
The B2B platform for the best purchasing descision. Identify and compare relevant B2B manufacturers, suppliers and retailers
Close
Filter
Result configuration
Continents
Select continent
Locations
Result types
Company type
Select company type
Industries
Select industry
Company status
Select company status preset
Number of employees
Min.
Max.
Founding year
Atlantic Data Security
East Hartford, United States
B
11-50 Employees
1993
Key takeaway
With over 30 years of experience in the cybersecurity industry, the company specializes in creating and managing comprehensive security infrastructures tailored to meet the evolving needs of clients. Their team of skilled engineers is dedicated to protecting assets and provides access to leading cybersecurity technologies and services.
Reference
Core business
The Premier Cybersecurity Solutions Provider
Cyber Protect LLC
United States
B
1-10 Employees
2019
Key takeaway
Cyber Protect LLC offers exceptional cyber security services in Michigan, ensuring companies have robust control over their cybersecurity infrastructure through tailored strategies. Their dedicated team of experts focuses on simplifying cyber security, allowing businesses to concentrate on their core operations.
Reference
Core business
Home of the Cybersecurity Specialist - Cyber Protect LLC
Cybersecurity simplified. We provide smart solutions for companies of all sizes and pride ourselves on our unparalleled, dedicated service. GET A FREE QUOTE
Blue Cloak
Sterling, United States
B
11-50 Employees
2015
Key takeaway
The company specializes in cybersecurity, providing customizable mobile cyber ranges for testing, training, and validation. Their skilled IT security experts focus on developing robust cybersecurity policies and integrating real and simulated operations to enhance response capabilities.
Reference
Service
Cybersecurity | Blue Cloak
Looking for more accurate results?
Find the right companies for free by entering your custom query!
25M+ companies
250M+ products
Free to use
Curator Cyber Security
Virginia Beach, United States
B
1-10 Employees
2020
Key takeaway
The company specializes in providing experienced cyber security specialists to support IT teams, offering training, high-level talent, and project management. Their leadership collaborates closely with client leaders to ensure effective planning and consulting.
Reference
Core business
Home
Cyber Security Global
Frisco, United States
B
51-100 Employees
2007
Key takeaway
Cyber Security Global™ is a leading provider of cyber security management consulting and professional services, offering training and boot camp preparations for key industry certifications such as CISSP, CISM, CISA, CEH, and CompTIA Security+.
Reference
Core business
About – CyberSecurityGlobal™
CYBER BUYER
Charlotte, United States
B
1-10 Employees
2018
Key takeaway
The company specializes in providing and implementing new and emerging Cloud and SaaS Cyber Security solutions, making it a valuable resource for CISOs and cyber security leaders. With a wide range of over 200 Independent Software Vendor solutions and managed security services, they focus on helping businesses enhance their cyber security posture.
Reference
Core business
CYBER BUYER | Cyber Security Software Outfitters and Marketplace | CYBER BUYER LLC
With CYBER BUYER, we help you focus your efforts on effective investments in new cyber security technologies that Stop More Attacks, Find Breaches Faster, Fix Breaches Faster and Lower Breach Impact.
Cybervizor LTD
United States
B
11-50 Employees
2015
Key takeaway
Cyber Vizor guides global enterprises in their cyber security strategies, offering expert advice on best practices to combat data breaches and cyber attacks. They provide a wide range of integrated solutions and stay updated with the latest protection technologies, ensuring long-term support for their clients' security needs.
Reference
Core business
Cyber Vizor LTD - Home
CyberVizor - Your Protective Mask , Experts in Cyber-Security Consulting & Integration.
Cyber Protection Services
Columbia, United States
B
11-50 Employees
2019
Key takeaway
Cyber Protection Services is a leading authority in cybersecurity, offering high-security solutions to safeguard data from cyber threats. Their expert team specializes in assessing vulnerabilities and developing customized defense strategies, ensuring businesses can operate confidently without the fear of cyber attacks.
Reference
Core business
Cybersecurity In Maryland | Cyber Protection Services
Cyber Protection Services offers cybersecurity compliance and configuration expertise to MSPs, SMBs, and government agencies.
SEPNIX
Los Angeles, United States
B
1-10 Employees
2021
Key takeaway
SEPNIX, founded in 2021 in Los Angeles, specializes in enhancing digital defenses against cyberattacks and ransomware through comprehensive cloud security technologies. Their elite team of cybersecurity engineers offers services that include data protection, network security configuration, and incident response management, ensuring robust protection for corporate networks.
Reference
Core business
Cyber Security Services and Consulting
CyberArq
Miami, United States
B
11-50 Employees
-
Key takeaway
CyberArq is a dedicated cyber security consulting firm that focuses on assessing and securing organizations' critical data assets to stay ahead of cyber threats. Their team of experts employs white hat hacking techniques to identify security vulnerabilities, ensuring robust protection and compliance for their clients.
Reference
Core business
CyberArq: Cyber Security Consulting
CyberArq experts identify security gaps through assessing, securing, and deploying industry standards to protect corporate data assets.
Technologies which have been searched by others and may be interesting for you:
A selection of suitable products and services provided by verified companies according to your search.

Product
Text Anonymization Service
Go to product
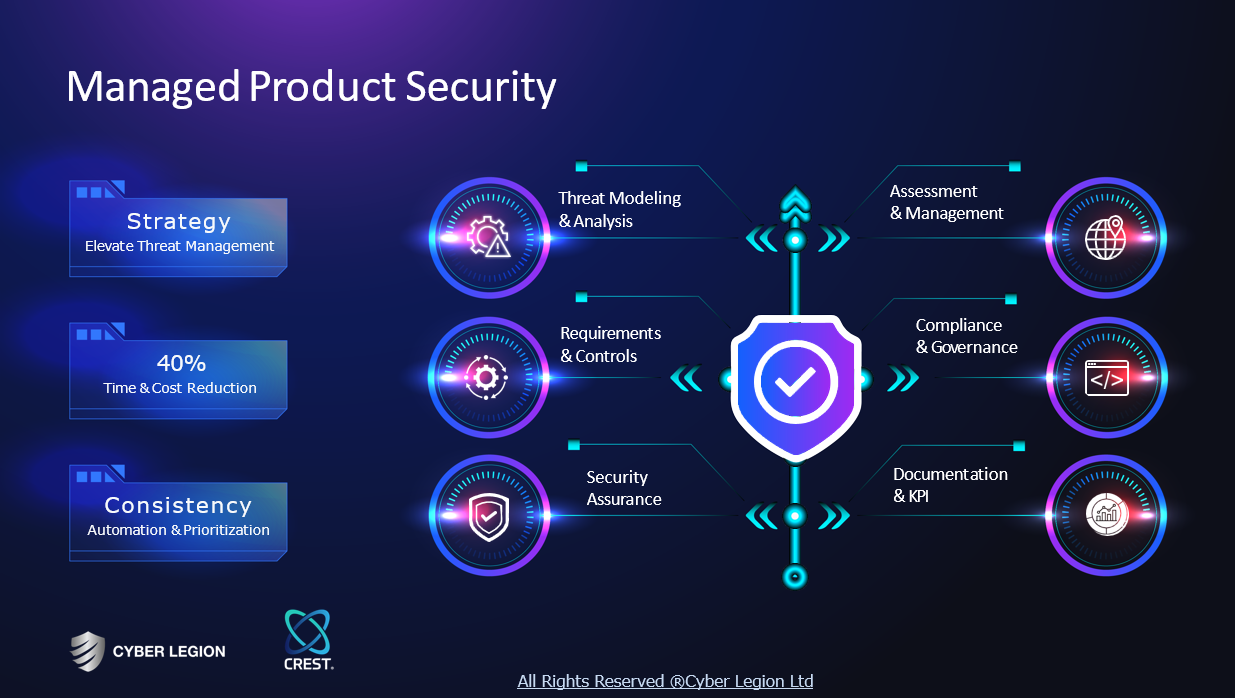
Service
Security Consultant
Go to product
Service
Product Security
Go to product

Product
enclaive vHSM
Go to product
A selection of suitable use cases for products or services provided by verified companies according to your search.

Use case
Cybersecurity
All
Cybersecurity is the act of protecting your digital assets against bad actors attack. This is a vast field which starts by identifying the risk in your industry and mitigating these risks on the best of your ability. There is always the probability that a bad actor will penetrate your defense system, in that case you should have in place a response plan. Are your digital assets protected?

Use case
Managed Firewall für ein öffentliches Unternehmen – NIS2-Compliance gewährleistet
Public Sector
Herausforderung: Ein öffentliches Versorgungsunternehmen steht vor der Aufgabe, seine IT-Infrastruktur gegen wachsende Cyberbedrohungen abzusichern und gleichzeitig die Vorgaben der NIS-Richtlinie (Network and Information Security) zu erfüllen. Die internen IT-Ressourcen reichen nicht aus, um die Anforderungen an kontinuierliche Überwachung, Aktualisierungen und Protokollierung zu bewältigen. Lösung: Mit der Managed Firewall von bytehaus wird die Sicherheitsinfrastruktur des Unternehmens auf den neuesten Stand gebracht. Bytehaus analysiert die Netzwerkarchitektur und implementiert eine maßgeschneiderte Firewall-Lösung, die den strengen Anforderungen der NIS-Richtlinie entspricht.

Use case
Managed Firewall für ein Unternehmen mit 10 Mitarbeitern – Prävention nach früherem Hackerangriff
Supplier
Herausforderung: Ein mittelständisches Unternehmen mit 10 Mitarbeitern wurde vor einigen Jahren Opfer eines Hackerangriffs, bei dem sensible Daten gestohlen und der Betrieb erheblich beeinträchtigt wurden. Seitdem besteht ein hohes Sicherheitsbewusstsein, jedoch fehlen die internen Ressourcen, um die IT-Sicherheit auf dem aktuellen Stand zu halten und neue Bedrohungen abzuwehren. Lösung: Mit der Managed Firewall von Bytehaus erhält das Unternehmen eine umfassende Sicherheitslösung, die speziell auf kleine Unternehmen mit begrenzten IT-Ressourcen zugeschnitten ist. Bytehaus übernimmt die Implementierung, Verwaltung und Überwachung der Firewall, sodass das Unternehmen vor zukünftigen Angriffen optimal geschützt ist.

Use case
Protecting Critical Infrastructure from Cyber Threats
KRITIS, Critical Infrastructure, Industries with Sensitive Data, Healthcare, Energy, Gov, Supplier
Operators of critical infrastructure such as energy, water, transportation, and healthcare are prime targets for cyberattacks. Many industrial control systems (ICS) and SCADA environments sometimes rely software that is difficult to patch, while strict regulatory requirements like NIS2 and BSI-KritisV demand enhanced security measures. Labyrinth uses specialized SCADA and OT decoys to simulate real industrial control systems, misleading attackers and capturing their activity without impacting operational performance. This ensures early threat detection, supports regulatory compliance with detailed forensic reporting, and protects against APTs and ransomware targeting critical systems.

Use case
Protecting SMEs Against Targeted Cyber Attacks
SME, all
Small and medium-sized enterprises (SMEs) often have limited IT resources and no dedicated Security Operations Center (SOC). They are particularly vulnerable to ransomware, phishing attacks, and data theft as traditional security systems like firewalls or antivirus software fail to counter modern threats. Labyrinth provides an easy-to-implement and cost-efficient deception technology that lures attackers into simulated IT environments, enabling threat detection up to 12 times faster before real damage occurs. This proactive approach reduces false positives, minimizes downtime, and ensures effective cybersecurity without requiring additional IT staff or high costs.

Use case
Reducing SOC Workload in Large Enterprises
Enterprise, all
Security teams in large enterprises face an overwhelming number of security alerts, including many false positives, making it difficult to detect and respond to advanced persistent threats (APTs). Labyrinth deploys highly realistic decoys within corporate networks, attracting and identifying attackers before they can infiltrate critical systems. By providing detailed forensic insights and attack timelines, Labyrinth helps SOC teams focus on real threats, reduces alert fatigue, and seamlessly integrates with existing SIEM, EDR, and firewall solutions for automated defense.

Use case
Cybersecurity
All
Cybersecurity is the act of protecting your digital assets against bad actors attack. This is a vast field which starts by identifying the risk in your industry and mitigating these risks on the best of your ability. There is always the probability that a bad actor will penetrate your defense system, in that case you should have in place a response plan. Are your digital assets protected?
When exploring the Cyber Security industry in the United States, several key factors warrant consideration. The regulatory environment is crucial, as compliance with laws such as the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA) shapes operational standards. Understanding industry-specific regulations can help in assessing a company's credibility and service offerings. The evolving nature of cyber threats also presents significant challenges, with companies needing to adapt continually to emerging vulnerabilities and sophisticated attacks. Opportunities abound in this sector, driven by an increasing demand for robust security solutions across various industries, including finance, healthcare, and government. Companies that invest in advanced technologies like artificial intelligence and machine learning can gain a competitive edge. The environmental impact of technology deployment is another consideration, as sustainable practices become more important in corporate strategies. The competitive landscape is dense, with numerous players ranging from startups to established firms, making differentiation key. Additionally, the global relevance of the U.S. Cyber Security market cannot be overstated, as American firms often lead innovations that influence worldwide trends. Therefore, a thorough understanding of these factors will provide valuable insights for anyone interested in pursuing a career or investment in this dynamic field.
Some interesting numbers and facts about your company results for Cyber Security
| Country with most fitting companies | United States |
| Amount of fitting manufacturers | 3789 |
| Amount of suitable service providers | 4587 |
| Average amount of employees | 11-50 |
| Oldest suiting company | 1993 |
| Youngest suiting company | 2021 |
Some interesting questions that has been asked about the results you have just received for Cyber Security
What are related technologies to Cyber Security?
Based on our calculations related technologies to Cyber Security are Space Technologies, Military, Commercial Aviation, Airport Security
Who are Start-Ups in the field of Cyber Security?
Start-Ups who are working in Cyber Security are SEPNIX
Which industries are mostly working on Cyber Security?
The most represented industries which are working in Cyber Security are IT, Software and Services, Other, Defense, Telecommunications, Consulting
How does ensun find these Cyber Security Companies?
ensun uses an advanced search and ranking system capable of sifting through millions of companies and hundreds of millions of products and services to identify suitable matches. This is achieved by leveraging cutting-edge technologies, including Artificial Intelligence.