
The B2B platform for the best purchasing descision. Identify and compare relevant B2B manufacturers, suppliers and retailers
Close
Filter
Result configuration
Continents
Select continent
Locations
Result types
Company type
Select company type
Industries
Select industry
Company status
Select company status preset
Number of employees
Min.
Max.
Founding year
Kudelski IoT
Cheseaux-sur-Lausanne, Switzerland
A
1001-5000 Employees
1951
Key takeaway
The company's extensive expertise in IoT security, built over three decades, emphasizes a holistic approach that ensures secure by design solutions. They offer a range of IoT security services, including evaluations, certifications, and continuous firmware monitoring, which are crucial for the long-term success and sustainability of IoT businesses.
Reference
Core business
IoT Services & Solutions, Secure by Design
No matter where you are on your IoT journey, we have the expertise, the technology and the solutions to help you succeed.
IoT Defense
Falls Church, United States
B
1-10 Employees
2015
Key takeaway
The company is dedicated to securing the Internet of Things (IoT) through innovative products like RATtrap, which addresses emerging cyber threats such as ransomware. They emphasize the importance of robust security for IoT devices, recognizing the market's potential for growth as these devices become more prevalent in homes and businesses.
Reference
Core business
IoT Defense - Internet Security Product and Threat Research
asvin.io
Stuttgart, Germany
A
1-10 Employees
-
Key takeaway
Asvin emphasizes the critical importance of securing IoT and IIoT devices, which are vulnerable to cyberattacks due to common security oversights. The company has developed a comprehensive platform that utilizes advanced cryptographic algorithms to protect these devices from various threats, ensuring their safety and functionality.
Reference
Core business
We provide the highest level of security for IoT and IIoT
Trusted and secure IoT and IIoT lifecycle management for software supply chains. Learn more about asvin's Cybersecurity Management System.
Looking for more accurate results?
Find the right companies for free by entering your custom query!
25M+ companies
250M+ products
Free to use
IoT Security Initiative
Austin, United States
B
1-10 Employees
2015
Key takeaway
The IoT Security Initiative offers extensive guidance and tools to ensure security and privacy in IoT products and systems. It provides actionable materials for practitioners to understand threats and vulnerabilities, allowing for effective security controls to protect various types of IoT assets.
Reference
Core business
.. IoT Security Initiative Overview
Security Pattern
Italy
B
1-10 Employees
2017
Key takeaway
The company emphasizes its commitment to IoT security through ongoing research and development in cryptography and active participation in standardization bodies. They have developed the IoT Secure Suite®, which provides robust security solutions for intelligent connected devices, ensuring sustainable protection against current threats.
Reference
Service
Security Pattern | Embedded security by design
We help creators of smart and connected devices (in the field of automotive, home automation, industrial and medical) to design, develop and operate their systems with the proper level of protection and to keep them protected over time.
Crypto Quantique
London, United Kingdom
A
11-50 Employees
2016
Key takeaway
Crypto Quantique specializes in end-to-end IoT security, offering innovative products that integrate security measures throughout the supply chain. Their patented software platform and unique quantum-driven secure silicon chip design address vulnerabilities in existing IoT systems, making them a key player in the IoT security landscape.
Reference
Core business
IoT security Archives - Crypto Quantique
semphos
Newcastle upon Tyne, United Kingdom
A
1-10 Employees
2019
Key takeaway
The company utilizes AWS-IoT for device management, ensuring efficient handling of millions of devices while maintaining a focus on cost-effectiveness. Their expertise in designing IoT devices based on ESP32, from component selection to PCB design and testing, highlights their capability in developing secure and scalable IoT solutions.
Reference
Service
IoT Services
Iotabeam, Inc.
Palo Alto, United States
B
1-10 Employees
2017
Key takeaway
The company specializes in IoT security, particularly for low-end, low-power endpoint devices, allowing for the integration of security measures without the need for hardware redesign or changes to existing infrastructure. Their expertise spans various IoT platforms and technologies, making them well-equipped to enhance security in both new and retrofitted systems.
Reference
Core business
iotaBEAM - Iot Security, Low Power Sensors, Iot Devices
IoT security for low-end, low power IoT endpoint devices with no need for hardware redesign or change in infrastructure,
SmartAxiom
Irvine, United States
B
11-50 Employees
2016
Key takeaway
SmartAxiom specializes in IoT security by utilizing decentralized blockchain technology to protect devices and data, enhancing security and efficiency in edge computing networks. Their innovative platform integrates advanced insights and secure connections for IoT devices, focusing on device identification, authentication, and data integrity.
Reference
Product
IoT Security Product base on Blockchain Technology - SmartAxiom
IoT Security Product base on Blockchain Technology
Praetorian
Austin, United States
B
51-100 Employees
2011
Key takeaway
The company specializes in IoT security, offering expertise to strengthen the security of IoT products from chip to cloud, ensuring that devices and data are protected throughout the entire supply chain. Their security team emulates attackers to identify vulnerabilities and safeguard critical infrastructure, making them a trusted partner for organizations looking to enhance their IoT security initiatives.
Reference
Service
IoT Security - Praetorian
Gain confidence that your IoT devices and data are secure, throughout the entire supply chain, with our IoT security experts.
Technologies which have been searched by others and may be interesting for you:
A selection of suitable products and services provided by verified companies according to your search.

Service
IoT development services
Go to product
A selection of suitable use cases for products or services provided by verified companies according to your search.
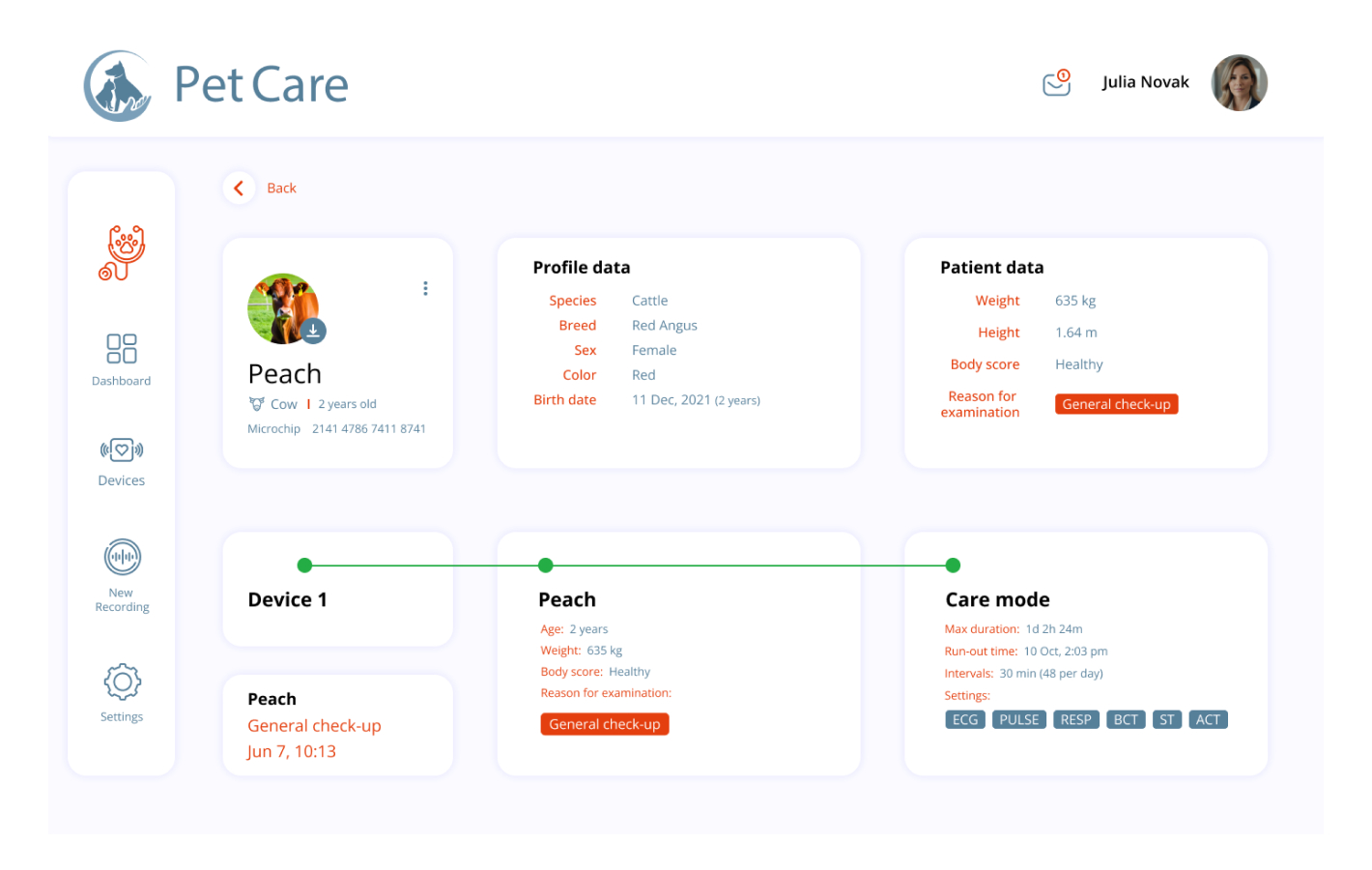
Use case
A platform for vital farm animals signs monitoring
Healthcare
The Client develops a technology incorporated in a matchbox-sized wearable device allowing precise measurement of medically relevant vital data of farm animals. The Client is a MedTech company that developed innovative technology for animal healthcare, focusing on a wearable device that offers precise measurement of vital data in animals. Location: Switzerland. Industry: MedTech, Medicine, Veterinary. Team size: Up to 18 team members Project duration: 3+ years

Use case
A platform for vital farm animals signs monitoring
Healthcare
The Client develops a technology incorporated in a matchbox-sized wearable device allowing precise measurement of medically relevant vital data of farm animals. The Client is a MedTech company that developed innovative technology for animal healthcare, focusing on a wearable device that offers precise measurement of vital data in animals. Location: Switzerland. Industry: MedTech, Medicine, Veterinary. Team size: Up to 18 team members Project duration: 3+ years
IoT security refers to the measures and protocols implemented to protect Internet of Things (IoT) devices and networks from cyber threats. As IoT devices become increasingly prevalent, ensuring their security is vital to prevent unauthorized access, data breaches, and potential disruptions. These security measures often include encryption, secure authentication, and regular software updates. With the vast number of interconnected devices, maintaining robust security protocols is essential to safeguard sensitive information and ensure the integrity of the systems in which these devices operate.
IoT Security utilizes multiple strategies to safeguard connected devices from various threats. One key method involves implementing robust encryption protocols, which protect data transmission between devices and servers, ensuring that sensitive information remains confidential. Additionally, secure authentication processes are vital, as they verify the identity of devices before granting access to networks. Regular software updates and patches help to address vulnerabilities, while monitoring systems detect unusual activities, allowing for quick responses to potential breaches. This multi-layered approach enhances the overall security of IoT devices, reducing the risk of cyberattacks.
One of the primary challenges in IoT security is the vast number of devices that are often deployed without adequate security measures. Each device can serve as a potential entry point for cyber threats, making it difficult to maintain a consistent security posture across all endpoints. Another significant concern is data privacy. With devices collecting sensitive information, ensuring that data is encrypted and protected from unauthorized access is critical. Additionally, the lack of standardized protocols across different manufacturers leads to vulnerabilities, making it essential for providers to establish robust security frameworks tailored to IoT environments.
IoT security is crucial for businesses as it protects sensitive data and ensures the integrity of connected devices. With the growing number of Internet of Things (IoT) devices, vulnerabilities increase, making organizations more susceptible to cyberattacks. A breach can lead to significant financial losses, reputational damage, and legal ramifications. Moreover, robust IoT security measures help maintain customer trust and compliance with regulations. As businesses increasingly rely on connected technologies for operations, safeguarding these systems becomes essential for sustaining productivity and ensuring a competitive edge in the market.
1. Device Authentication
This solution ensures that only authorized devices can connect to the IoT network, preventing unauthorized access and potential data breaches.
2. Data Encryption
Data encryption protects sensitive information transmitted between devices by converting it into an unreadable format, ensuring that even if data is intercepted, it cannot be accessed by unauthorized parties.
3. Network Security
Implementing robust network security measures, such as firewalls and intrusion detection systems, helps safeguard the entire IoT ecosystem from external threats and attacks.
4. Regular Software Updates
Keeping IoT devices up to date with the latest software patches is crucial for fixing vulnerabilities and enhancing security features against emerging threats.
5. Threat Detection and Response
Advanced monitoring solutions can identify anomalies and respond to potential security incidents in real-time, allowing for swift action to mitigate risks.
Some interesting numbers and facts about your company results for IoT Security
| Country with most fitting companies | United States |
| Amount of fitting manufacturers | 10000 |
| Amount of suitable service providers | 10000 |
| Average amount of employees | 1-10 |
| Oldest suiting company | 1951 |
| Youngest suiting company | 2019 |
20%
40%
60%
80%
Some interesting questions that has been asked about the results you have just received for IoT Security
What are related technologies to IoT Security?
Based on our calculations related technologies to IoT Security are Big Data, E-Health, Retail Tech, Artificial Intelligence & Machine Learning, E-Commerce
Which industries are mostly working on IoT Security?
The most represented industries which are working in IoT Security are IT, Software and Services, Defense, Other, Telecommunications, Electronics and Electrical engineering
How does ensun find these IoT Security Companies?
ensun uses an advanced search and ranking system capable of sifting through millions of companies and hundreds of millions of products and services to identify suitable matches. This is achieved by leveraging cutting-edge technologies, including Artificial Intelligence.