
The B2B platform for the best purchasing descision. Identify and compare relevant B2B manufacturers, suppliers and retailers
Close
Filter
Result configuration
Continents
Select continent
Locations
Result types
Company type
Select company type
Industries
Select industry
Company status
Select company status preset
Number of employees
Min.
Max.
Founding year
Guardanet
Łódź, Poland
B
1-10 Employees
2017
Key takeaway
Guardanet specializes in defining secure architectures for cloud-based and on-premise workloads, emphasizing security best practices that align with business objectives. With expertise in AWS Cloud Security and Kubernetes Security, the company is well-equipped to address cloud computing security needs.
Reference
Service
Public Cloud Security – Guardanet | Security Architecture | Public Cloud Security | Kubernetes Security
Cloud Services ☁️
Sopot, Poland
B
51-100 Employees
2009
Key takeaway
Cloud Services specializes in efficiently migrating service infrastructure and optimizing data storage and processing costs in the cloud. Their expertise in IT support and understanding of banking product requirements enhances the implementation of dedicated solutions for electronic channels.
Reference
Core business
About Us | Cloud Services
TENESYS
Poland
B
11-50 Employees
2015
Key takeaway
Tenesys emphasizes the importance of data security in cloud computing, offering cloud security services that utilize proven practices to ensure that businesses are protected as their needs evolve.
Reference
Service
Cloud security services | Tenesys
We understand that data security is crucial. That's why we provide solutions based only on proven practices, so you can be sure that your business is protected.
Looking for more accurate results?
Find the right companies for free by entering your custom query!
25M+ companies
250M+ products
Free to use
GATECH S.A.
Wrocław, Poland
B
1-10 Employees
2014
Key takeaway
Identity Secure emphasizes its commitment to safeguarding personal data through a secure cloud infrastructure, particularly for medical data management. Additionally, Secure Hosting Solutions offers high-security data hosting services and cloud environment development, ensuring robust protection against data breaches and unauthorized access.
Reference
Core business
GATECH S.A. Specialized IT Services: IoT and Cloud Solutions
A specialized company for special tasks. Security, availability, Internet of Things, Hosting, virtual environments. Everything in one place.

ZawCloud
Poland
B
1-10 Employees
2021
Key takeaway
ZawCloud has established strong relationships with various hosting providers globally, ensuring reliable server management.
Reference
Core business
ZawCloud -
eCloudChain
Różopole, Poland
B
11-50 Employees
-
Key takeaway
eCloudChain emphasizes its expertise in Cloud Managed Services and Cloud Migration, which are integral to enhancing operational efficiency and security. Their approach as a trusted cloud system integrator helps organizations lower operational costs and reduce compliance risks while implementing best industry practices.
Reference
Core business
Cloud Transformation : Successful Planning & Execution
We work with you as a trusted Cloud system integrator partner to build strong organization capabilities to lower operational costs, improve security, reduce compliance risks and focus on the best industry practices.
Securing
Krakow, Poland
B
11-50 Employees
2003
Key takeaway
The company specializes in IT security, offering expertise in cloud computing security, including a detailed explanation of the Cloud Shared Responsibility Model and security tips for AWS. Their services include dedicated training and workshops that emphasize best practices for securing applications and systems throughout the development process.
Reference
Core business
Securing - more than security testing
We help to achieve appropriate level of applications and systems security. More than security testing.
PANDORA COGNITIVE CYBERSECURITY S.A.
Gdynia, Poland
B
251-500 Employees
-
Key takeaway
Pandora Cognitive Cybersecurity focuses on advanced cybersecurity solutions, utilizing artificial intelligence and machine learning to enhance threat detection and response. Their systems, like the Autonomous Data Traffic Analyzer, are designed to monitor and analyze data traffic, making it particularly relevant for addressing security challenges in cloud computing environments.
Reference
Core business
Pandora Cognitive Cybersecurity
Scramjet
Suwałki, Poland
B
11-50 Employees
2020
Key takeaway
The Scramjet Cloud Platform offers a robust serverless data processing solution that facilitates secure and efficient data management across distributed environments. With features like isolated Spaces for data Topics and a unified control panel, the platform enhances data integration and transfer, making it ideal for developers seeking to streamline their data ecosystems.
Reference
Core business
Distributed Data Processing Platform | Scramjet
The real-time data integration platform created by devs, for devs. Leverage all the data from anywhere in the world, now in an easier and faster way.
CloudPanda.io
Poland
B
1-10 Employees
-
Key takeaway
The company, CloudPanda, emphasizes its commitment to ensuring seamless cloud migration and ongoing infrastructure maintenance and support. With over 10 years of experience, they provide comprehensive services that enhance cloud security and efficiency, allowing businesses to focus on their core operations.
Reference
Core business
CloudPanda.io - Cloud solutions and DevOps services
Technologies which have been searched by others and may be interesting for you:
A selection of suitable products and services provided by verified companies according to your search.
Service
Product Security
Go to product

Product
enclaive vHSM
Go to product

Service
EMCP
Go to product

Service
Cloud Hosting
Go to product
A selection of suitable use cases for products or services provided by verified companies according to your search.
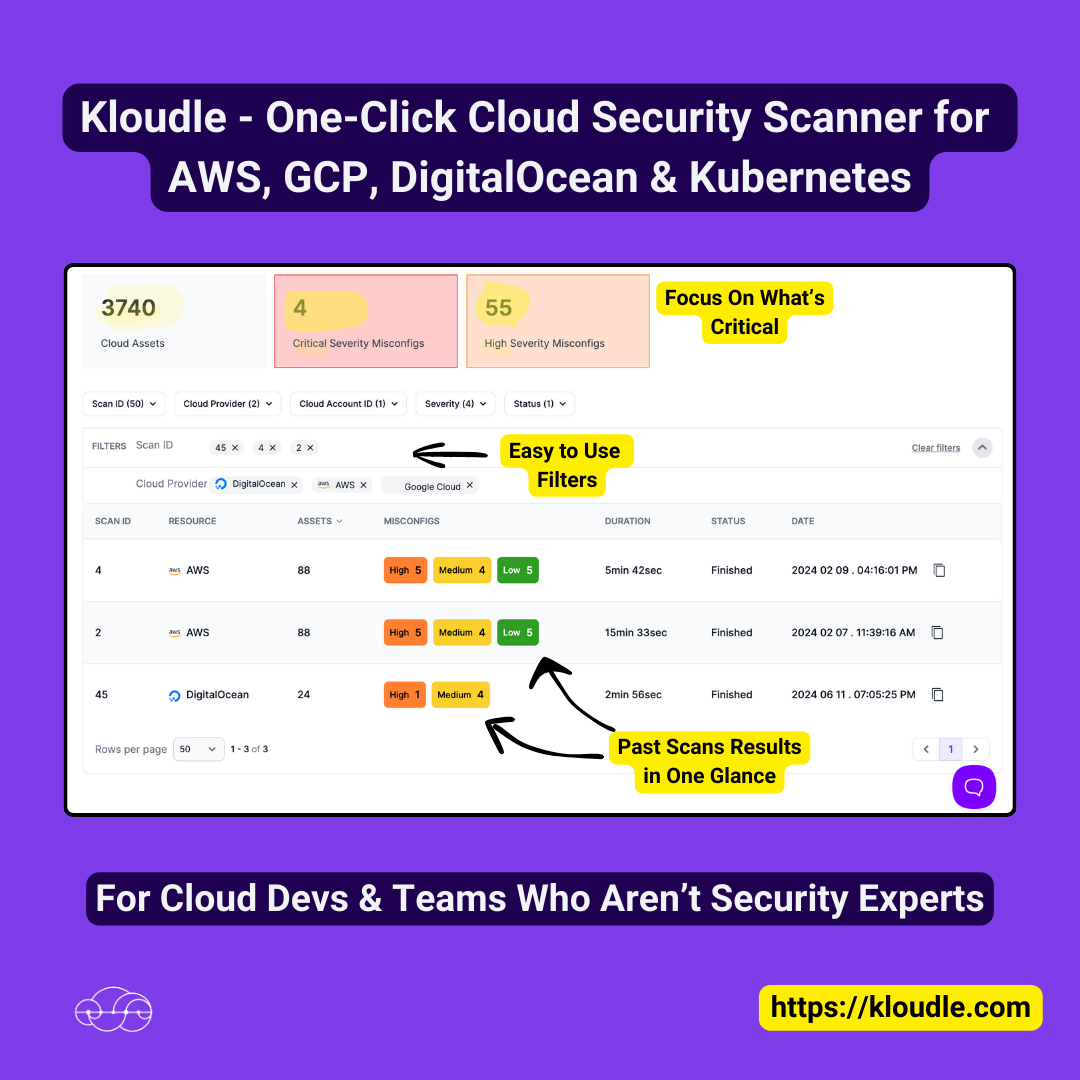
Use case
Comprehensive Cloud Security Management with Kloudle
software
Kloudle enables businesses to protect their cloud environments efficiently by offering a comprehensive cloud security posture management system. It scans for over 350 potential security issues and provides actionable solutions, all without requiring specialized expertise. Major cloud providers such as AWS, Google Cloud, DigitalOcean, Azure, and Kubernetes are supported, ensuring broad compatibility and robust security management. With user-friendly features including a centralized dashboard, actionable insights, rapid scan results, and comprehensive reporting, Kloudle empowers users to maintain a secure cloud environment effortlessly.

Use case
Comprehensive Cloud Security Management with Kloudle
software
Kloudle enables businesses to protect their cloud environments efficiently by offering a comprehensive cloud security posture management system. It scans for over 350 potential security issues and provides actionable solutions, all without requiring specialized expertise. Major cloud providers such as AWS, Google Cloud, DigitalOcean, Azure, and Kubernetes are supported, ensuring broad compatibility and robust security management. With user-friendly features including a centralized dashboard, actionable insights, rapid scan results, and comprehensive reporting, Kloudle empowers users to maintain a secure cloud environment effortlessly.
In Poland, the Cloud Computing Security industry is shaped by several key considerations. Regulatory compliance is paramount, particularly with the implementation of the General Data Protection Regulation (GDPR), which mandates strict data handling and privacy practices. Organizations must ensure that their cloud providers adhere to these regulations to avoid hefty fines. The landscape presents unique challenges such as managing data sovereignty issues, as companies must understand where their data is stored and the implications of local laws. Opportunities abound in Poland due to the growing demand for secure cloud solutions driven by digital transformation across various sectors. The competitive landscape is evolving, with both local firms and global players vying for market share, leading to innovation and advancements in security technologies. Furthermore, as businesses increasingly migrate to the cloud, the demand for specialized security services continues to rise, creating a robust market for solution providers. Environmental concerns also play a role, as companies are urged to adopt sustainable practices in their operations, including energy-efficient data centers. Understanding these aspects is crucial for anyone researching companies in the Cloud Computing Security sector in Poland, as they highlight the interplay between compliance, market demand, and innovation in a rapidly changing technological environment.
Some interesting numbers and facts about your company results for Cloud Computing Security
| Country with most fitting companies | Poland |
| Amount of fitting manufacturers | 36 |
| Amount of suitable service providers | 28 |
| Average amount of employees | 11-50 |
| Oldest suiting company | 2003 |
| Youngest suiting company | 2021 |
Some interesting questions that has been asked about the results you have just received for Cloud Computing Security
What are related technologies to Cloud Computing Security?
Based on our calculations related technologies to Cloud Computing Security are Big Data, E-Health, Retail Tech, Artificial Intelligence & Machine Learning, E-Commerce
Who are Start-Ups in the field of Cloud Computing Security?
Start-Ups who are working in Cloud Computing Security are ZawCloud
Which industries are mostly working on Cloud Computing Security?
The most represented industries which are working in Cloud Computing Security are IT, Software and Services, Other, Cyber Security, Education
How does ensun find these Cloud Computing Security Companies?
ensun uses an advanced search and ranking system capable of sifting through millions of companies and hundreds of millions of products and services to identify suitable matches. This is achieved by leveraging cutting-edge technologies, including Artificial Intelligence.