
The B2B platform for the best purchasing descision. Identify and compare relevant B2B manufacturers, suppliers and retailers
Close
Filter
Result configuration
Continents
Select continent
Locations
Result types
Company type
Select company type
Industries
Select industry
Company status
Select company status preset
Number of employees
Min.
Max.
Founding year
CloudCodes Software
India
D
11-50 Employees
2011
Key takeaway
CloudCodes specializes in providing innovative and robust cloud data security solutions, enabling enterprises to protect their data across various SaaS applications effectively. Recognized by Gartner and certified as a SOC Type-II company, CloudCodes offers integrated security measures that empower businesses to adopt cloud technologies with confidence, addressing their data security concerns comprehensively.
Reference
Product
Advanced Cloud Data Security Solutions For Challenging Cloud Platforms
CloudLink Technologies
Ottawa, Canada
A
51-100 Employees
-
Key takeaway
CloudLink specializes in providing cloud security and management solutions, particularly for enterprises and IT service providers. Their award-winning software addresses key concerns of CIOs, enabling the secure adoption of cloud computing for sensitive and regulated workloads.
Reference
Product
Cloud Encryption Management for Enterprise and Governments
Datacenter virtualization cloud security management software for enterprise and government.

TRI-LAN I.T. LIMITED
Exeter, United Kingdom
A
1-10 Employees
1997
Key takeaway
The company offers a comprehensive range of cloud services, including secure cloud storage, tailored to meet the specific IT needs of businesses. Their focus on reliable and fast connectivity solutions, along with customizable IT services, enhances business performance and security in the cloud.
Reference
Service
Secure Cloud Storage
Looking for more accurate results?
Find the right companies for free by entering your custom query!
25M+ companies
250M+ products
Free to use
iSOC24 B.V.
Culemborg, Netherlands
A
11-50 Employees
2012
Key takeaway
iSOC24 focuses on helping organizations effectively manage and monitor their risks in real time, making it particularly relevant for sectors like banking, finance, and government. Their approach includes a robust cloud security management platform that emphasizes data classification, operational resilience through detection and prevention, and the integration of Cyber Threat Intelligence, all essential components for enhancing cloud data security.
Reference
Product
Cloud Security
Cloud Raxak
Los Gatos, United States
B
11-50 Employees
2014
Key takeaway
Cloud Raxak focuses on automating and simplifying security compliance for cloud assets, ensuring comprehensive protection across various infrastructure types. With a strong foundation in security expertise, the company is dedicated to safeguarding enterprise assets in the cloud.
Reference
Product
Google Cloud Security | Cloud Raxak
ScyberX
Watford, United Kingdom
A
1-10 Employees
2019
Key takeaway
The company emphasizes its extensive experience in the IT and security industry, particularly in cloud security, and its commitment to providing innovative and cost-effective solutions.
Reference
Service
Service
McAfee Enterprise
-
1001-5000 Employees
-
Key takeaway
Skyhigh Security emphasizes its commitment to cloud data security by providing adaptive data protection that safeguards sensitive information throughout its lifecycle. The company integrates security into every initiative, ensuring a secure environment for remote work and addressing comprehensive security needs across cloud, web, and network.
Reference
Core business
Enterprise Cloud Data Protection - Skyhigh Security
Skyhigh Security enables your remote workforce while addressing your cloud, web, data, and network security needs. Enterprise data protection anywhere.
CloudProtect
Midrand, South Africa
C
1-10 Employees
2017
Key takeaway
CloudProtect offers a robust, secure, and user-friendly cloud-based data backup solution that allows users to backup, archive, and recover their data across various operating systems and business sizes. With features designed to protect data effectively, it positions itself as a comprehensive solution for cloud data security.
Reference
Core business
CloudProtect - Secure Backup in the Cloud
Cloudbia Technologies
Dubai, United Arab Emirates
C
11-50 Employees
2012
Key takeaway
CloudBIA is a global digital solutions provider that specializes in IT transformation and offers services related to data security. Their strategic consulting helps clients develop effective strategies for digital innovation and hybrid multi-cloud deployments.
Reference
Service
Data Security - Cloudbia
Cyral
Temecula, United States
B
11-50 Employees
2018
Key takeaway
Cyral specializes in securing and governing cloud data, offering a user-friendly data mesh security service that integrates with various data services. Their platform automates workflows and enhances collaboration between DevOps and security teams, providing critical visibility and control to prevent data breaches and leaks.
Reference
Core business
Stop Data Breaches and Leaks. Data Security Governance - Cyral
Easily observe, protect, and control your data endpoints in a cloud and DevOps-first world. Discover Security as Code with Cyral.
Technologies which have been searched by others and may be interesting for you:
A selection of suitable products and services provided by verified companies according to your search.
Service
Product Security
Go to product

Product
enclaive vHSM
Go to product

Service
EMCP
Go to product
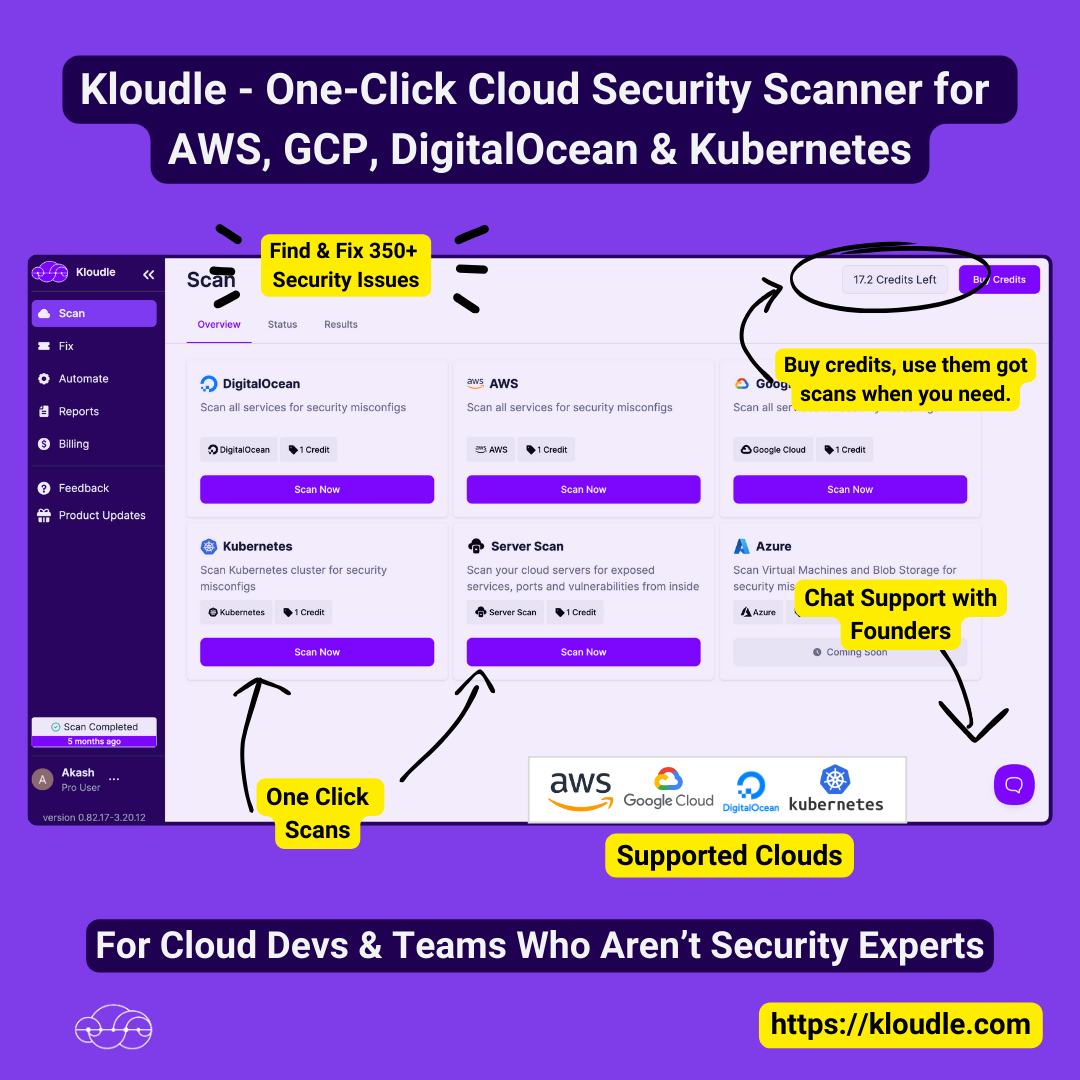
Service
Kloudle
Go to product
A selection of suitable use cases for products or services provided by verified companies according to your search.
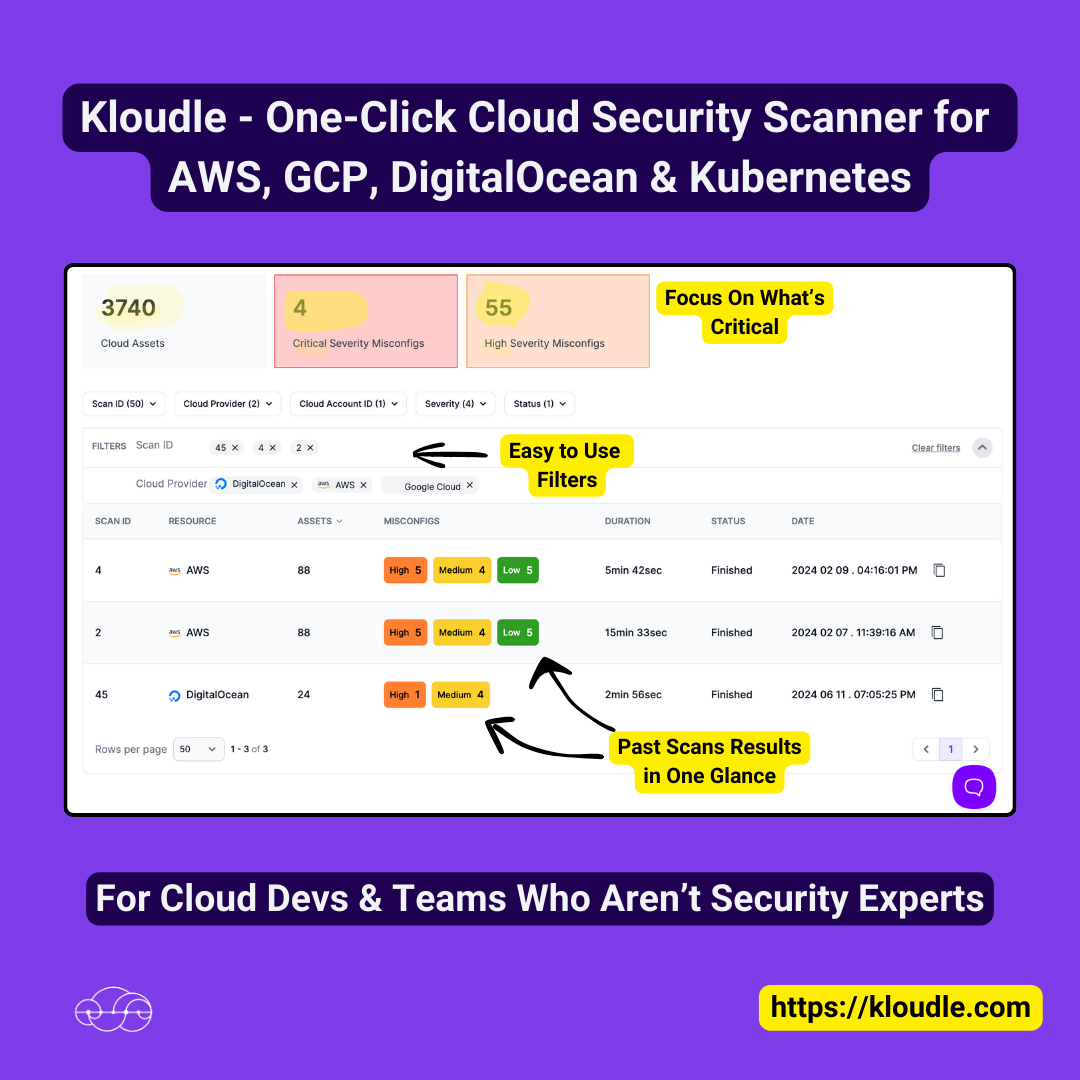
Use case
Comprehensive Cloud Security Management with Kloudle
software
Kloudle enables businesses to protect their cloud environments efficiently by offering a comprehensive cloud security posture management system. It scans for over 350 potential security issues and provides actionable solutions, all without requiring specialized expertise. Major cloud providers such as AWS, Google Cloud, DigitalOcean, Azure, and Kubernetes are supported, ensuring broad compatibility and robust security management. With user-friendly features including a centralized dashboard, actionable insights, rapid scan results, and comprehensive reporting, Kloudle empowers users to maintain a secure cloud environment effortlessly.

Use case
Comprehensive Cloud Security Management with Kloudle
software
Kloudle enables businesses to protect their cloud environments efficiently by offering a comprehensive cloud security posture management system. It scans for over 350 potential security issues and provides actionable solutions, all without requiring specialized expertise. Major cloud providers such as AWS, Google Cloud, DigitalOcean, Azure, and Kubernetes are supported, ensuring broad compatibility and robust security management. With user-friendly features including a centralized dashboard, actionable insights, rapid scan results, and comprehensive reporting, Kloudle empowers users to maintain a secure cloud environment effortlessly.
Cloud data security refers to the measures and protocols put in place to protect data stored in cloud environments from unauthorized access, data breaches, and other cyber threats. This involves the use of encryption, identity and access management, and regular security audits to ensure that sensitive information remains secure. In addition, cloud data security encompasses compliance with regulations and standards, ensuring that data handling practices meet legal requirements. By implementing robust security practices, organizations can safeguard their data assets while leveraging the flexibility and scalability of cloud services.
Cloud Data Security employs a combination of advanced technologies and best practices to safeguard sensitive information. Encryption plays a crucial role by converting data into a secure format that can only be read by authorized users. This ensures that even if unauthorized access occurs, the information remains protected. Additionally, access controls are implemented to limit who can view or modify the data. Multi-factor authentication adds another layer of security by requiring users to provide multiple forms of verification before accessing sensitive information. Regular audits and compliance checks help maintain security standards, ensuring that data protection measures are effective and up-to-date.
1. Data Breaches
Organizations often face the risk of unauthorized access to sensitive data stored in the cloud. Cybercriminals exploit vulnerabilities to gain access, leading to potential exposure of personal and confidential information.
2. Insider Threats
Employees or contractors with access to cloud data can pose significant risks. Whether intentional or accidental, insider threats can result in data leaks or misuse, making it critical for organizations to monitor user access and activities.
3. Insecure APIs
Cloud services often rely on APIs for functionality and integration. If these APIs are not properly secured, they can become entry points for attackers, allowing them to manipulate or extract data.
4. Data Loss
Cloud data can be lost due to various factors, including accidental deletion, malicious attacks, or service outages. Without proper backup solutions, organizations may face severe consequences from lost data.
5. Account Hijacking
Cybercriminals may attempt to gain control of user accounts through phishing or credential theft. Once they have access, they can manipulate data and services, often without the victim's knowledge.
Businesses can ensure compliance with Cloud Data Security standards by implementing a robust framework that includes regular audits and assessments of their cloud environments. Establishing policies that align with industry regulations, such as GDPR, HIPAA, or PCI-DSS, is essential. Training employees on best practices for data handling and security measures also plays a crucial role. Additionally, utilizing encryption for data at rest and in transit, along with identity and access management (IAM) tools, helps protect sensitive information. Regularly updating and patching systems further minimizes vulnerabilities and enhances overall compliance.
1. Data Encryption
Implementing strong encryption for data at rest and in transit is essential. This protects sensitive information from unauthorized access, ensuring that even if data is intercepted or accessed, it remains unreadable without the proper decryption keys.
2. Access Control
Establishing strict access controls is crucial. Limiting user access based on roles and responsibilities minimizes the risk of data breaches. Multi-factor authentication adds an extra layer of security by requiring additional verification beyond just passwords.
3. Regular Audits and Monitoring
Conducting regular security audits and continuous monitoring of cloud environments helps identify vulnerabilities and suspicious activities. This proactive approach allows organizations to address potential threats before they escalate into serious issues.
4. Compliance with Regulations
Adhering to industry regulations and standards, such as GDPR or HIPAA, is vital for maintaining data security. Compliance not only protects sensitive data but also builds trust with clients and stakeholders.
5. Data Backup and Recovery
Implementing a robust data backup and recovery plan ensures that data can be restored in case of loss or corruption. Regular backups protect against data breaches and accidental deletions, allowing for quick recovery of critical information.
Some interesting numbers and facts about your company results for Cloud Data Security
| Country with most fitting companies | United States |
| Amount of fitting manufacturers | 7432 |
| Amount of suitable service providers | 8604 |
| Average amount of employees | 11-50 |
| Oldest suiting company | 1997 |
| Youngest suiting company | 2019 |
20%
40%
60%
80%
Some interesting questions that has been asked about the results you have just received for Cloud Data Security
What are related technologies to Cloud Data Security?
Based on our calculations related technologies to Cloud Data Security are Education, Engineering Services, IT & Technology Services, Healthcare Services, Consulting
Which industries are mostly working on Cloud Data Security?
The most represented industries which are working in Cloud Data Security are IT, Software and Services, Other, Defense, Consulting, Telecommunications
How does ensun find these Cloud Data Security Companies?
ensun uses an advanced search and ranking system capable of sifting through millions of companies and hundreds of millions of products and services to identify suitable matches. This is achieved by leveraging cutting-edge technologies, including Artificial Intelligence.