
The B2B platform for the best purchasing descision. Identify and compare relevant B2B manufacturers, suppliers and retailers
Close
Filter
Result configuration
Continents
Select continent
Locations
Result types
Company type
Select company type
Industries
Select industry
Company status
Select company status preset
Number of employees
Min.
Max.
Founding year
Cyber Legion Ltd
London, United Kingdom
A
1-10 Employees
2021
Key takeaway
Cyber Legion Ltd is a UK-EU-based cybersecurity company that specializes in advanced cybersecurity testing and consultancy services, particularly for remote work environments and product security. They are a CREST Approved organization for Penetration Testing Services, emphasizing the importance of enhancing cyber resilience and safeguarding digital assets.
Reference
Service
Security Consultant
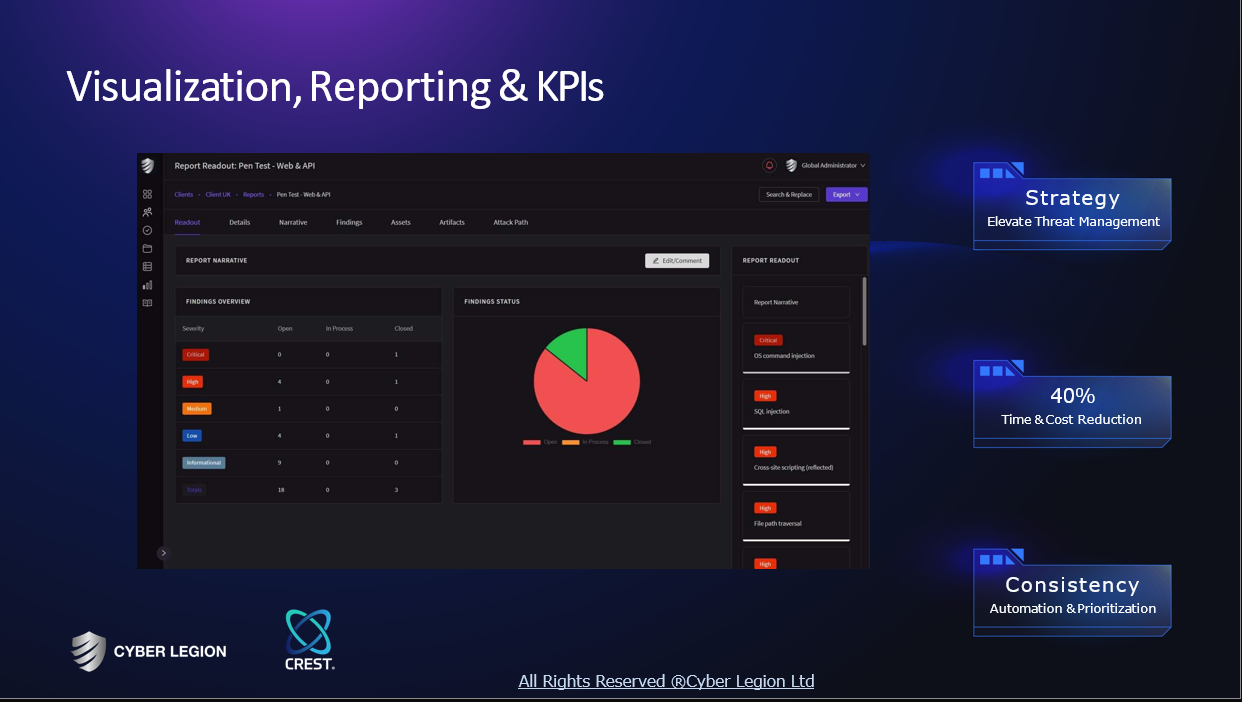
At Cyber Legion, we are dedicated to providing top-notch cybersecurity consultancy to protect your business from evolving threats. Our offerings include a meticulous gap analysis and remediation strategy development, aimed at uncovering vulnerabilities and forging robust plans to mitigate them. Leveraging OSINT (Open Source Intelligence) and cutting-edge threat intelligence, we empower your organization to preemptively neutralize potential security threats. Moreover, we specialize in the formulation of Key Performance Indicators (KPIs) and deliver detailed reporting on your security infrastructure's efficacy. This enables you to monitor your cybersecurity posture's evolution and identify key areas for ongoing improvement. At Cyber Legion, we are dedicated to providing top-notch cybersecurity consultancy to protect your business from evolving threats. Our team of experts will work closely with you to develop a tailored security strategy that meets your specific needs. Contact us today for a free consultation! Staying ahead in security challenges and Get in Touch with Cyber Legion or Get a Free Quote

Cyber Security Defence Ltd
City of Edinburgh, United Kingdom
A
1-10 Employees
-
Key takeaway
Cyber Security Defence Ltd offers innovative products that enhance endpoint security, effectively preventing phishing, blocking malware, and eliminating Zero Day threats. Their solutions include endpoint protection and antivirus.
Reference
Core business
Cyber Security Defence - Endpoint Protection, Anti Virus
Cyber Security Defence Ltd brings new innovative products for greater endpoint security.
C Company
Melbourne, Australia
A
1-10 Employees
2023
Key takeaway
The company specializes in cybersecurity, offering comprehensive solutions to protect and secure digital assets for businesses. Their mission is to empower organizations to navigate the digital world confidently through exceptional cyber defense strategies.
Reference
Core business
Cyber Company
Looking for more accurate results?
Find the right companies for free by entering your custom query!
25M+ companies
250M+ products
Free to use
Atlantic Data Security
East Hartford, United States
B
11-50 Employees
1993
Key takeaway
With over 30 years of experience in the cybersecurity industry, the company offers a comprehensive range of services and expertise to enhance an organization's security infrastructure. Their skilled team adapts and customizes solutions to meet the evolving cybersecurity needs of clients, ensuring robust protection of digital assets.
Reference
Core business
The Premier Cybersecurity Solutions Provider
CyberSecOn
Melbourne, Australia
A
11-50 Employees
2016
Key takeaway
CyberSecOn is a trusted team of professionals in Australia that provides robust and cutting-edge cyber security solutions for enterprises, including network, application, and data security. With a proven track record and strong customer relationships, they aim to revolutionize information security and ensure compliance through a broad range of security services.
Reference
Core business
Company – CyberSecOn
CyberSecthreat Corporation Limited.
Taipei, Taiwan
1-10 Employees
2021
Key takeaway
CyberSecThreat is a prominent cybersecurity solutions provider that offers advanced services such as Cyber Threat Intelligence, Security Orchestration, and incident response enhancement. With a commitment to improving cybersecurity postures, they specialize in security assessments and penetration testing, making them a key player in the cybersecurity landscape.
Reference
Core business
Home - CyberSecThreat
cybersecurity solutions A safe digital life featured NEWS Swimlane CXO Round Table Event – 12 Jul 2023 CyberSecThreat to Launch Patented Solutions
Insyghts Security Pte Ltd
Singapore
C
1-10 Employees
2017
Key takeaway
Insyghts Security is a comprehensive cybersecurity service provider that offers expertise in governance, engineering, and managed risk operations. With over 25 years of experience, they help organizations enhance their security posture by providing ongoing visibility into threats and vulnerabilities.
Reference
Core business
Insyghts Security – Cybersecurity Service Provider
CYBER BUYER
Charlotte, United States
B
1-10 Employees
2018
Key takeaway
CYBER BUYER is dedicated to assisting CISOs and cyber security leaders in procuring and implementing innovative Cloud and SaaS Cyber Security solutions. With a vast selection of over 200 Independent Software Vendor solutions, they focus on helping businesses enhance their cyber security posture through effective technology investments and managed security services.
Reference
Core business
CYBER BUYER | Cyber Security Software Outfitters and Marketplace | CYBER BUYER LLC
With CYBER BUYER, we help you focus your efforts on effective investments in new cyber security technologies that Stop More Attacks, Find Breaches Faster, Fix Breaches Faster and Lower Breach Impact.

ActiSoft Technology Limited
London, United Kingdom
A
1-10 Employees
2017
Key takeaway
The company offers a proactive, risk-based approach to cyber security, providing cost-effective solutions tailored for SMEs. By partnering with leading vendors, they ensure access to the best cyber security products, helping businesses address security gaps and stay ahead of evolving threats.
Reference
Core business
Cybersecurity Software & Services | 0203 931 0199
Managed Cyber Security Services for SME’s. Individual products to fix security gaps to complete solutions. Leverage Next-Generation Technology to protect your organisation and stay operational.
CyberSoft
Conshohocken, United States
B
11-50 Employees
1988
Key takeaway
CyberSoft Operating Corporation specializes in cybersecurity software, offering comprehensive anti-virus and malware protection for UNIX and Linux servers. Their commitment to research and development ensures they stay ahead of current and future threats, making them a key player in safeguarding critical systems.
Reference
Core business
CyberSoft | Makers of Linux and UNIX Computer Security Products
Technologies which have been searched by others and may be interesting for you:
A selection of suitable products and services provided by verified companies according to your search.
Service
Product Security
Go to product

Product
DigiCert EV Code Signing
Go to product

Product
enclaive vHSM
Go to product

Service
EMCP
Go to product
A selection of suitable use cases for products or services provided by verified companies according to your search.
Use case
Penetration Testing for a fintech customer
fintech
A fintech customer leverages PentestLive to proactively identify and manage security vulnerabilities across web apps, APIs, and mobile platforms. Real-time updates from Bluefire Redteam experts ensure rapid remediation and risk prioritization. Trusted by global fintech leaders, PentestLive safeguards sensitive financial data.

Use case
Penetration Testing for a fintech customer
fintech
A fintech customer leverages PentestLive to proactively identify and manage security vulnerabilities across web apps, APIs, and mobile platforms. Real-time updates from Bluefire Redteam experts ensure rapid remediation and risk prioritization. Trusted by global fintech leaders, PentestLive safeguards sensitive financial data.
Cyber security software is designed to protect systems, networks, and data from digital attacks, theft, and damage. It encompasses a range of tools and applications that help organizations safeguard their information assets against threats such as malware, phishing, and unauthorized access. This software typically includes features like firewalls, antivirus programs, intrusion detection systems, and encryption technologies. By implementing cyber security software, businesses can enhance their security posture, ensuring that sensitive information remains confidential and secure from potential breaches.
Cyber security software serves as a vital defense mechanism against various digital threats by employing multiple layers of protection. It utilizes technologies like antivirus, firewalls, intrusion detection systems, and encryption to secure sensitive data and systems. By continuously monitoring networks for suspicious activities, it can detect unauthorized access or malware attempts in real-time, allowing for immediate response and mitigation. Additionally, this software often includes features such as threat intelligence, which analyzes and predicts potential cyber threats based on emerging trends. Regular updates ensure that the software is equipped with the latest security protocols to combat new vulnerabilities. Overall, cyber security software plays a crucial role in safeguarding organizations from evolving cyber threats while maintaining the integrity and confidentiality of their data.
When selecting cyber security software, several features are essential for effective protection. One critical aspect is real-time threat detection, which allows the software to continuously monitor and identify potential threats as they arise. This capability is vital for minimizing damage from attacks. Additionally, user-friendly interface is important; it ensures that even non-technical users can navigate and manage the software efficiently. Integration capabilities with existing systems and applications also play a significant role, as seamless compatibility enhances overall security management. Lastly, regular updates and support from the provider are crucial for keeping the software effective against emerging threats.
Cyber Security Software is designed to seamlessly integrate with existing systems to enhance overall security without disrupting operations. This integration involves utilizing APIs and standard protocols that allow the software to communicate effectively with current IT infrastructure, such as servers, networks, and endpoints. Furthermore, many solutions offer customizable settings that enable them to adapt to various environments, ensuring compatibility with legacy systems and cloud-based services. The result is a comprehensive security posture that protects data and applications while maintaining workflow efficiency.
1. Threat Protection
Cyber security software provides robust protection against various threats such as malware, ransomware, and phishing attacks. By employing advanced algorithms and real-time monitoring, these solutions help businesses detect and neutralize threats before they can cause significant damage.
2. Data Security
Implementing cyber security software enhances data security through encryption, access controls, and secure data storage. This ensures sensitive business information remains protected from unauthorized access, which is crucial for maintaining customer trust and compliance with data protection regulations.
Some interesting numbers and facts about your company results for Cyber Security Software
| Country with most fitting companies | United States |
| Amount of fitting manufacturers | 10000 |
| Amount of suitable service providers | 10000 |
| Average amount of employees | 1-10 |
| Oldest suiting company | 1988 |
| Youngest suiting company | 2023 |
20%
40%
60%
80%
Some interesting questions that has been asked about the results you have just received for Cyber Security Software
What are related technologies to Cyber Security Software?
Based on our calculations related technologies to Cyber Security Software are Big Data, E-Health, Retail Tech, Artificial Intelligence & Machine Learning, E-Commerce
Who are Start-Ups in the field of Cyber Security Software?
Start-Ups who are working in Cyber Security Software are Cyber Legion Ltd, C Company, CyberSecthreat Corporation Limited.
Which industries are mostly working on Cyber Security Software?
The most represented industries which are working in Cyber Security Software are IT, Software and Services, Defense, Other, Telecommunications, Consulting
How does ensun find these Cyber Security Software Companies?
ensun uses an advanced search and ranking system capable of sifting through millions of companies and hundreds of millions of products and services to identify suitable matches. This is achieved by leveraging cutting-edge technologies, including Artificial Intelligence.