
The B2B platform for the best purchasing descision. Identify and compare relevant B2B manufacturers, suppliers and retailers
Close
Filter
Result configuration
Continents
Select continent
Locations
Result types
Company type
Select company type
Industries
Select industry
Company status
Select company status preset
Number of employees
Min.
Max.
Founding year
Cyberus Labs
Katowice, Poland
B
1-10 Employees
-
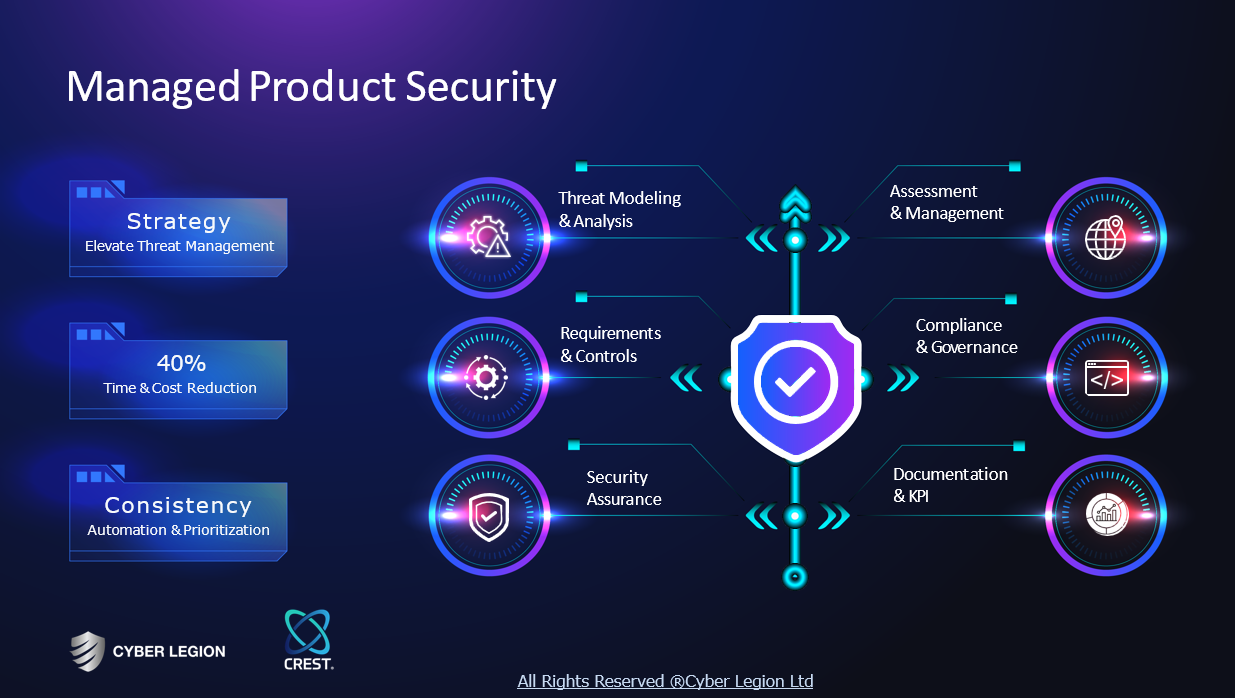
Key takeaway
Cyberus Labs offers innovative, tokenized cybersecurity solutions designed to significantly reduce cyber threats and data breaches. Their unique audio-token technology effectively prevents 80 percent of hacking attacks, making it a key player in safeguarding critical digital infrastructure.
Reference
Core business
O firmie - Cyberus LabsCyberus Labs
Dostarczamy rozwiązania w dziedzinie cyberbezpieczeństwa. Nasz cel to eliminowanie źródła cyber zagrożeń, a nie jedynie reakcja na nie. Łączymy technologię zapr
VOL
Poland
B
11-50 Employees
1992
Key takeaway
The company is dedicated to enhancing security and business continuity through specialized services, focusing on adapting to the evolving cybersecurity landscape. They offer expertise in cyber risk assessments and emphasize their commitment to exceeding customer expectations in IT security.
Reference
Core business
Outsourcing IT | Cybersecurity | people, knowledge, technologies
AVET Information and Network Security Sp. z o.o.
Warsaw, Poland
B
11-50 Employees
1997
Key takeaway
The company specializes in cybersecurity, offering over 21 years of experience in delivering secure software development, risk management, and compliance consulting services across various sectors. Their expertise ensures that organizations can innovate while maintaining compliance with regulatory requirements, thereby building trust with customers.
Reference
Core business
AVETINS
Looking for more accurate results?
Find the right companies for free by entering your custom query!
25M+ companies
250M+ products
Free to use
Security Masters
Warsaw, Poland
B
11-50 Employees
2021
Key takeaway
The company offers a range of cyber security services, including solution assessments and controlled attacks to identify vulnerabilities. They also provide cyber security training, highlighting their commitment to protecting businesses from evolving threats like ransomware.
Reference
Service
Services - SECURITY MASTERS
PREBYTES
Leżajsk, Poland
B
11-50 Employees
2009
Key takeaway
PREBYTES is a global cybersecurity provider that delivers innovative solutions to protect businesses, financial institutions, and government organizations from cyber attacks. With over 15 years of experience, they focus on addressing critical cybersecurity challenges, ensuring compliance with legal regulations, and offering immediate support to strengthen protection against hackers.
Reference
Core business
PREBYTES | Cybersecurity for Business - Effective protection against hacker attacks
Since 2009, we have been providing cybersecurity to companies worldwide. Protecting confidential data, preventing fraud, managing incidents, and protecting brands.
Vector Synergy
Poland
B
11-50 Employees
-
Key takeaway
Vector Synergy specializes in providing expert IT security services, including Cyber Defence, which are essential for projects requiring security clearance. Their highly qualified specialists ensure the protection and integrity of their clients' information systems, making them a valuable partner for organizations focused on cybersecurity.
Reference
Core business
Vector Synergy: Consultancy Services, Cyber Defence Services | Vector Synergy dostarcza firmom i organizacjom ekspertów do realizacji projektów, które wymagają posiadania certyfikatu bezpieczeństwa oraz oferuje kompleksowe usługi i więcej niż zaawansowane rozwiązania w zakresie bezpieczeństwa informatycznego Klientów.
CRAON.PL
Komorów, Poland
B
1-10 Employees
2021
Key takeaway
Craon is a reliable partner that provides Cyber Security solutions to ensure the protection of business data and continuity. Their services focus on safeguarding against cyber attacks, emphasizing the importance of robust security measures beyond just antivirus and antispam.
Reference
Core business
Craon Srl | IT Consulting | Cyber Security
NETWORK-SECURITY-SOLUTIONS
Poland
B
1-10 Employees
2010
Key takeaway
Network Security Solutions specializes in providing professional network and server infrastructure management, emphasizing high-quality security solutions that address market needs. Their commitment to 24/7 monitoring and tailored IT outsourcing services underscores their expertise in creating secure and stable networking environments.
Reference
Core business
[ N-SECURITY.COM ] - [ Network Security Solutions ]
PANDORA COGNITIVE CYBERSECURITY S.A.
Gdynia, Poland
B
251-500 Employees
-
Key takeaway
Pandora Cognitive Cybersecurity focuses on advanced cybersecurity solutions by integrating artificial intelligence and machine learning to address the challenges posed by the rapid growth of IoT. Their systems, such as the Autonomous Data Traffic Analyzer and the Anomaly Intelligence Cockpits, enable immediate detection of suspicious activities and provide cybersecurity experts with powerful tools for threat identification and response.
Reference
Core business
Pandora Cognitive Cybersecurity

Link Group
Sól, Poland
B
51-100 Employees
2016
Key takeaway
The company offers comprehensive cybersecurity services designed to secure critical data and protect businesses. With a team of experts, they provide top-quality solutions that enhance security and support overall business growth.
Reference
Service
Cybersecurity
Secure your business with our Cybersecurity outsourcing services. Our experts provide top-quality solutions to keep your business safe.
Technologies which have been searched by others and may be interesting for you:
A selection of suitable products and services provided by verified companies according to your search.

Service
Cybersecurity
Go to product

Service
Penetration Testing
Go to product
Service
Security Consultant
Go to product
Service
Product Security
Go to product
A selection of suitable use cases for products or services provided by verified companies according to your search.

Use case
Cybersecurity
All
Cybersecurity is the act of protecting your digital assets against bad actors attack. This is a vast field which starts by identifying the risk in your industry and mitigating these risks on the best of your ability. There is always the probability that a bad actor will penetrate your defense system, in that case you should have in place a response plan. Are your digital assets protected?

Use case
Managed Firewall für ein öffentliches Unternehmen – NIS2-Compliance gewährleistet
Public Sector
Herausforderung: Ein öffentliches Versorgungsunternehmen steht vor der Aufgabe, seine IT-Infrastruktur gegen wachsende Cyberbedrohungen abzusichern und gleichzeitig die Vorgaben der NIS-Richtlinie (Network and Information Security) zu erfüllen. Die internen IT-Ressourcen reichen nicht aus, um die Anforderungen an kontinuierliche Überwachung, Aktualisierungen und Protokollierung zu bewältigen. Lösung: Mit der Managed Firewall von bytehaus wird die Sicherheitsinfrastruktur des Unternehmens auf den neuesten Stand gebracht. Bytehaus analysiert die Netzwerkarchitektur und implementiert eine maßgeschneiderte Firewall-Lösung, die den strengen Anforderungen der NIS-Richtlinie entspricht.

Use case
Managed Firewall für ein Unternehmen mit 10 Mitarbeitern – Prävention nach früherem Hackerangriff
Supplier
Herausforderung: Ein mittelständisches Unternehmen mit 10 Mitarbeitern wurde vor einigen Jahren Opfer eines Hackerangriffs, bei dem sensible Daten gestohlen und der Betrieb erheblich beeinträchtigt wurden. Seitdem besteht ein hohes Sicherheitsbewusstsein, jedoch fehlen die internen Ressourcen, um die IT-Sicherheit auf dem aktuellen Stand zu halten und neue Bedrohungen abzuwehren. Lösung: Mit der Managed Firewall von Bytehaus erhält das Unternehmen eine umfassende Sicherheitslösung, die speziell auf kleine Unternehmen mit begrenzten IT-Ressourcen zugeschnitten ist. Bytehaus übernimmt die Implementierung, Verwaltung und Überwachung der Firewall, sodass das Unternehmen vor zukünftigen Angriffen optimal geschützt ist.

Use case
Cybersecurity
All
Cybersecurity is the act of protecting your digital assets against bad actors attack. This is a vast field which starts by identifying the risk in your industry and mitigating these risks on the best of your ability. There is always the probability that a bad actor will penetrate your defense system, in that case you should have in place a response plan. Are your digital assets protected?
When exploring the Cyber Security IT industry in Poland, several key factors warrant attention. The country has a growing demand for cyber security professionals due to an increase in cyber threats, making it an attractive environment for career opportunities. Understanding the regulatory landscape is essential, as Poland adheres to EU regulations like the General Data Protection Regulation (GDPR), which imposes strict data protection standards on businesses. Potential challenges include a talent shortage and the need for continuous skill development, as the industry evolves rapidly with emerging technologies. The competitive landscape in Poland features a mix of established firms and startups, all vying for a share of the market, which fosters innovation but can also complicate entry for new players. Moreover, environmental concerns are becoming increasingly relevant, as cyber security solutions must now consider energy efficiency and sustainability. On a global scale, Poland's cyber security sector is gaining recognition, with many companies engaging in international collaborations and projects. This interconnectedness enhances opportunities for growth and knowledge exchange, positioning Poland as an emerging hub within the European cyber security landscape. Overall, thorough research into these aspects can provide valuable insights for anyone interested in entering this dynamic industry.
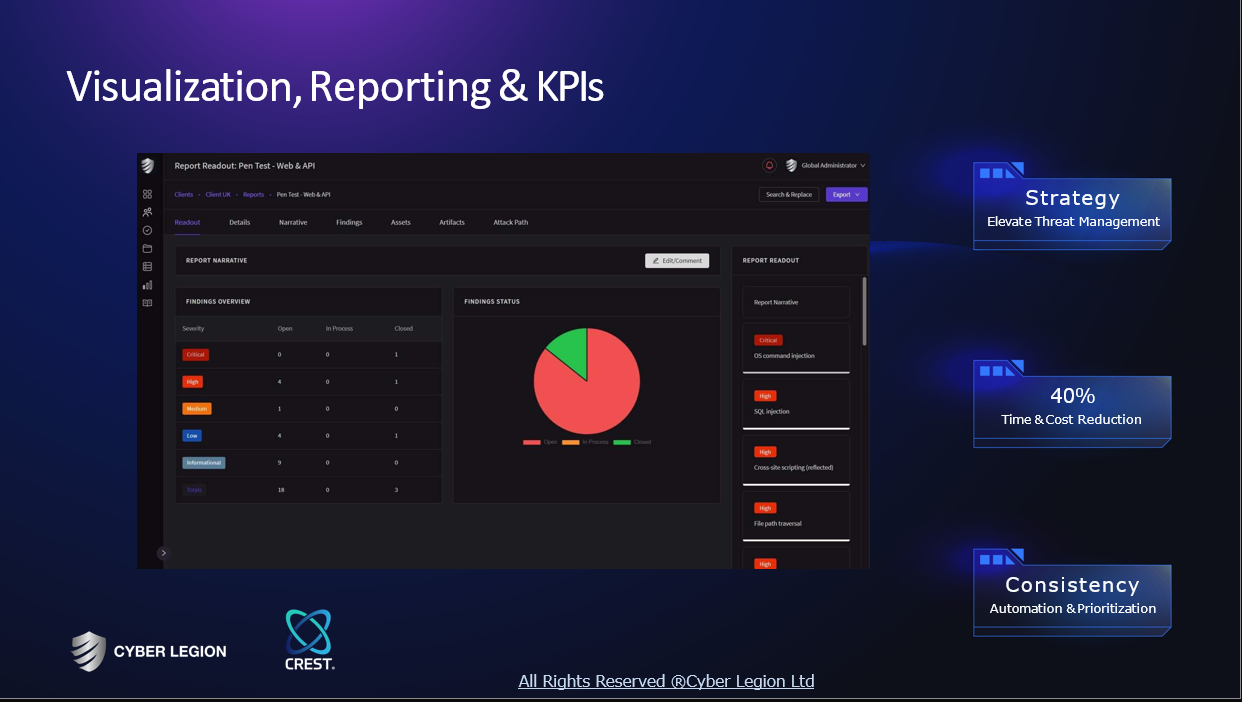
Some interesting numbers and facts about your company results for Cyber Security IT
| Country with most fitting companies | Poland |
| Amount of fitting manufacturers | 40 |
| Amount of suitable service providers | 34 |
| Average amount of employees | 11-50 |
| Oldest suiting company | 1992 |
| Youngest suiting company | 2021 |
Some interesting questions that has been asked about the results you have just received for Cyber Security IT
What are related technologies to Cyber Security IT?
Based on our calculations related technologies to Cyber Security IT are Big Data, E-Health, Retail Tech, Artificial Intelligence & Machine Learning, E-Commerce
Who are Start-Ups in the field of Cyber Security IT?
Start-Ups who are working in Cyber Security IT are Security Masters, CRAON.PL
Which industries are mostly working on Cyber Security IT?
The most represented industries which are working in Cyber Security IT are IT, Software and Services, Business Services, Defense, Other, Cyber Security
How does ensun find these Cyber Security IT Companies?
ensun uses an advanced search and ranking system capable of sifting through millions of companies and hundreds of millions of products and services to identify suitable matches. This is achieved by leveraging cutting-edge technologies, including Artificial Intelligence.