
The B2B platform for the best purchasing descision. Identify and compare relevant B2B manufacturers, suppliers and retailers
Close
Filter
Result configuration
Continents
Select continent
Locations
Result types
Company type
Select company type
Industries
Select industry
Company status
Select company status preset
Number of employees
Min.
Max.
Founding year
Cyber Legion Ltd
London, United Kingdom
A
1-10 Employees
2021
Key takeaway
Cyber Legion Ltd is a UK-EU-based cybersecurity company that specializes in securing remote work environments and product security. They offer comprehensive services, including penetration testing, and provide educational resources to enhance cybersecurity knowledge and skills.
Reference
Service
Security Consultant
At Cyber Legion, we are dedicated to providing top-notch cybersecurity consultancy to protect your business from evolving threats. Our offerings include a meticulous gap analysis and remediation strategy development, aimed at uncovering vulnerabilities and forging robust plans to mitigate them. Leveraging OSINT (Open Source Intelligence) and cutting-edge threat intelligence, we empower your organization to preemptively neutralize potential security threats. Moreover, we specialize in the formulation of Key Performance Indicators (KPIs) and deliver detailed reporting on your security infrastructure's efficacy. This enables you to monitor your cybersecurity posture's evolution and identify key areas for ongoing improvement. At Cyber Legion, we are dedicated to providing top-notch cybersecurity consultancy to protect your business from evolving threats. Our team of experts will work closely with you to develop a tailored security strategy that meets your specific needs. Contact us today for a free consultation! Staying ahead in security challenges and Get in Touch with Cyber Legion or Get a Free Quote
Insyghts Security Pte Ltd
Singapore
C
1-10 Employees
2017
Key takeaway
Insyghts Security is a full-service cybersecurity service provider that offers expertise in governance, engineering, and managed risk operations. With over 25 years of experience, they help organizations assess their security maturity and effectively manage threats to protect critical assets.
Reference
Core business
Insyghts Security – Cybersecurity Service Provider
Agincourt Partners Ltd t/a Cybersec Solutions
United Kingdom
A
1-10 Employees
2015
Key takeaway
Cybersec Solutions offers comprehensive and tailored security solutions to protect organizations from cyber threats, including zero trust networking and a managed security awareness program. Their services aim to reduce risk and prevent data breaches, ensuring businesses receive the right level of protection to meet their specific needs.
Reference
Service
Cybersecurity Services – Cybersec Solutions
Looking for more accurate results?
Find the right companies for free by entering your custom query!
25M+ companies
250M+ products
Free to use
Atlantic Data Security
East Hartford, United States
B
11-50 Employees
1993
Key takeaway
With over 30 years of experience in the cybersecurity industry, the company specializes in creating and managing comprehensive security infrastructures tailored to meet the evolving needs of clients. Their team of skilled engineers is dedicated to protecting assets and provides access to leading cybersecurity technologies and services.
Reference
Core business
The Premier Cybersecurity Solutions Provider
C Company
Melbourne, Australia
A
1-10 Employees
2023
Key takeaway
Cyber Company specializes in providing exceptional and comprehensive cybersecurity solutions, empowering businesses to protect and secure their digital assets. Their mission is to enhance cyber defense through unparalleled expertise and effective project management, ensuring organizations can navigate the digital world with confidence.
Reference
Core business
Cyber Company
Protecture Technology
United Kingdom
A
11-50 Employees
2013
Key takeaway
The company emphasizes its deep understanding and expertise in Cyber Security and Data Security, highlighting the importance of integrating both aspects. They assist clients, particularly in sectors like Charity, Education, Hospitality, and legal, in navigating the challenges and opportunities of digital transformation related to Cyber Security.
Reference
Service
Cyber Security - Protecture
PureCyber Limited
Cardiff, United Kingdom
A
11-50 Employees
2010
Key takeaway
PureCyber is a leading provider of comprehensive managed cyber security solutions, dedicated to enhancing businesses' resilience against cyber threats. Their innovative services and expert team focus on making cyber security accessible and understandable for organizations of all sizes, ensuring effective protection against various cyber risks.
Reference
Service
Award Winning Cyber Security Services — PureCyber
Learn more about our effective cyber security services to protect you from current and emerging cyber threats.

CYBER SECURITY WAREHOUSE LTD
Reading, United Kingdom
A
1-10 Employees
2019
Key takeaway
The company provides Cyber Security consulting services to help businesses address their Cyber Security requirements, including regulatory compliance and annual testing.
Reference
Core business
Cyber Security Warehouse
CyberNX Technologies Private Limited
Mumbai, India
D
11-50 Employees
2018
Key takeaway
CyberNX is a dynamic Cyber Security firm that offers innovative solutions and services, emphasizing the importance of embedding information security into an organization's core. They provide comprehensive Cyber Security Leadership services, 24/7 monitoring through their Security Operations Centre, and assistance in implementing security standards and frameworks to protect against advanced cyber threats.
Reference
Core business
Cyber Security and Cloud Security Company in India - CyberNX
Cyber Security and Cloud Security Company in India
CyberSecOn
Melbourne, Australia
A
11-50 Employees
2016
Key takeaway
CyberSecOn is dedicated to delivering advanced cyber security solutions, including network, application, and data security for both IT and OT services. With a team of professionals and a strong track record, they offer a comprehensive range of security services designed to meet the diverse needs of enterprises.
Reference
Core business
Company – CyberSecOn
Technologies which have been searched by others and may be interesting for you:
A selection of suitable products and services provided by verified companies according to your search.

Product
Text Anonymization Service
Go to product
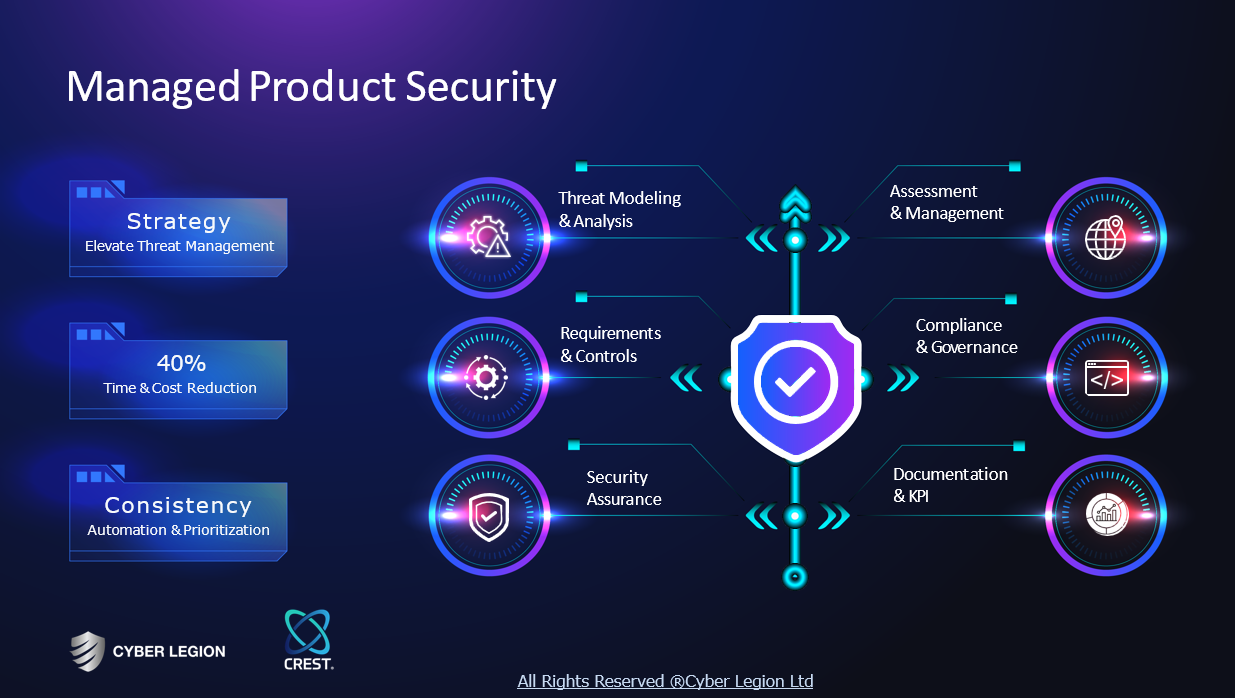
Service
Security Consultant
Go to product
Service
Product Security
Go to product

Product
enclaive vHSM
Go to product
A selection of suitable use cases for products or services provided by verified companies according to your search.

Use case
Cybersecurity
All
Cybersecurity is the act of protecting your digital assets against bad actors attack. This is a vast field which starts by identifying the risk in your industry and mitigating these risks on the best of your ability. There is always the probability that a bad actor will penetrate your defense system, in that case you should have in place a response plan. Are your digital assets protected?

Use case
Managed Firewall für ein öffentliches Unternehmen – NIS2-Compliance gewährleistet
Public Sector
Herausforderung: Ein öffentliches Versorgungsunternehmen steht vor der Aufgabe, seine IT-Infrastruktur gegen wachsende Cyberbedrohungen abzusichern und gleichzeitig die Vorgaben der NIS-Richtlinie (Network and Information Security) zu erfüllen. Die internen IT-Ressourcen reichen nicht aus, um die Anforderungen an kontinuierliche Überwachung, Aktualisierungen und Protokollierung zu bewältigen. Lösung: Mit der Managed Firewall von bytehaus wird die Sicherheitsinfrastruktur des Unternehmens auf den neuesten Stand gebracht. Bytehaus analysiert die Netzwerkarchitektur und implementiert eine maßgeschneiderte Firewall-Lösung, die den strengen Anforderungen der NIS-Richtlinie entspricht.

Use case
Managed Firewall für ein Unternehmen mit 10 Mitarbeitern – Prävention nach früherem Hackerangriff
Supplier
Herausforderung: Ein mittelständisches Unternehmen mit 10 Mitarbeitern wurde vor einigen Jahren Opfer eines Hackerangriffs, bei dem sensible Daten gestohlen und der Betrieb erheblich beeinträchtigt wurden. Seitdem besteht ein hohes Sicherheitsbewusstsein, jedoch fehlen die internen Ressourcen, um die IT-Sicherheit auf dem aktuellen Stand zu halten und neue Bedrohungen abzuwehren. Lösung: Mit der Managed Firewall von Bytehaus erhält das Unternehmen eine umfassende Sicherheitslösung, die speziell auf kleine Unternehmen mit begrenzten IT-Ressourcen zugeschnitten ist. Bytehaus übernimmt die Implementierung, Verwaltung und Überwachung der Firewall, sodass das Unternehmen vor zukünftigen Angriffen optimal geschützt ist.

Use case
Protecting Critical Infrastructure from Cyber Threats
KRITIS, Critical Infrastructure, Industries with Sensitive Data, Healthcare, Energy, Gov, Supplier
Operators of critical infrastructure such as energy, water, transportation, and healthcare are prime targets for cyberattacks. Many industrial control systems (ICS) and SCADA environments sometimes rely software that is difficult to patch, while strict regulatory requirements like NIS2 and BSI-KritisV demand enhanced security measures. Labyrinth uses specialized SCADA and OT decoys to simulate real industrial control systems, misleading attackers and capturing their activity without impacting operational performance. This ensures early threat detection, supports regulatory compliance with detailed forensic reporting, and protects against APTs and ransomware targeting critical systems.

Use case
Protecting SMEs Against Targeted Cyber Attacks
SME, all
Small and medium-sized enterprises (SMEs) often have limited IT resources and no dedicated Security Operations Center (SOC). They are particularly vulnerable to ransomware, phishing attacks, and data theft as traditional security systems like firewalls or antivirus software fail to counter modern threats. Labyrinth provides an easy-to-implement and cost-efficient deception technology that lures attackers into simulated IT environments, enabling threat detection up to 12 times faster before real damage occurs. This proactive approach reduces false positives, minimizes downtime, and ensures effective cybersecurity without requiring additional IT staff or high costs.

Use case
Reducing SOC Workload in Large Enterprises
Enterprise, all
Security teams in large enterprises face an overwhelming number of security alerts, including many false positives, making it difficult to detect and respond to advanced persistent threats (APTs). Labyrinth deploys highly realistic decoys within corporate networks, attracting and identifying attackers before they can infiltrate critical systems. By providing detailed forensic insights and attack timelines, Labyrinth helps SOC teams focus on real threats, reduces alert fatigue, and seamlessly integrates with existing SIEM, EDR, and firewall solutions for automated defense.

Use case
Cybersecurity
All
Cybersecurity is the act of protecting your digital assets against bad actors attack. This is a vast field which starts by identifying the risk in your industry and mitigating these risks on the best of your ability. There is always the probability that a bad actor will penetrate your defense system, in that case you should have in place a response plan. Are your digital assets protected?
Cyber security refers to the practice of protecting systems, networks, and programs from digital attacks. These attacks are typically aimed at accessing, altering, or destroying sensitive information, extorting money from users, or interrupting normal business processes. With the increasing reliance on technology, the importance of cyber security has grown significantly, as threats evolve and become more sophisticated. Effective cyber security involves a combination of technologies, processes, and practices designed to safeguard devices and data. This includes implementing firewalls, encryption, and intrusion detection systems, as well as fostering a culture of security awareness among employees. Organizations must continuously assess their security posture, adapting to new threats and ensuring compliance with regulatory standards to protect their assets and maintain customer trust.
Cyber security is crucial for businesses as it protects sensitive information from unauthorized access and cyber threats. A robust cyber security strategy helps safeguard customer data, financial information, and intellectual property, preventing costly breaches that can damage a company’s reputation and lead to significant financial losses. Furthermore, compliance with industry regulations often mandates strong cyber security measures. By ensuring a secure environment, businesses can maintain trust with customers and partners, fostering a safe digital landscape that supports growth and innovation.
1. Malware
Malware is a prevalent threat in cyber security, encompassing various malicious software types such as viruses, worms, and ransomware. These programs can infiltrate systems, steal sensitive data, and disrupt operations.
2. Phishing
Phishing attacks involve deceptive emails or messages that trick individuals into revealing personal information or downloading harmful software. This tactic relies on social engineering to exploit human trust.
3. Denial-of-Service (DoS) Attacks
DoS attacks aim to overwhelm a system or network, rendering it unavailable to users. By flooding the target with excessive traffic, attackers can disrupt services, causing significant downtime and financial loss.
4. Insider Threats
Insider threats come from within an organization, often involving employees or contractors who misuse their access to sensitive information. This can lead to data breaches and significant harm to the organization’s reputation.
5. Advanced Persistent Threats (APTs)
APTs are prolonged and targeted cyber attacks where an intruder gains access to a network and remains undetected for an extended period. These threats often aim to steal sensitive data or intellectual property.
6. Zero-Day Exploits
Zero-day exploits target vulnerabilities that developers have not yet patched. Attackers leverage these vulnerabilities before they are known to the software vendor, making them particularly dangerous.
7. Credential Theft
Credential theft involves stealing usernames and passwords to gain unauthorized access to systems and data. This can occur through various methods, including keylogging and data breaches.
1. Regular Security Assessments
Conducting regular security assessments helps identify vulnerabilities within a company's network and systems. By evaluating current security measures and simulating attacks, organizations can understand their weak points and address them proactively.
2. Employee Training
Providing comprehensive training for employees is crucial in enhancing cyber security. Educating staff about recognizing phishing attempts, securing their devices, and following company protocols can significantly reduce the risk of human error, which is often a major factor in security breaches.
1. Regular Software Updates
Keeping software and systems updated is crucial. Timely updates patch vulnerabilities that cyber attackers could exploit, ensuring the integrity of the network.
2. Strong Password Policies
Implementing complex password requirements and encouraging regular changes can significantly reduce unauthorized access. Multifactor authentication adds an additional layer of security.
3. Employee Training
Educating staff about cyber threats and safe practices is vital. Regular training sessions help employees recognize phishing attempts and other social engineering tactics.
4. Data Encryption
Encrypting sensitive data protects it from unauthorized access. Even if data is intercepted, encryption makes it unreadable without the proper decryption key.
5. Regular Backups
Frequent data backups ensure that critical information can be restored in the event of a cyber attack. This practice minimizes downtime and data loss.
6. Firewall and Antivirus Protection
Using firewalls and antivirus software helps detect and block malicious activities. These tools act as the first line of defense against cyber threats.
7. Incident Response Plan
Having a well-defined incident response plan prepares organizations to respond effectively to cyber incidents. This ensures quick recovery and minimizes damage.
8. Network Segmentation
Dividing the network into segments limits access to sensitive information. This makes it harder for attackers to move laterally within the network if they gain entry.
9. Regular Security Audits
Conducting periodic security assessments helps identify vulnerabilities. This proactive approach allows organizations to address issues before they can be exploited.
10. Access Controls
Implementing strict access controls ensures that only authorized personnel can access sensitive data. This reduces the risk of insider threats and data breaches.
Some interesting numbers and facts about your company results for Cyber Security
| Country with most fitting companies | United States |
| Amount of fitting manufacturers | 10000 |
| Amount of suitable service providers | 10000 |
| Average amount of employees | 11-50 |
| Oldest suiting company | 1993 |
| Youngest suiting company | 2023 |
20%
40%
60%
80%
Some interesting questions that has been asked about the results you have just received for Cyber Security
What are related technologies to Cyber Security?
Based on our calculations related technologies to Cyber Security are Space Technologies, Military, Commercial Aviation, Airport Security
Who are Start-Ups in the field of Cyber Security?
Start-Ups who are working in Cyber Security are Cyber Legion Ltd, C Company
Which industries are mostly working on Cyber Security?
The most represented industries which are working in Cyber Security are IT, Software and Services, Defense, Other, Telecommunications, Consulting
How does ensun find these Cyber Security Companies?
ensun uses an advanced search and ranking system capable of sifting through millions of companies and hundreds of millions of products and services to identify suitable matches. This is achieved by leveraging cutting-edge technologies, including Artificial Intelligence.