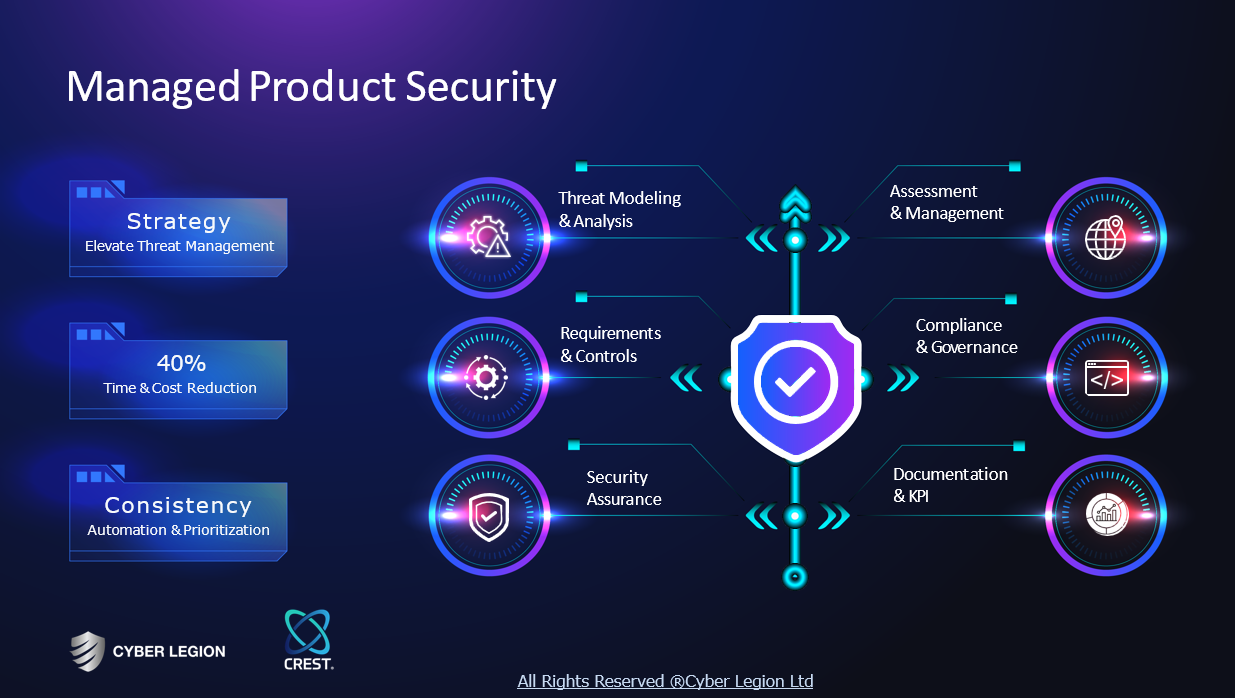
Key takeaway
Ebryx is a prominent cybersecurity leader, offering a comprehensive suite of services that includes 360° cybersecurity, security product engineering, and a proprietary Zero Trust Network Access solution called Invisily. With over a decade of experience, Ebryx empowers organizations, including Fortune 500 companies and government entities, by providing innovative cybersecurity solutions to enhance their security posture.
Reference
Product
Cyber Defense Boot Camp - Ebryx
Cyber Espial Pvt Ltd
Khushab, Pakistan
E
11-50 Employees
-
Key takeaway
Cyber Espial Pvt Ltd is a prominent cybersecurity company dedicated to protecting businesses and consumers from cyber threats through services like penetration testing and network security. They focus on identifying vulnerabilities before hackers can exploit them, making them a trusted partner for SaaS companies seeking robust cybersecurity measures.
Reference
Core business
Cyber Espial - Trusted Cybersecurity Partner for SaaS Companies
Cyber Espial is the reliable partner for SaaS across the globe when it comes to Network and Web Pentesting, VAM and Compliance.
Catalyic Security
Lahore, Pakistan
E
251-500 Employees
2012
Key takeaway
Catalyic Security is a managed security service company that offers a comprehensive range of tailored information and cybersecurity services, including real-time assessments and internationally accredited IT security training. With over 15 years of experience, they align IT with business goals while managing risks and ensuring compliance with industry regulations.
Reference
Service
Cybersecurity Services - Catalyic Security
Catalyic Security provides best cybersecurity services weather its managed security services, GRC, offensive security or security tools.
Looking for more accurate results?
Find the right companies for free by entering your custom query!
25M+ companies
250M+ products
Free to use
Security Foster
Karachi Division, Pakistan
E
11-50 Employees
2021
Key takeaway
Security Foster emphasizes its commitment to delivering high-quality security services and expertise in addressing cyber threats. Their team works closely with clients' IT or security personnel to stay updated on incidents, positioning them as a trusted partner in cybersecurity.
Reference
Service
Security Foster | Services
Graxo Consulting (Pvt) Ltd
Islamabad, Pakistan
E
11-50 Employees
2018
Key takeaway
The company is dedicated to safeguarding your data through advanced cybersecurity protocols and a team of certified professionals. They offer compliance services for international standards and provide vulnerability assessments and penetration testing to ensure a secure environment for businesses.
Reference
Core business
Home - Graxo Consulting
Multiple unique services are available under one umbrella so you can focus on your core business, while we protect your business to thrive.
cyberatic security
Multan, Pakistan
E
1-10 Employees
2016
Key takeaway
Cyberatic is a Pakistan-based agency specializing in cybersecurity services, offering ethical hacking and comprehensive security solutions to protect organizations from various cyber threats. Their Cybersecurity Platform emphasizes preparation, prevention, detection, and response, ensuring robust security for people, information, and networks.
Reference
Core business
Cyberatic Total Endpoint Security
Total Endpoint Security Offensive and Defensive Teams Always-on. Always protected.Cyberatic® Is Intelligent Security. Protect your organization with a modern unified endpoint security solution. Our end-to-end approach to cybersecurity is deeply rooted in Cylance® AI and machines.
SECISYS
Islamabad, Pakistan
E
11-50 Employees
2018
Key takeaway
Secisys specializes in providing comprehensive information security solutions, including services related to cyber security, risk assessments, and training in areas such as ethical hacking and information system auditing. Their commitment to supporting businesses and institutions in enhancing their information security programs aligns with their vision of securing the future and protecting data.
Reference
Product
Products – Secisys
Supersecure
Karachi Division, Pakistan
E
51-100 Employees
2017
Key takeaway
Supersecure is a Managed Security Service Provider (MSSP) that specializes in cybersecurity, offering advanced threat protection, compliance, and risk management services to organizations of all sizes, including government entities. Their dedicated team and scalable services are designed to address the increasing demand for IT security in the face of persistent cyber threats.
Reference
Core business
Home - Super Secure
Cydea Tech
Islamabad, Pakistan
E
51-100 Employees
2019
Key takeaway
Cydea Tech is a leading cybersecurity solution company that addresses global cybersecurity challenges through innovative research and affordable technology solutions. Their products, including the Cydea Threat Intelligence Platform and Cydea Deception Platform, empower security teams with actionable intelligence to predict, detect, and respond to threats, ensuring that enterprises stay one step ahead of cybercriminals.
Reference
Core business
Cyber Expert Networking -Cyber Security Solution - CydeaTech
Cydea Technology is the No.1 Leading cybersecurity solution company that protects your valuable assets against a multitude of cyber-criminal attacks.
Concave FORT
Islamabad, Pakistan
E
11-50 Employees
2021
Key takeaway
The company offers a comprehensive range of cyber security services and solutions designed to protect businesses from various cyber threats. Their expertise includes advanced network security measures such as firewall configuration and intrusion detection systems, ensuring robust defenses for digital assets.
Reference
Product
Network Security Services - Enhance Your Cyber Defenses Now
Protect your network from cyber threats with our cutting-edge Network Security Services. Our experts offer comprehensive solutions, including firewall configuration, intrusion detection systems, and secure VPN setup, ensuring the utmost security for your digital assets.
Technologies which have been searched by others and may be interesting for you:
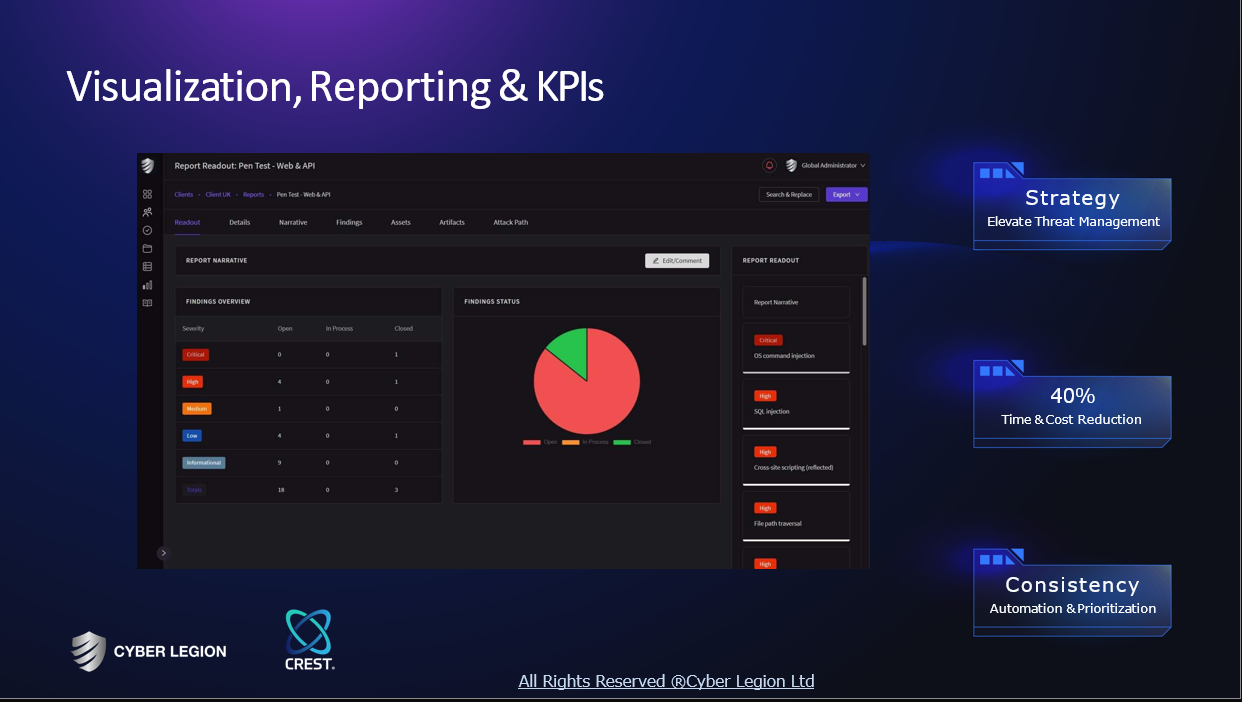
A selection of suitable products and services provided by verified companies according to your search.

Product
Text Anonymization Service
Go to product
Service
Security Consultant
Go to product
Service
Product Security
Go to product

Product
enclaive vHSM
Go to product
A selection of suitable use cases for products or services provided by verified companies according to your search.

Use case
Cybersecurity
All
Cybersecurity is the act of protecting your digital assets against bad actors attack. This is a vast field which starts by identifying the risk in your industry and mitigating these risks on the best of your ability. There is always the probability that a bad actor will penetrate your defense system, in that case you should have in place a response plan. Are your digital assets protected?

Use case
Managed Firewall für ein öffentliches Unternehmen – NIS2-Compliance gewährleistet
Public Sector
Herausforderung: Ein öffentliches Versorgungsunternehmen steht vor der Aufgabe, seine IT-Infrastruktur gegen wachsende Cyberbedrohungen abzusichern und gleichzeitig die Vorgaben der NIS-Richtlinie (Network and Information Security) zu erfüllen. Die internen IT-Ressourcen reichen nicht aus, um die Anforderungen an kontinuierliche Überwachung, Aktualisierungen und Protokollierung zu bewältigen. Lösung: Mit der Managed Firewall von bytehaus wird die Sicherheitsinfrastruktur des Unternehmens auf den neuesten Stand gebracht. Bytehaus analysiert die Netzwerkarchitektur und implementiert eine maßgeschneiderte Firewall-Lösung, die den strengen Anforderungen der NIS-Richtlinie entspricht.

Use case
Managed Firewall für ein Unternehmen mit 10 Mitarbeitern – Prävention nach früherem Hackerangriff
Supplier
Herausforderung: Ein mittelständisches Unternehmen mit 10 Mitarbeitern wurde vor einigen Jahren Opfer eines Hackerangriffs, bei dem sensible Daten gestohlen und der Betrieb erheblich beeinträchtigt wurden. Seitdem besteht ein hohes Sicherheitsbewusstsein, jedoch fehlen die internen Ressourcen, um die IT-Sicherheit auf dem aktuellen Stand zu halten und neue Bedrohungen abzuwehren. Lösung: Mit der Managed Firewall von Bytehaus erhält das Unternehmen eine umfassende Sicherheitslösung, die speziell auf kleine Unternehmen mit begrenzten IT-Ressourcen zugeschnitten ist. Bytehaus übernimmt die Implementierung, Verwaltung und Überwachung der Firewall, sodass das Unternehmen vor zukünftigen Angriffen optimal geschützt ist.

Use case
Protecting Critical Infrastructure from Cyber Threats
KRITIS, Critical Infrastructure, Industries with Sensitive Data, Healthcare, Energy, Gov, Supplier
Operators of critical infrastructure such as energy, water, transportation, and healthcare are prime targets for cyberattacks. Many industrial control systems (ICS) and SCADA environments sometimes rely software that is difficult to patch, while strict regulatory requirements like NIS2 and BSI-KritisV demand enhanced security measures. Labyrinth uses specialized SCADA and OT decoys to simulate real industrial control systems, misleading attackers and capturing their activity without impacting operational performance. This ensures early threat detection, supports regulatory compliance with detailed forensic reporting, and protects against APTs and ransomware targeting critical systems.

Use case
Protecting SMEs Against Targeted Cyber Attacks
SME, all
Small and medium-sized enterprises (SMEs) often have limited IT resources and no dedicated Security Operations Center (SOC). They are particularly vulnerable to ransomware, phishing attacks, and data theft as traditional security systems like firewalls or antivirus software fail to counter modern threats. Labyrinth provides an easy-to-implement and cost-efficient deception technology that lures attackers into simulated IT environments, enabling threat detection up to 12 times faster before real damage occurs. This proactive approach reduces false positives, minimizes downtime, and ensures effective cybersecurity without requiring additional IT staff or high costs.

Use case
Reducing SOC Workload in Large Enterprises
Enterprise, all
Security teams in large enterprises face an overwhelming number of security alerts, including many false positives, making it difficult to detect and respond to advanced persistent threats (APTs). Labyrinth deploys highly realistic decoys within corporate networks, attracting and identifying attackers before they can infiltrate critical systems. By providing detailed forensic insights and attack timelines, Labyrinth helps SOC teams focus on real threats, reduces alert fatigue, and seamlessly integrates with existing SIEM, EDR, and firewall solutions for automated defense.

Use case
Cybersecurity
All
Cybersecurity is the act of protecting your digital assets against bad actors attack. This is a vast field which starts by identifying the risk in your industry and mitigating these risks on the best of your ability. There is always the probability that a bad actor will penetrate your defense system, in that case you should have in place a response plan. Are your digital assets protected?
When exploring the Cyber Security industry in Pakistan, several key considerations come into play. The regulatory environment is crucial, as the government is increasingly focusing on enhancing cybersecurity measures through initiatives like the National Cyber Security Policy. This policy aims to protect critical infrastructure and promote a secure digital environment. Challenges such as a skilled labor shortage and evolving cyber threats must be acknowledged, as these factors can impact the industry's growth and effectiveness. Opportunities abound in this sector due to the rising digitalization of businesses and the increasing awareness of cyber threats among organizations. As more companies seek to safeguard their data, the demand for cybersecurity solutions is expected to grow. The competitive landscape features both established firms and emerging startups, fostering innovation and collaboration. Additionally, Pakistan's strategic location and participation in global cybersecurity initiatives position it as a relevant player in the global market. Environmental concerns, while not directly linked to cybersecurity, should be considered, especially regarding data centers and their energy consumption. Ultimately, thorough research into these aspects can provide valuable insights for anyone interested in entering or investing in the Cyber Security industry in Pakistan.
Some interesting numbers and facts about your company results for Cyber Security
| Country with most fitting companies | Pakistan |
| Amount of fitting manufacturers | 66 |
| Amount of suitable service providers | 75 |
| Average amount of employees | 11-50 |
| Oldest suiting company | 2008 |
| Youngest suiting company | 2021 |
Some interesting questions that has been asked about the results you have just received for Cyber Security
What are related technologies to Cyber Security?
Based on our calculations related technologies to Cyber Security are Space Technologies, Military, Commercial Aviation, Airport Security
Who are Start-Ups in the field of Cyber Security?
Start-Ups who are working in Cyber Security are Security Foster, Concave FORT
Which industries are mostly working on Cyber Security?
The most represented industries which are working in Cyber Security are IT, Software and Services, Defense, Retail, Telecommunications
How does ensun find these Cyber Security Companies?
ensun uses an advanced search and ranking system capable of sifting through millions of companies and hundreds of millions of products and services to identify suitable matches. This is achieved by leveraging cutting-edge technologies, including Artificial Intelligence.