
The B2B platform for the best purchasing descision. Identify and compare relevant B2B manufacturers, suppliers and retailers
Close
Filter
Result configuration
Continents
Select continent
Locations
Result types
Company type
Select company type
Industries
Select industry
Company status
Select company status preset
Number of employees
Min.
Max.
Founding year
Insystech Inc
Chantilly, United States
B
11-50 Employees
1997
Key takeaway
Insystech, Inc. is an information technology service provider that emphasizes its expertise in cyber security, aligning with the growing demand for high-quality IT services. Their commitment to understanding client needs and delivering effective solutions positions them as a reliable partner in the cyber security domain.
Reference
Service
Cyber Security - Information technology service provider
Cyber Legion Ltd
London, United Kingdom
A
1-10 Employees
2021
Key takeaway
Cyber Legion Ltd is a UK-EU-based cybersecurity company that specializes in advanced cybersecurity testing and consultancy services, particularly for remote work environments and product security. As a CREST Approved organization, they offer comprehensive penetration testing services and resources for enhancing cybersecurity knowledge.
Reference
Service
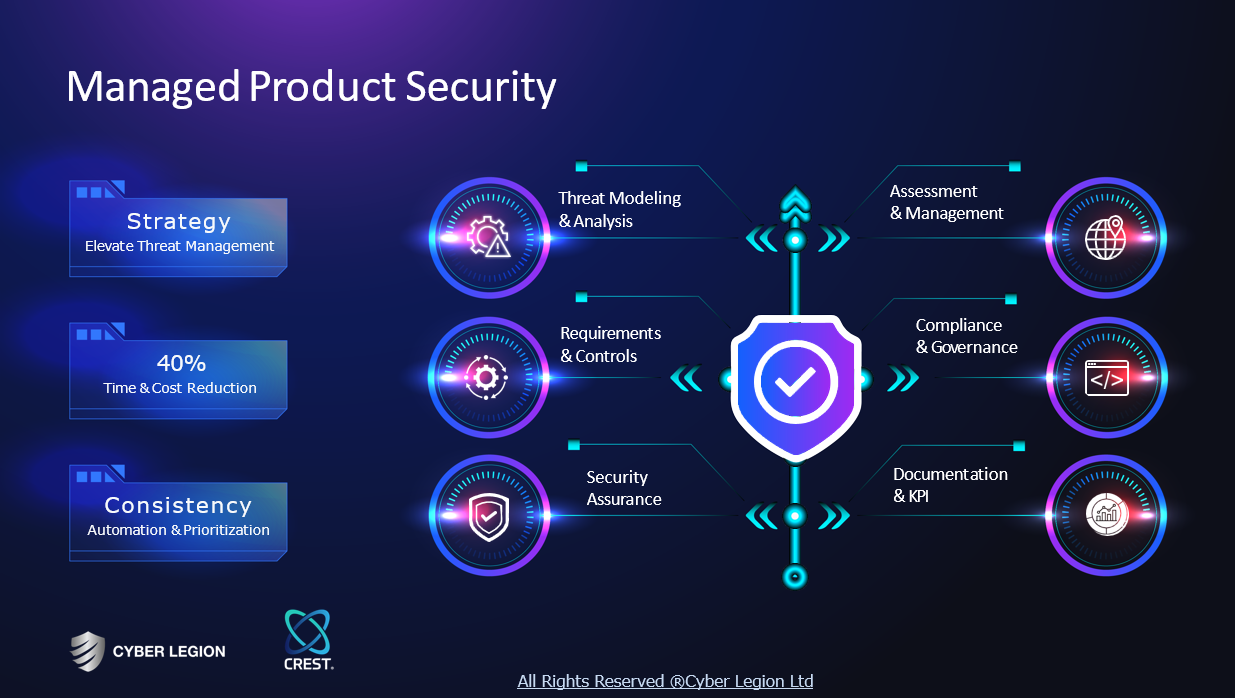
Security Consultant
At Cyber Legion, we are dedicated to providing top-notch cybersecurity consultancy to protect your business from evolving threats. Our offerings include a meticulous gap analysis and remediation strategy development, aimed at uncovering vulnerabilities and forging robust plans to mitigate them. Leveraging OSINT (Open Source Intelligence) and cutting-edge threat intelligence, we empower your organization to preemptively neutralize potential security threats. Moreover, we specialize in the formulation of Key Performance Indicators (KPIs) and deliver detailed reporting on your security infrastructure's efficacy. This enables you to monitor your cybersecurity posture's evolution and identify key areas for ongoing improvement. At Cyber Legion, we are dedicated to providing top-notch cybersecurity consultancy to protect your business from evolving threats. Our team of experts will work closely with you to develop a tailored security strategy that meets your specific needs. Contact us today for a free consultation! Staying ahead in security challenges and Get in Touch with Cyber Legion or Get a Free Quote

NASHVILLE IT HEALTH INC.
Brentwood, United States
B
1-10 Employees
2008
Key takeaway
The company specializes in providing robust cyber security solutions that safeguard IT infrastructures against emerging threats.
Reference
Core business
IT Managed Services and Cybersecurity Solutions
Looking for more accurate results?
Find the right companies for free by entering your custom query!
25M+ companies
250M+ products
Free to use
Cyber Protect LLC
United States
B
1-10 Employees
2019
Key takeaway
Cyber Protect LLC is a leading managed IT solutions provider in Michigan, offering exceptional cybersecurity services tailored to businesses of all sizes. Their dedicated team of security experts works to create customized security strategies, ensuring clients have control over their cybersecurity infrastructure for peace of mind.
Reference
Core business
Home of the Cybersecurity Specialist - Cyber Protect LLC
Cybersecurity simplified. We provide smart solutions for companies of all sizes and pride ourselves on our unparalleled, dedicated service. GET A FREE QUOTE
Insyghts Security Pte Ltd
Singapore
C
1-10 Employees
2017
Key takeaway
Insyghts Security is a comprehensive cybersecurity service provider that helps organizations enhance their cybersecurity governance and manage risks and threats. With over 25 years of experience, they offer ongoing visibility into vulnerabilities and security operations, making them well-equipped to assist companies in securing their critical assets.
Reference
Core business
Insyghts Security – Cybersecurity Service Provider
All Secure IT Services
Sydney, Australia
A
1-10 Employees
2017
Key takeaway
All Secure IT Services focuses on delivering quality IT managed services that protect businesses from cyber threats and potential revenue loss. They offer penetration testing and remediation, emphasizing their commitment to enhancing cyber security.
Reference
Service
Cyber Insurance - All Secure IT Services
IT Bus
West Oxfordshire, United Kingdom
A
11-50 Employees
2008
Key takeaway
ITB is a leading supplier of cybersecurity solutions and services, offering a comprehensive range of products designed to protect against cyber threats and secure organizational networks and data. Their expert team supports clients throughout their security journey, providing customized solutions that encompass all aspects of IT security, including endpoint security, cloud security, and risk management.
Reference
Product
Cyber Solutions - ITB Cyber Solutions
Here at ITB we offer the very best cyber security solutions to ensure your organisation is fully protected. We cover all aspects of IT security, from security operations to endpoint security. Not only do we help arm your IT infrastructure with world-leading cyber security, but we continuously develop to ensure the safety of your organisational […]
Agincourt Partners Ltd t/a Cybersec Solutions
United Kingdom
A
1-10 Employees
2015
Key takeaway
Cybersec offers comprehensive and tailored security solutions to protect organizations from cyber threats, including zero trust networking and a managed security awareness program. Their services aim to reduce risk and prevent data breaches, ensuring businesses receive the right level of protection to meet their specific needs.
Reference
Service
Cybersecurity Services – Cybersec Solutions
Protecture Technology
United Kingdom
A
11-50 Employees
2013
Key takeaway
The company emphasizes its expertise in Cyber Security and Data Security, highlighting the need to integrate both for effective protection. They assist clients, particularly in sectors like Charity, Education, Hospitality, and legal, in navigating the challenges and opportunities of digital transformation related to Cyber Security.
Reference
Service
Cyber Security - Protecture
TechZone Networking Services LLC
Dubai, United Arab Emirates
C
51-100 Employees
2001
Key takeaway
The company specializes in cyber security services, emphasizing its expertise in critical aspects of information technology.
Reference
Service
Cyber Security Services
Technologies which have been searched by others and may be interesting for you:
A selection of suitable products and services provided by verified companies according to your search.

Service
Cybersecurity
Go to product

Service
Penetration Testing
Go to product
Service
Security Consultant
Go to product
Service
Product Security
Go to product
A selection of suitable use cases for products or services provided by verified companies according to your search.

Use case
Cybersecurity
All
Cybersecurity is the act of protecting your digital assets against bad actors attack. This is a vast field which starts by identifying the risk in your industry and mitigating these risks on the best of your ability. There is always the probability that a bad actor will penetrate your defense system, in that case you should have in place a response plan. Are your digital assets protected?

Use case
Managed Firewall für ein öffentliches Unternehmen – NIS2-Compliance gewährleistet
Public Sector
Herausforderung: Ein öffentliches Versorgungsunternehmen steht vor der Aufgabe, seine IT-Infrastruktur gegen wachsende Cyberbedrohungen abzusichern und gleichzeitig die Vorgaben der NIS-Richtlinie (Network and Information Security) zu erfüllen. Die internen IT-Ressourcen reichen nicht aus, um die Anforderungen an kontinuierliche Überwachung, Aktualisierungen und Protokollierung zu bewältigen. Lösung: Mit der Managed Firewall von bytehaus wird die Sicherheitsinfrastruktur des Unternehmens auf den neuesten Stand gebracht. Bytehaus analysiert die Netzwerkarchitektur und implementiert eine maßgeschneiderte Firewall-Lösung, die den strengen Anforderungen der NIS-Richtlinie entspricht.

Use case
Managed Firewall für ein Unternehmen mit 10 Mitarbeitern – Prävention nach früherem Hackerangriff
Supplier
Herausforderung: Ein mittelständisches Unternehmen mit 10 Mitarbeitern wurde vor einigen Jahren Opfer eines Hackerangriffs, bei dem sensible Daten gestohlen und der Betrieb erheblich beeinträchtigt wurden. Seitdem besteht ein hohes Sicherheitsbewusstsein, jedoch fehlen die internen Ressourcen, um die IT-Sicherheit auf dem aktuellen Stand zu halten und neue Bedrohungen abzuwehren. Lösung: Mit der Managed Firewall von Bytehaus erhält das Unternehmen eine umfassende Sicherheitslösung, die speziell auf kleine Unternehmen mit begrenzten IT-Ressourcen zugeschnitten ist. Bytehaus übernimmt die Implementierung, Verwaltung und Überwachung der Firewall, sodass das Unternehmen vor zukünftigen Angriffen optimal geschützt ist.

Use case
Cybersecurity
All
Cybersecurity is the act of protecting your digital assets against bad actors attack. This is a vast field which starts by identifying the risk in your industry and mitigating these risks on the best of your ability. There is always the probability that a bad actor will penetrate your defense system, in that case you should have in place a response plan. Are your digital assets protected?
Cyber security IT involves the practices, technologies, and processes designed to protect computer systems, networks, and data from cyber threats. It encompasses a wide range of security measures including firewalls, intrusion detection systems, and encryption protocols, which work together to safeguard sensitive information from unauthorized access, cyberattacks, and data breaches. Organizations rely on cyber security IT to mitigate risks and ensure the confidentiality, integrity, and availability of their digital assets. By implementing comprehensive security strategies, businesses can defend against evolving threats and maintain trust with customers and stakeholders.
Cyber Security IT employs a variety of strategies to safeguard against data breaches. Implementing robust firewall systems acts as the first line of defense, filtering incoming and outgoing traffic based on predetermined security rules. Additionally, these providers utilize advanced encryption techniques to protect sensitive data both at rest and in transit, making it inaccessible to unauthorized users. Regular security assessments and penetration testing are conducted to identify vulnerabilities within systems. Furthermore, Cyber Security IT specialists continuously monitor network activity for unusual behavior, enabling swift response to potential threats. By combining these practices with employee training on security protocols, organizations can significantly reduce the risk of data breaches.
Cyber Security IT is crucial for businesses as it protects sensitive information from cyber threats. With the increasing frequency and sophistication of cyberattacks, organizations face risks that can lead to data breaches, financial losses, and reputational damage. Implementing robust cyber security measures safeguards critical data, ensuring compliance with regulations and maintaining customer trust. Additionally, effective cyber security practices help in identifying vulnerabilities within systems, allowing businesses to proactively address potential weaknesses. This not only enhances the overall security posture but also fosters a culture of safety and awareness among employees, which is essential in today's digital landscape.
1. Risk Assessment
A thorough risk assessment is essential for identifying vulnerabilities within an organization’s IT infrastructure. This involves evaluating potential threats, the likelihood of their occurrence, and the impact they could have on operations.
2. Security Policies and Procedures
Developing comprehensive security policies and procedures is vital. These documents outline the protocols for data protection, access controls, and incident response, ensuring that all employees understand their roles in maintaining security.
3. Employee Training and Awareness
Regular training and awareness programs help employees recognize cyber threats such as phishing and social engineering attacks. This component ensures that everyone in the organization is equipped to follow best practices and respond appropriately to potential security incidents.
4. Incident Response Plan
An effective incident response plan outlines the steps to take in the event of a security breach. This includes identifying the breach, containing the damage, eradicating the threat, and recovering systems, which helps minimize downtime and data loss.
5. Regular Security Audits
Conducting regular security audits is crucial for assessing the effectiveness of the current cyber security measures. These audits help identify gaps and weaknesses, allowing organizations to adjust their strategies accordingly.
6. Technology Solutions
Implementing advanced technology solutions, such as firewalls, intrusion detection systems, and encryption, enhances the overall security posture. These tools work together to protect sensitive data and prevent unauthorized access.
7. Compliance and Regulations
Staying compliant with industry regulations and standards is a key component. This ensures that the organization adheres to legal requirements regarding data protection and privacy, reducing the risk of legal repercussions.
Identifying and mitigating cyber security IT threats involves a multifaceted approach. Regularly conducting security assessments helps organizations pinpoint vulnerabilities within their systems. These assessments can include penetration testing, vulnerability scanning, and risk analysis, which collectively reveal potential entry points for cyber attacks. To effectively mitigate these threats, implementing comprehensive security protocols is essential. This includes deploying firewalls, intrusion detection systems, and encryption technologies to safeguard sensitive data. Additionally, ongoing employee training on recognizing phishing attempts and practicing safe online behavior significantly reduces the risk of human error, which is often a key factor in cyber security breaches. Regular updates and patches to software and systems also play a crucial role in protecting against known vulnerabilities.
Some interesting numbers and facts about your company results for Cyber Security IT
| Country with most fitting companies | United States |
| Amount of fitting manufacturers | 10000 |
| Amount of suitable service providers | 10000 |
| Average amount of employees | 1-10 |
| Oldest suiting company | 1997 |
| Youngest suiting company | 2021 |
20%
40%
60%
80%
Some interesting questions that has been asked about the results you have just received for Cyber Security IT
What are related technologies to Cyber Security IT?
Based on our calculations related technologies to Cyber Security IT are Big Data, E-Health, Retail Tech, Artificial Intelligence & Machine Learning, E-Commerce
Who are Start-Ups in the field of Cyber Security IT?
Start-Ups who are working in Cyber Security IT are Cyber Legion Ltd
Which industries are mostly working on Cyber Security IT?
The most represented industries which are working in Cyber Security IT are IT, Software and Services, Other, Defense, Telecommunications, Consulting
How does ensun find these Cyber Security IT Companies?
ensun uses an advanced search and ranking system capable of sifting through millions of companies and hundreds of millions of products and services to identify suitable matches. This is achieved by leveraging cutting-edge technologies, including Artificial Intelligence.