
The B2B platform for the best purchasing descision. Identify and compare relevant B2B manufacturers, suppliers and retailers
Close
Filter
Result configuration
Continents
Select continent
Locations
Result types
Company type
Select company type
Industries
Select industry
Company status
Select company status preset
Number of employees
Min.
Max.
Founding year
CYBER.SO-Cyber Services HK
China
D
1-10 Employees
2020
Key takeaway
Cyber Services is a global provider specializing in advanced cybersecurity measures and safeguards to protect confidential data and electronic assets. They employ sophisticated countermeasures and state-of-the-art tools to detect and prevent cyberattacks, ensuring the integrity of their clients' data.
Reference
Core business
Digital Cybersecurity Agency | Cyber Services HK
Cyber.so-Cyber Services HK - International Digital Security Agency offers solutions based on highest intelligence-Identification of Corruption, Bribery,Money Laundry.Investigating into Financial Markets crime.CryptoCurency crime. Identification of Fraud. Deep Due Diligence. Asset Tracing and Recovery.OSINT
ThreatAgility
Huangpu District, China
D
1-10 Employees
2020
Key takeaway
ThreatAgility specializes in AI-driven automotive cybersecurity, focusing on creating self-aware and secure vehicles. Their innovative approach includes intelligent attack simulations that generate detailed cybersecurity requirements, enhancing vehicle safety and resilience against cyber threats.
Reference
Core business
Agile, Automotive Cybersecurity - ThreatAgility
Agile, intelligent cybersecurity, woven into the lifecycle of connected vehicles. ThreatAgility’s unique AI-driven platform enables self-aware, cybersecure vehicles.

北京微步在线科技有限公司
Dongcheng District, China
D
11-50 Employees
-
Key takeaway
ThreatBook is a leading provider of cybersecurity solutions, offering a range of SaaS-based threat intelligence products that enhance threat detection and response across cloud, network, and endpoints.
Reference
Product
Cyber Security Solutions_Security Operation | ThreatBook
Looking for more accurate results?
Find the right companies for free by entering your custom query!
25M+ companies
250M+ products
Free to use
CYPHER
Kowloon, China
D
1-10 Employees
-
Key takeaway
CYPHER is a cyber security consultancy that offers intelligence-based security assessments, helping clients identify vulnerabilities through realistic hacker simulations. Their tailored solutions make cyber security services more accessible, particularly for SMEs.
Reference
Core business
Cypher | Security Testing, Security Consultant, Ethical Hacking
Huge Crown Technology Limited
Hong Kong Island, China
D
11-50 Employees
2013
Key takeaway
HCTL offers comprehensive cybersecurity solutions that encompass data protection, network security, IoT security, and identity and access management, ensuring robust security for your business. Their team provides consultative assistance and services, including advanced network analysis and security policy consultation.
Reference
Service
IT Consulting | Huge Crown Technology
From data protection to network security, from IoT security to Trust management and Identity and Access Management, discover how HCTL cybersecurity hardware and software solutions ensure the ultimate security for your business.
Sangfor Technologies
Shenzhen, China
D
1001-5000 Employees
2000
Key takeaway
Sangfor Technologies specializes in cybersecurity services, offering a range of solutions including threat identification, incident response, and security assessments, all developed to meet the real-world needs of customers.
Reference
Service
Cyber Security Services | Sangfor Technologies
On demand threat identification, analysis and risk management services

怡和科技(上海)有限公司
Huangpu District, China
D
1-10 Employees
-
Key takeaway
HKBNES, a leading telecom and IT system integration provider, offers Aegis Intelligence solutions that help businesses effectively address security threats and enhance their IT infrastructure.
Reference
Product
Aegis Intelligence | HKBN Enterprise Solutions
Aegis Intelligence 提供解決方案,幫助你有效應對頻寬短缺與安全威脅,推動數碼轉型,優化 IT 基礎架構。
Systex
Hong Kong Island, China
D
1001-5000 Employees
1997
Key takeaway
Systex specializes in integrated application solutions and has established strategic partnerships with leading companies like Aqua Security, which offers a cloud-native endpoint protection platform designed to prevent breaches. Their extensive experience and commitment to technological advancement position them as a key player in the cybersecurity landscape.
Reference
Product
Aqua Security
Wynyard Group
Hong Kong Island, China
D
251-500 Employees
2011
Key takeaway
Wynyard Group specializes in advanced technology solutions, including Cyber Threat Analytics (CTA), which aggregates log data from connected devices to identify suspicious activity. Their commitment to research and development enhances their ability to provide effective cybersecurity measures for law enforcement agencies.
Reference
Service
Distributed SIEM Solution | Cyber Threat Analytics | Wynyard Group
Distributed SIEM solution by Wynyard Group aggregates log data from the various connected devices and filters them for suspicious activity
Hoplite Technology Ltd
Kowloon, China
D
1-10 Employees
2018
Key takeaway
Hoplite Tech emphasizes the importance of cybersecurity for everyday users, aiming to provide accessible tools that protect personal information and online identity. Their focus on enhancing cyber protection through innovative products and risk assessment solutions highlights their commitment to making cybersecurity a universal right.
Reference
Core business
Cyber Risk and Awareness Training Solution
Measure cyber security risk with automated risk assessment tools, for cyber insurance firms
Technologies which have been searched by others and may be interesting for you:
A selection of suitable products and services provided by verified companies according to your search.
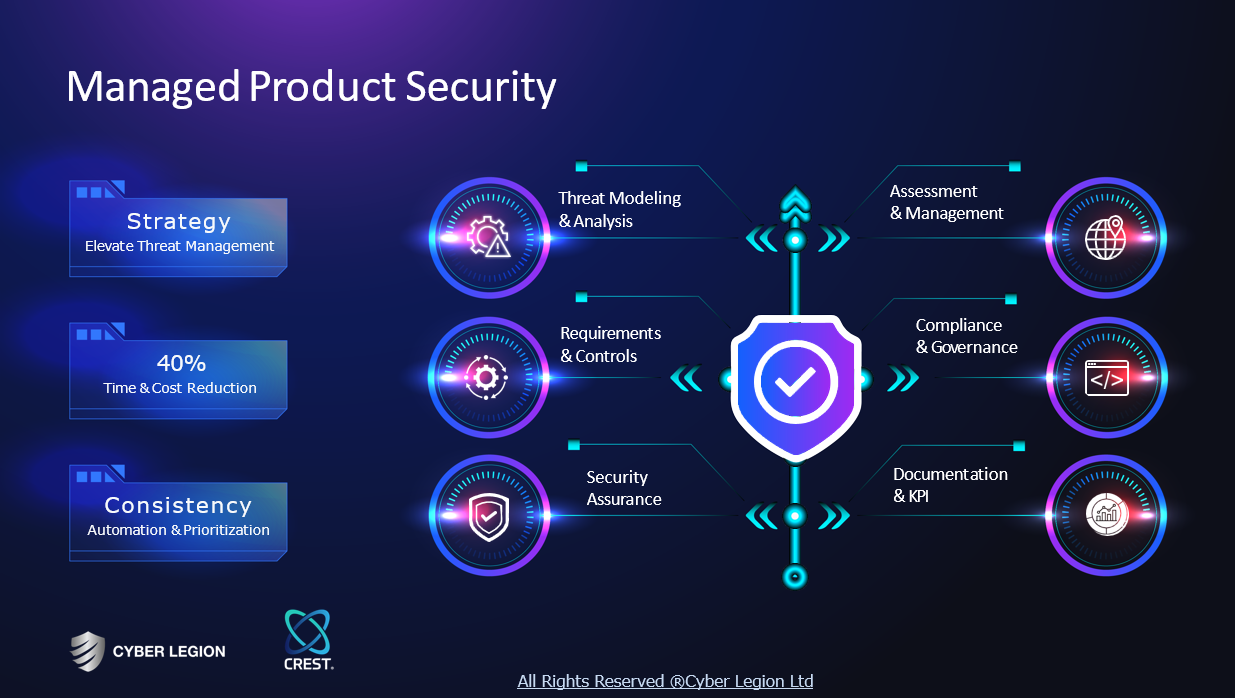
Service
Security Consultant
Go to product
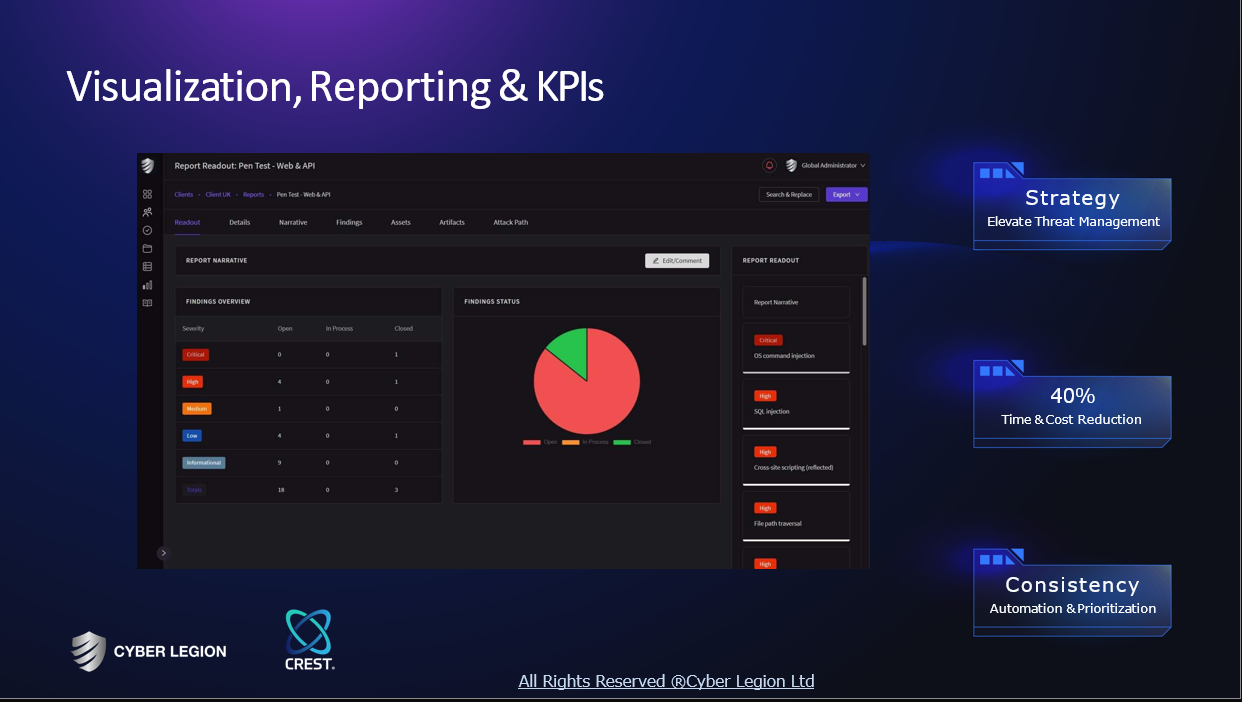
Service
Product Security
Go to product

Product
enclaive vHSM
Go to product

Service
EMCP
Go to product
A selection of suitable use cases for products or services provided by verified companies according to your search.

Use case
Cybersecurity
All
Cybersecurity is the act of protecting your digital assets against bad actors attack. This is a vast field which starts by identifying the risk in your industry and mitigating these risks on the best of your ability. There is always the probability that a bad actor will penetrate your defense system, in that case you should have in place a response plan. Are your digital assets protected?

Use case
Cybersecurity
All
Cybersecurity is the act of protecting your digital assets against bad actors attack. This is a vast field which starts by identifying the risk in your industry and mitigating these risks on the best of your ability. There is always the probability that a bad actor will penetrate your defense system, in that case you should have in place a response plan. Are your digital assets protected?
In the AI Cybersecurity industry in China, several key considerations are essential for anyone conducting research. First, regulatory frameworks are critical, as the Chinese government has implemented stringent cybersecurity laws that govern data protection and AI usage. Familiarity with these regulations is crucial for compliance and operational success. Challenges include a rapidly evolving threat landscape, where cybercrime tactics are becoming increasingly sophisticated, necessitating continuous innovation in AI technologies. Opportunities abound due to the growing demand for AI-driven cybersecurity solutions, particularly as businesses seek to protect sensitive data from breaches. The competitive landscape is marked by both established firms and startups, each vying for market share, which can result in a dynamic but crowded environment. Collaborations between tech companies and government entities can also facilitate advancements and access to resources. Environmental concerns are increasingly relevant, as the tech industry faces scrutiny over its carbon footprint and energy consumption. Sustainable practices are becoming a priority for companies aiming to align with global trends. Lastly, global market relevance cannot be overlooked, as Chinese firms are increasingly looking to expand internationally, positioning themselves as key players in the global AI Cybersecurity arena. Understanding these factors can provide valuable insights for navigating the complexities of this emerging industry in China.
Some interesting numbers and facts about your company results for AI Cybersecurity
| Country with most fitting companies | China |
| Amount of fitting manufacturers | 76 |
| Amount of suitable service providers | 65 |
| Average amount of employees | 11-50 |
| Oldest suiting company | 1997 |
| Youngest suiting company | 2020 |
Some interesting questions that has been asked about the results you have just received for AI Cybersecurity
What are related technologies to AI Cybersecurity?
Based on our calculations related technologies to AI Cybersecurity are Big Data, E-Health, Retail Tech, Artificial Intelligence & Machine Learning, E-Commerce
Which industries are mostly working on AI Cybersecurity?
The most represented industries which are working in AI Cybersecurity are IT, Software and Services, Other, Electronics and Electrical engineering, Telecommunications, Defense
How does ensun find these AI Cybersecurity Companies?
ensun uses an advanced search and ranking system capable of sifting through millions of companies and hundreds of millions of products and services to identify suitable matches. This is achieved by leveraging cutting-edge technologies, including Artificial Intelligence.