
The B2B platform for the best purchasing descision. Identify and compare relevant B2B manufacturers, suppliers and retailers
Close
Filter
Result configuration
Continents
Select continent
Locations
Result types
Company type
Select company type
Industries
Select industry
Company status
Select company status preset
Number of employees
Min.
Max.
Founding year
Insystech Inc
Chantilly, United States
B
11-50 Employees
1997
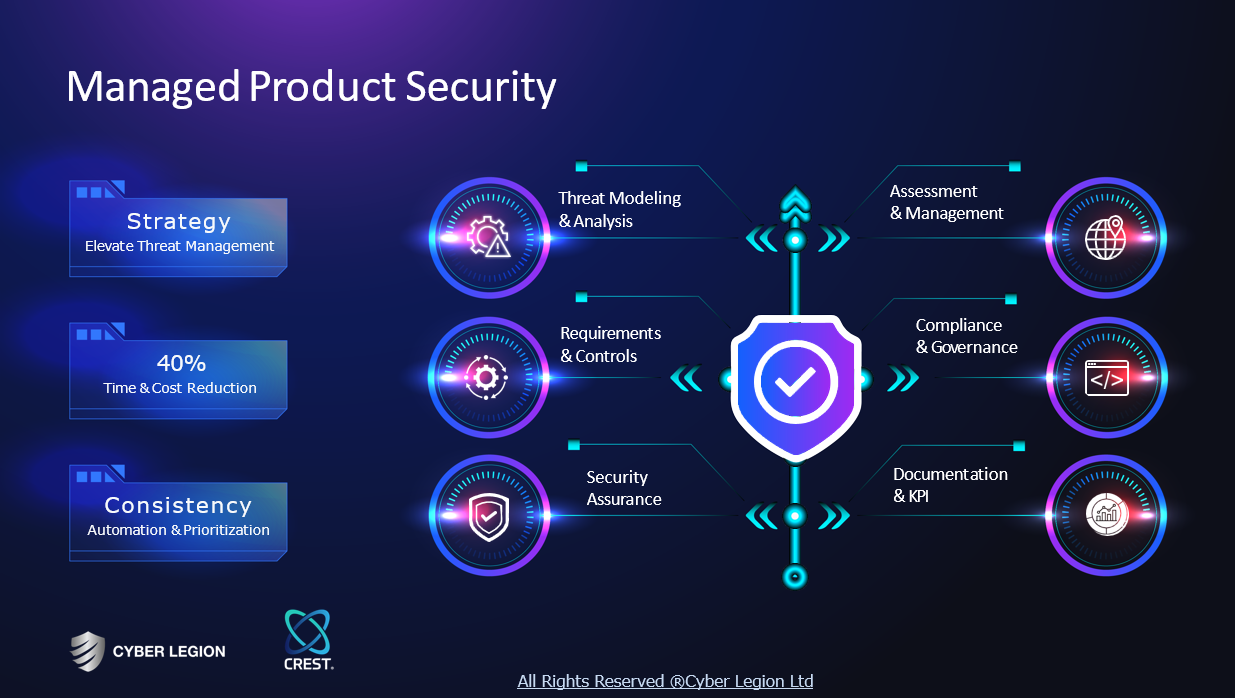
Key takeaway
Insystech, Inc. is an information technology service provider that emphasizes its expertise in cyber security, aligning with the growing demand for high-quality IT services. Their commitment to understanding client needs and delivering effective solutions positions them as a reliable partner in the cyber security domain.
Reference
Service
Cyber Security - Information technology service provider

NASHVILLE IT HEALTH INC.
Brentwood, United States
B
1-10 Employees
2008
Key takeaway
The company specializes in providing robust cyber security solutions that safeguard IT infrastructures against emerging threats.
Reference
Core business
IT Managed Services and Cybersecurity Solutions
Cyber Protect LLC
United States
B
1-10 Employees
2019
Key takeaway
Cyber Protect LLC is a leading managed IT solutions provider in Michigan, offering exceptional cybersecurity services tailored to businesses of all sizes. Their dedicated team of security experts works to create customized security strategies, ensuring clients have control over their cybersecurity infrastructure for peace of mind.
Reference
Core business
Home of the Cybersecurity Specialist - Cyber Protect LLC
Cybersecurity simplified. We provide smart solutions for companies of all sizes and pride ourselves on our unparalleled, dedicated service. GET A FREE QUOTE
Looking for more accurate results?
Find the right companies for free by entering your custom query!
25M+ companies
250M+ products
Free to use
EK Associates
Cerritos, United States
B
1-10 Employees
2012
Key takeaway
The company specializes in cybersecurity and network security solutions, emphasizing their commitment to maintaining the highest level of security and data integrity in their integrated IT solutions. Their skilled consultants assess clients' needs and provide a broad range of technical options to enhance system efficiency and staff productivity.
Reference
Service
Information Technology and Management Solutions Provider | Cybersecurity and Network Security Solutions
The Network Company
Rancho Santa Margarita, United States
B
1-10 Employees
1989
Key takeaway
The company provides tailored cybersecurity solutions and IT services, ensuring robust protection and streamlined operations for businesses. Their offerings include managed services and co-managed IT support, enhancing efficiency and reducing operational costs.
Reference
Service
Services - The Network Company | Cyber Security | IT Services | Network Security
Magna Cyber
Miramar, United States
B
11-50 Employees
2020
Key takeaway
Magna Cyber specializes in implementing and securing IT and cyber security infrastructures, trusted by government agencies and large corporations. They have expertise in migrating to Palo Alto and Fortinet firewalls, providing robust network security solutions while maintaining high service levels and competitive pricing.
Reference
Core business
Magna Cyber – IT & Cyber Security Services
Atlantic Data Security
East Hartford, United States
B
11-50 Employees
1993
Key takeaway
With over 30 years of experience in the cybersecurity industry, the company offers comprehensive security solutions tailored to meet the evolving needs of clients. Their team of skilled cybersecurity engineers is dedicated to protecting assets and providing access to leading cybersecurity technologies.
Reference
Core business
The Premier Cybersecurity Solutions Provider
Blue Cloak
Sterling, United States
B
11-50 Employees
2015
Key takeaway
Blue Cloak provides comprehensive cybersecurity services, including customizable mobile cyber ranges and innovative training that integrates real and simulated operations. Their skilled IT security experts focus on developing robust cybersecurity policies and enabling thorough analysis and verification of cyber products, which is essential for effective decision-making in the field of cyber security.
Reference
Service
Cybersecurity | Blue Cloak
B Suite Cyber Security
Chicago, United States
B
1-10 Employees
2017
Key takeaway
B Suite Cyber Security IT Company specializes in providing enterprise-grade cyber security solutions tailored for small businesses, focusing on simplifying the complexities of data security and protecting against cyber threats. They offer comprehensive services to minimize cyber risks and close security gaps, ensuring the safety of business assets.
Reference
Core business
Cyber Security | Network Security Services Chicago IL
Cyber security company based in Chicago, IL implementing IT network security services for SMB, healthcare, and enterprise firms nationwide.
AHCTS LLC
Toledo, United States
B
1-10 Employees
2021
Key takeaway
AHCTS, LLC offers comprehensive IT solutions with a strong emphasis on cybersecurity protection, tailoring strategies to meet the unique needs of businesses. Their expert team ensures seamless operations and data integrity, allowing clients to focus on growth while effectively managing complex IT challenges.
Reference
Service
Cybersecurity
AHCTS LLC provides enterprise scalable holistic cybersecurity consulting, management, and professional services custom tailored to your needs. Whether you're looking for comprehensive security, managed solutions, or experiencing a cybersecurity emergency, our team of experts is on standby 24/7 to provide immediate response and remediation services to you and your business, so that you don't need to worry!
Technologies which have been searched by others and may be interesting for you:
A selection of suitable products and services provided by verified companies according to your search.

Service
Cybersecurity
Go to product

Service
Penetration Testing
Go to product
Service
Security Consultant
Go to product
Service
Product Security
Go to product
A selection of suitable use cases for products or services provided by verified companies according to your search.

Use case
Cybersecurity
All
Cybersecurity is the act of protecting your digital assets against bad actors attack. This is a vast field which starts by identifying the risk in your industry and mitigating these risks on the best of your ability. There is always the probability that a bad actor will penetrate your defense system, in that case you should have in place a response plan. Are your digital assets protected?

Use case
Managed Firewall für ein öffentliches Unternehmen – NIS2-Compliance gewährleistet
Public Sector
Herausforderung: Ein öffentliches Versorgungsunternehmen steht vor der Aufgabe, seine IT-Infrastruktur gegen wachsende Cyberbedrohungen abzusichern und gleichzeitig die Vorgaben der NIS-Richtlinie (Network and Information Security) zu erfüllen. Die internen IT-Ressourcen reichen nicht aus, um die Anforderungen an kontinuierliche Überwachung, Aktualisierungen und Protokollierung zu bewältigen. Lösung: Mit der Managed Firewall von bytehaus wird die Sicherheitsinfrastruktur des Unternehmens auf den neuesten Stand gebracht. Bytehaus analysiert die Netzwerkarchitektur und implementiert eine maßgeschneiderte Firewall-Lösung, die den strengen Anforderungen der NIS-Richtlinie entspricht.

Use case
Managed Firewall für ein Unternehmen mit 10 Mitarbeitern – Prävention nach früherem Hackerangriff
Supplier
Herausforderung: Ein mittelständisches Unternehmen mit 10 Mitarbeitern wurde vor einigen Jahren Opfer eines Hackerangriffs, bei dem sensible Daten gestohlen und der Betrieb erheblich beeinträchtigt wurden. Seitdem besteht ein hohes Sicherheitsbewusstsein, jedoch fehlen die internen Ressourcen, um die IT-Sicherheit auf dem aktuellen Stand zu halten und neue Bedrohungen abzuwehren. Lösung: Mit der Managed Firewall von Bytehaus erhält das Unternehmen eine umfassende Sicherheitslösung, die speziell auf kleine Unternehmen mit begrenzten IT-Ressourcen zugeschnitten ist. Bytehaus übernimmt die Implementierung, Verwaltung und Überwachung der Firewall, sodass das Unternehmen vor zukünftigen Angriffen optimal geschützt ist.

Use case
Cybersecurity
All
Cybersecurity is the act of protecting your digital assets against bad actors attack. This is a vast field which starts by identifying the risk in your industry and mitigating these risks on the best of your ability. There is always the probability that a bad actor will penetrate your defense system, in that case you should have in place a response plan. Are your digital assets protected?
When exploring the Cyber Security IT industry in the United States, several key considerations are important. First, understanding the regulatory environment is crucial, as compliance with standards such as the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA) can significantly impact operations. The rapid evolution of cyber threats presents ongoing challenges, requiring companies to stay ahead of malicious actors through innovation and advanced technologies. Opportunities abound in this growing sector, driven by increasing demand for robust cybersecurity solutions across various industries, including finance, healthcare, and government. The competitive landscape is characterized by both established firms and start-ups, fostering innovation but also necessitating differentiation to capture market share. Additionally, awareness of global market relevance is essential, as cybersecurity concerns are not confined to national borders; international collaboration and understanding of foreign regulations can enhance a company's effectiveness. Environmental concerns, while not the primary focus of the industry, are gaining attention as companies adopt sustainable practices in their operations. Overall, potential entrants should prioritize ongoing education and training to keep pace with the dynamic nature of cyber threats and the technologies designed to combat them. This holistic approach will enable informed decision-making and strategic positioning within the Cyber Security IT landscape.
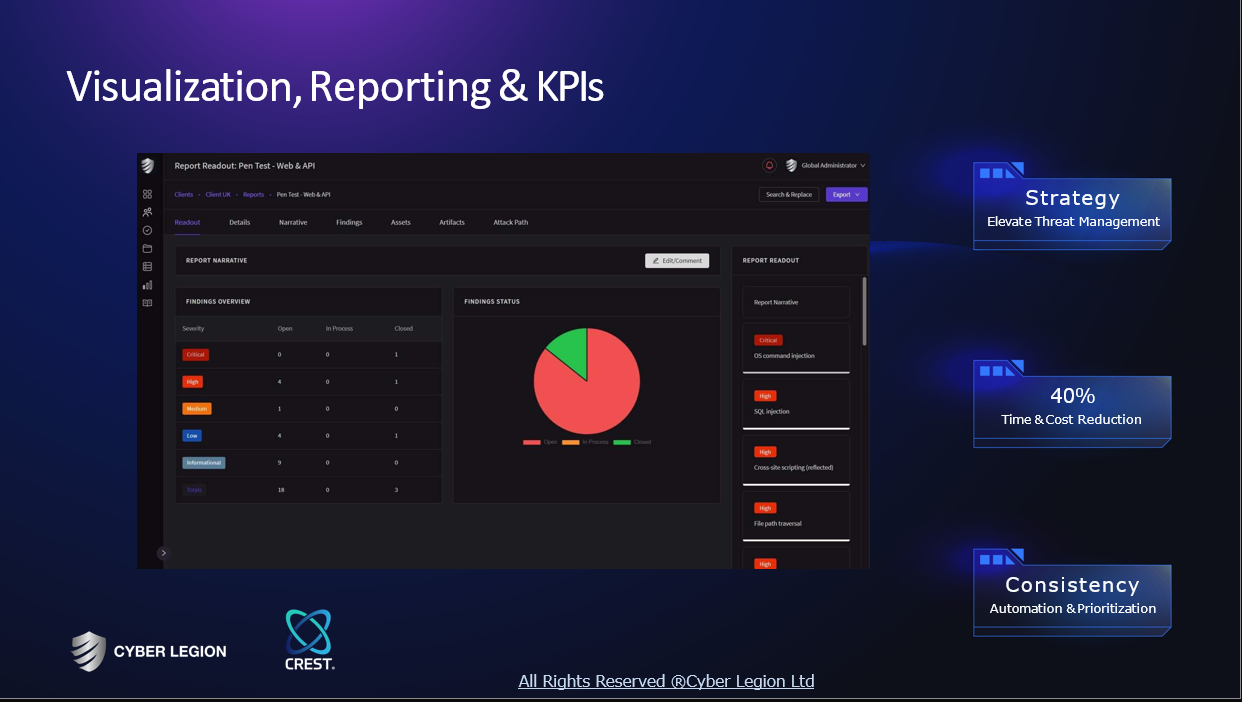
Some interesting numbers and facts about your company results for Cyber Security IT
| Country with most fitting companies | United States |
| Amount of fitting manufacturers | 5247 |
| Amount of suitable service providers | 7042 |
| Average amount of employees | 1-10 |
| Oldest suiting company | 1989 |
| Youngest suiting company | 2021 |
Some interesting questions that has been asked about the results you have just received for Cyber Security IT
What are related technologies to Cyber Security IT?
Based on our calculations related technologies to Cyber Security IT are Big Data, E-Health, Retail Tech, Artificial Intelligence & Machine Learning, E-Commerce
Who are Start-Ups in the field of Cyber Security IT?
Start-Ups who are working in Cyber Security IT are AHCTS LLC
Which industries are mostly working on Cyber Security IT?
The most represented industries which are working in Cyber Security IT are IT, Software and Services, Other, Defense, Telecommunications, Consulting
How does ensun find these Cyber Security IT Companies?
ensun uses an advanced search and ranking system capable of sifting through millions of companies and hundreds of millions of products and services to identify suitable matches. This is achieved by leveraging cutting-edge technologies, including Artificial Intelligence.