
The B2B platform for the best purchasing descision. Identify and compare relevant B2B manufacturers, suppliers and retailers
Close
Filter
Result configuration
Continents
Select continent
Locations
Result types
Company type
Select company type
Industries
Select industry
Company status
Select company status preset
Number of employees
Min.
Max.
Founding year
ScyberX
Watford, United Kingdom
A
1-10 Employees
2019
Key takeaway
The company emphasizes its extensive experience in the IT and security industry, particularly in cloud security, making it a trusted partner for organizations seeking to enhance their cloud computing security. Their innovative approach and commitment to transparency foster long-term relationships with clients across various sectors.
Reference
Service
Service
iSOC24 B.V.
Culemborg, Netherlands
A
11-50 Employees
2012
Key takeaway
iSOC24 focuses on helping organizations effectively manage and monitor their risks in real time, making it particularly relevant for sectors like banking, finance, and government. The company emphasizes the importance of cloud security management, highlighting key concepts such as data classification, operational resilience through detection and prevention, and the role of Security Incident & Event Management in monitoring and alerting on security events.
Reference
Product
Cloud Security
Cloud Raxak
Los Gatos, United States
B
11-50 Employees
2014
Key takeaway
Cloud Raxak focuses on automating and simplifying security compliance across various infrastructures, including cloud assets. With a strong foundation in security expertise, the company is committed to ensuring the security of all enterprise assets.
Reference
Product
Amazon Web Services Cloud Security | Cloud Raxak
Looking for more accurate results?
Find the right companies for free by entering your custom query!
25M+ companies
250M+ products
Free to use
A-Cloud Solutions
New York, United States
B
11-50 Employees
-
Key takeaway
The company collaborates with top cloud providers to facilitate the migration of legacy data systems to the cloud.
Reference
Core business
Cloud Solutions Provider
SecureClouds
Hyderabad, India
D
1-10 Employees
2019
Key takeaway
SecureClouds is a prominent online training provider specializing in cloud security, which is essential for protecting cloud computing systems. Their training emphasizes the importance of technology, protocols, and best practices that safeguard cloud environments and data, highlighting the collaborative efforts required from both cloud providers and clients to ensure security.
Reference
Core business
Home
SCloud Pte. Ltd.
Singapore
C
11-50 Employees
2016
Key takeaway
SCloud specializes in providing secure cloud computing solutions, including security-as-a-service, backed by a robust infrastructure and a commitment to 24/7 customer support. With over 18 tier-3 data centers worldwide, SCloud ensures reliable and high-performance services for its clients.
Reference
Product
Cloud Security – SCloud
Cloud IT Service
Basta Tahta, Lebanon
D
11-50 Employees
2016
Key takeaway
Cloud IT Service offers a comprehensive suite of cloud computing solutions, including system migration and hybrid cloud environments, aimed at enhancing performance and efficiency for businesses. Their commitment to innovative technology and advanced security measures positions them as a key player in the cloud computing landscape.
Reference
Service
Advanced Security – Cloud IT Service
ITOTS Networks LLC
Hyattsville, United States
B
1-10 Employees
2007
Key takeaway
ITCloudSEC offers comprehensive security solutions that enhance the visibility and protection of applications across both physical and virtual networks. Their partnerships with various Cloud Service & Security Providers enable teams to secure critical operations effectively, ensuring data integrity in cloud computing environments.
Reference
Service
Services | ITcloudSEC
Orbit3 Consultancy
Sydney, Australia
A
1-10 Employees
2019
Key takeaway
The company emphasizes its expertise in cloud security, stating that their team conducts comprehensive assessments of technology stacks and workloads. This meticulous approach allows them to design and implement robust cloud security solutions tailored to clients' needs.
Reference
Service
Cloud Security
Cliffside Security Pty Ltd
Sydney, Australia
A
1-10 Employees
2014
Key takeaway
The company specializes in designing and implementing security management frameworks and developing roadmaps for cloud environments, ensuring protection against evolving threats. With over 20 years of experience, they help businesses achieve compliance and identify IT risks, transforming them into opportunities.
Reference
Core business
Cloud Security | Cliffside Security
Technologies which have been searched by others and may be interesting for you:
A selection of suitable products and services provided by verified companies according to your search.
Service
Product Security
Go to product

Product
enclaive vHSM
Go to product

Service
EMCP
Go to product

Service
Cloud Hosting
Go to product
A selection of suitable use cases for products or services provided by verified companies according to your search.
Use case
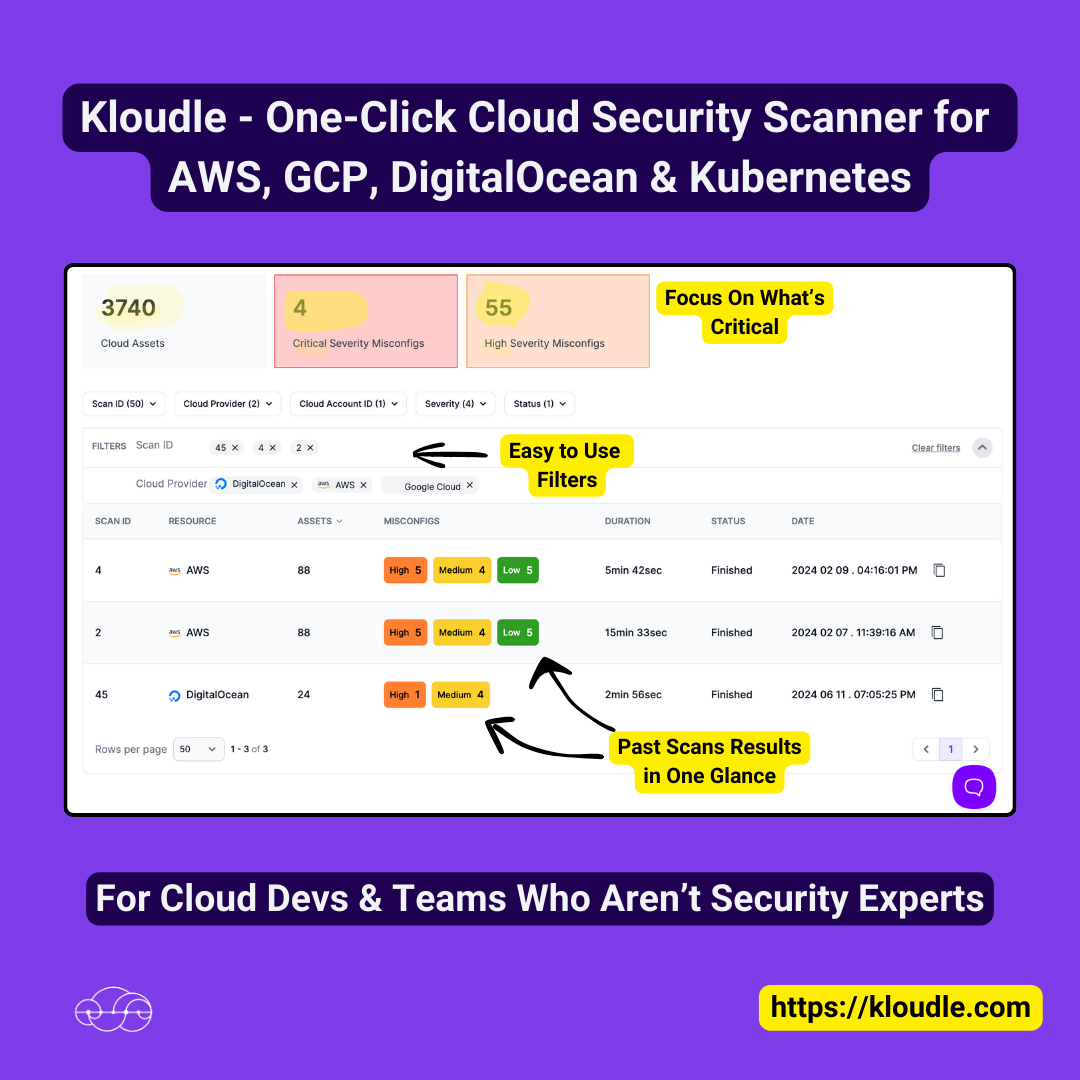
Comprehensive Cloud Security Management with Kloudle
software
Kloudle enables businesses to protect their cloud environments efficiently by offering a comprehensive cloud security posture management system. It scans for over 350 potential security issues and provides actionable solutions, all without requiring specialized expertise. Major cloud providers such as AWS, Google Cloud, DigitalOcean, Azure, and Kubernetes are supported, ensuring broad compatibility and robust security management. With user-friendly features including a centralized dashboard, actionable insights, rapid scan results, and comprehensive reporting, Kloudle empowers users to maintain a secure cloud environment effortlessly.

Use case
Comprehensive Cloud Security Management with Kloudle
software
Kloudle enables businesses to protect their cloud environments efficiently by offering a comprehensive cloud security posture management system. It scans for over 350 potential security issues and provides actionable solutions, all without requiring specialized expertise. Major cloud providers such as AWS, Google Cloud, DigitalOcean, Azure, and Kubernetes are supported, ensuring broad compatibility and robust security management. With user-friendly features including a centralized dashboard, actionable insights, rapid scan results, and comprehensive reporting, Kloudle empowers users to maintain a secure cloud environment effortlessly.
Cloud computing security encompasses a set of policies, technologies, and controls designed to protect data, applications, and infrastructures involved in cloud computing. This security framework aims to safeguard cloud environments from various threats, including data breaches, unauthorized access, and service disruptions. By implementing encryption, identity management, and access controls, organizations can enhance their security posture while leveraging the scalability and flexibility of cloud services. The integration of these measures ensures that sensitive information remains secure and compliant with regulatory standards, ultimately fostering trust in cloud solutions.
Cloud computing security employs various measures to safeguard data stored in the cloud. These measures include encryption, which ensures that sensitive information is transformed into an unreadable format that can only be decrypted by authorized users. Access controls play a crucial role as well, allowing administrators to set permissions and restrict data access based on user roles. Additionally, continuous monitoring helps in identifying and responding to potential threats in real-time. Providers often implement multi-factor authentication, adding an extra layer of security by requiring users to verify their identity through multiple methods. Together, these strategies create a robust defense against unauthorized access and data breaches, ensuring that data remains secure in cloud environments.
Common threats to cloud computing security include data breaches and unauthorized access. These incidents occur when sensitive information is exposed due to vulnerabilities in the cloud infrastructure or misconfigurations by users. Another significant threat is the risk of denial-of-service (DoS) attacks, which can overwhelm cloud services and render them inaccessible. Additionally, the use of insecure application programming interfaces (APIs) can lead to exploitation, compromising the integrity and confidentiality of data stored in the cloud. Organizations must remain vigilant and implement robust security measures to mitigate these risks.
1. Multi-Factor Authentication
Implementing multi-factor authentication (MFA) adds an extra layer of security by requiring users to provide multiple forms of verification before accessing cloud services. This significantly reduces the risk of unauthorized access.
2. Data Encryption
Utilizing encryption for data at rest and in transit ensures that sensitive information is protected from unauthorized access. Even if data is intercepted, it remains unreadable without the decryption key.
3. Regular Security Audits
Conducting regular security audits helps identify vulnerabilities within cloud systems. These assessments can lead to the implementation of stronger security measures and compliance with industry standards.
4. Continuous Monitoring
Employing continuous monitoring tools enables real-time detection of suspicious activity. This proactive approach allows for immediate responses to potential threats, minimizing the impact of security breaches.
5. Employee Training
Providing comprehensive training for employees on security best practices enhances overall awareness. Educated staff are less likely to fall victim to phishing attacks and other common security threats.
Several compliance standards are essential for ensuring the security of cloud computing environments. One prominent standard is the General Data Protection Regulation (GDPR), which mandates strict data protection and privacy measures for organizations handling personal data of EU citizens. Another critical framework is the Health Insurance Portability and Accountability Act (HIPAA), which applies to organizations in the healthcare sector, requiring them to safeguard sensitive patient information. Additionally, Payment Card Industry Data Security Standard (PCI DSS) is vital for any entity that stores, processes, or transmits cardholder data, ensuring secure transactions. Compliance with these standards helps cloud computing security providers demonstrate their commitment to data protection and builds trust with their clients.
Some interesting numbers and facts about your company results for Cloud Computing Security
| Country with most fitting companies | United States |
| Amount of fitting manufacturers | 7539 |
| Amount of suitable service providers | 9277 |
| Average amount of employees | 11-50 |
| Oldest suiting company | 2007 |
| Youngest suiting company | 2019 |
20%
40%
60%
80%
Some interesting questions that has been asked about the results you have just received for Cloud Computing Security
What are related technologies to Cloud Computing Security?
Based on our calculations related technologies to Cloud Computing Security are Big Data, E-Health, Retail Tech, Artificial Intelligence & Machine Learning, E-Commerce
Which industries are mostly working on Cloud Computing Security?
The most represented industries which are working in Cloud Computing Security are IT, Software and Services, Other, Defense, Telecommunications, Consulting
How does ensun find these Cloud Computing Security Companies?
ensun uses an advanced search and ranking system capable of sifting through millions of companies and hundreds of millions of products and services to identify suitable matches. This is achieved by leveraging cutting-edge technologies, including Artificial Intelligence.