
The B2B platform for the best purchasing descision. Identify and compare relevant B2B manufacturers, suppliers and retailers
Close
Filter
Result configuration
Continents
Select continent
Locations
Result types
Company type
Select company type
Industries
Select industry
Company status
Select company status preset
Number of employees
Min.
Max.
Founding year
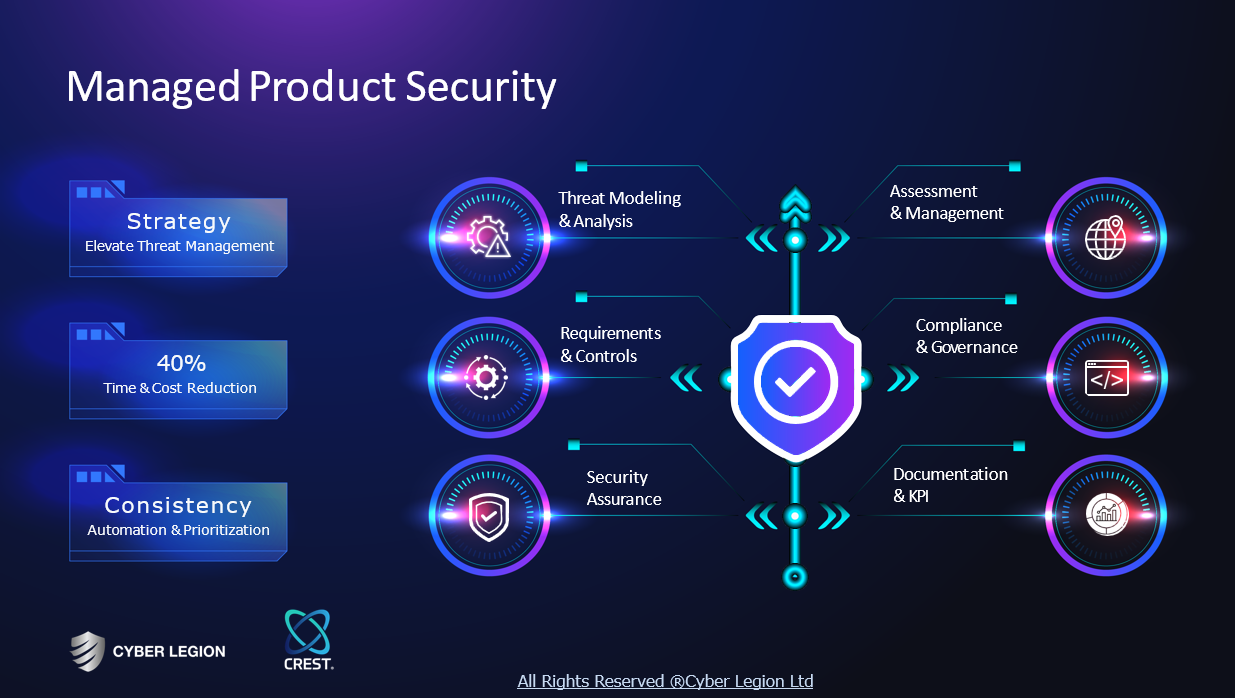
Security Office
Seoul, South Korea
A
1-10 Employees
2014
Key takeaway
Based on the expertise and practical experience of Security Office, they effectively protect clients' information and assets from cyber attacks. With over 30% of the top 100 Nordic companies relying on them for strategic cybersecurity advice, they demonstrate a strong commitment to preventing cyber threats and ensuring a safe digital future.
Reference
Core business
시큐리티 오피스 :: Security Office - Part of Truesec
당신의 안전한 디지털 미래를 위해 노력합니다. 시큐리티 오피스의 축적된 노하우와 실전 경험을 토대로 사이버 공격으로부터 고객의 정보와 자산을 보호하세요.
NORMA Inc.
Seoul, South Korea
A
11-50 Employees
2011
Key takeaway
The company, Norma, specializes in cyber security by providing IoT security solutions and consulting services. They support the establishment of security frameworks and compliance through certifications and penetration testing, while also offering expertise in cloud security certification.
Reference
Product
글로벌 IoT & 양자 보안 전문 기업 - 노르마
IoT 보안 솔루션과 컨설팅 서비스를 제공하는 양자 보안 전문 기업입니다.
Mandiant Korea
Seoul, South Korea
A
11-50 Employees
-
Key takeaway
Mandiant, now part of Google Cloud, specializes in cyber threat intelligence and offers a range of products and services designed to support defenses against cybercrime. Their expertise, combined with innovative tools like Mandiant Breach Analytics for Chronicle, enhances early threat detection and provides valuable insights into current cyber defense challenges.
Reference
Service
Cyber Security Consulting Services | Threat Intelligence_EN
Choose from a full range of Mandiant Cyber Security consulting services that help you respond to and proactively protect against cyber security threats.
Looking for more accurate results?
Find the right companies for free by entering your custom query!
25M+ companies
250M+ products
Free to use
SNTWORKS Inc.
South Korea
A
1-10 Employees
2016
Key takeaway
SNTWorks specializes in cyber security for embedded devices, offering services like reverse engineering and security assessments. With a focus on addressing dynamic security challenges, they provide the tools and expertise necessary for professionals and enthusiasts in the field.
Reference
Core business
SNTWorks
SNTWorks
Stella IT
South Korea
A
- Employees
2017
Key takeaway
Stella IT offers robust cyber security solutions through its global DDoS Mitigation network, which can protect services from attacks with up to 100Gbps of traffic. Their cloud computing services, including support for hosting Minecraft servers, emphasize security and performance tailored to individual needs.
Reference
Product
Stella IT's Technologies - Stella IT
Meet Stella IT's Technologies.
IT-Concept
Seoul, South Korea
A
11-50 Employees
2011
Key takeaway
IT-Concept offers dedicated IT support and manages VPN setup, which is crucial for secure communications, especially for their South Korean branch. Their expertise in IT solutions positions them as a reliable partner for addressing cybersecurity needs.
Reference
Core business
IT-Concept
IT support and profesionnal IT solutions in South Korea
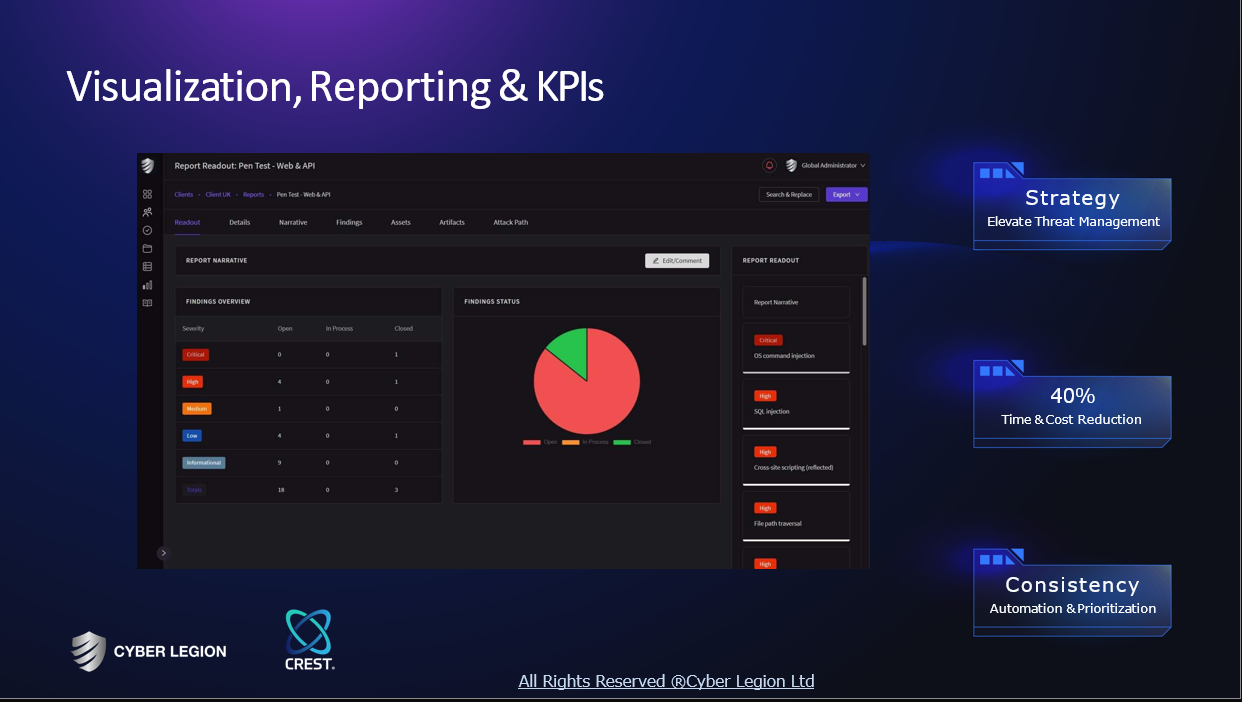
Technologies which have been searched by others and may be interesting for you:
A selection of suitable products and services provided by verified companies according to your search.

Service
Cybersecurity
Go to product

Service
Penetration Testing
Go to product
Service
Security Consultant
Go to product
Service
Product Security
Go to product
A selection of suitable use cases for products or services provided by verified companies according to your search.

Use case
Cybersecurity
All
Cybersecurity is the act of protecting your digital assets against bad actors attack. This is a vast field which starts by identifying the risk in your industry and mitigating these risks on the best of your ability. There is always the probability that a bad actor will penetrate your defense system, in that case you should have in place a response plan. Are your digital assets protected?

Use case
Managed Firewall für ein öffentliches Unternehmen – NIS2-Compliance gewährleistet
Public Sector
Herausforderung: Ein öffentliches Versorgungsunternehmen steht vor der Aufgabe, seine IT-Infrastruktur gegen wachsende Cyberbedrohungen abzusichern und gleichzeitig die Vorgaben der NIS-Richtlinie (Network and Information Security) zu erfüllen. Die internen IT-Ressourcen reichen nicht aus, um die Anforderungen an kontinuierliche Überwachung, Aktualisierungen und Protokollierung zu bewältigen. Lösung: Mit der Managed Firewall von bytehaus wird die Sicherheitsinfrastruktur des Unternehmens auf den neuesten Stand gebracht. Bytehaus analysiert die Netzwerkarchitektur und implementiert eine maßgeschneiderte Firewall-Lösung, die den strengen Anforderungen der NIS-Richtlinie entspricht.

Use case
Managed Firewall für ein Unternehmen mit 10 Mitarbeitern – Prävention nach früherem Hackerangriff
Supplier
Herausforderung: Ein mittelständisches Unternehmen mit 10 Mitarbeitern wurde vor einigen Jahren Opfer eines Hackerangriffs, bei dem sensible Daten gestohlen und der Betrieb erheblich beeinträchtigt wurden. Seitdem besteht ein hohes Sicherheitsbewusstsein, jedoch fehlen die internen Ressourcen, um die IT-Sicherheit auf dem aktuellen Stand zu halten und neue Bedrohungen abzuwehren. Lösung: Mit der Managed Firewall von Bytehaus erhält das Unternehmen eine umfassende Sicherheitslösung, die speziell auf kleine Unternehmen mit begrenzten IT-Ressourcen zugeschnitten ist. Bytehaus übernimmt die Implementierung, Verwaltung und Überwachung der Firewall, sodass das Unternehmen vor zukünftigen Angriffen optimal geschützt ist.

Use case
Cybersecurity
All
Cybersecurity is the act of protecting your digital assets against bad actors attack. This is a vast field which starts by identifying the risk in your industry and mitigating these risks on the best of your ability. There is always the probability that a bad actor will penetrate your defense system, in that case you should have in place a response plan. Are your digital assets protected?
When exploring the Cyber Security IT industry in South Korea, several key considerations emerge. The country has robust regulations governing data protection and cybersecurity, notably through the Personal Information Protection Act (PIPA) and the Cybersecurity Management Act. These regulations demand compliance from businesses, creating a significant opportunity for cybersecurity firms to offer solutions that align with legal requirements. Challenges in the industry include a rising sophistication in cyber threats and a shortage of skilled professionals. Organizations need to focus on continuous training and development to keep up with evolving threats. The competitive landscape is marked by a mix of established firms and startups, fostering innovation and collaboration. South Korea’s strategic position in the global tech market enhances its relevance, as many companies seek to expand their cybersecurity frameworks to meet international standards. Additionally, environmental concerns are gaining traction within the industry, as companies are increasingly expected to adopt sustainable practices in their operations. Given the rapid digital transformation across various sectors, the demand for cybersecurity solutions is expected to grow, presenting significant opportunities for those entering the market. Understanding these factors will be crucial for anyone interested in establishing a career or business in South Korea's Cyber Security IT sector.
Some interesting numbers and facts about your company results for Cyber Security IT
| Country with most fitting companies | South Korea |
| Amount of fitting manufacturers | 2 |
| Amount of suitable service providers | 6 |
| Average amount of employees | 11-50 |
| Oldest suiting company | 2011 |
| Youngest suiting company | 2017 |
Some interesting questions that has been asked about the results you have just received for Cyber Security IT
What are related technologies to Cyber Security IT?
Based on our calculations related technologies to Cyber Security IT are Big Data, E-Health, Retail Tech, Artificial Intelligence & Machine Learning, E-Commerce
Which industries are mostly working on Cyber Security IT?
The most represented industries which are working in Cyber Security IT are IT, Software and Services, Other
How does ensun find these Cyber Security IT Companies?
ensun uses an advanced search and ranking system capable of sifting through millions of companies and hundreds of millions of products and services to identify suitable matches. This is achieved by leveraging cutting-edge technologies, including Artificial Intelligence.