
The B2B platform for the best purchasing descision. Identify and compare relevant B2B manufacturers, suppliers and retailers
Close
Filter
Result configuration
Continents
Select continent
Locations
Result types
Company type
Select company type
Industries
Select industry
Company status
Select company status preset
Number of employees
Min.
Max.
Founding year
Hive Health
London, United Kingdom
A
1-10 Employees
2021
Key takeaway
Hive Health is a cyber security company dedicated to protecting healthcare through a focus on clinical risk and patient safety. They provide essential security functions like threat detection and risk management, offering a platform that enhances visibility and understanding of IoT devices, thereby ensuring compliance and safeguarding critical infrastructure.
Reference
Core business
Home - Hive Health
Cyber security for healthcare. Protect your critical infrastructure, connected devices and patient data with Hive
Alexio Corporation
Markham, Canada
A
11-50 Employees
2017
Key takeaway
The company, Alexio, addresses the critical cybersecurity needs of healthcare practices, particularly in the face of rising threats like ransomware and data theft. They offer a pioneering "Cybersecurity-as-a-Service" model that provides access to expert tools and solutions, ensuring that healthcare providers can protect their data and systems effectively, regardless of their size.
Reference
Core business
Dental/Medical Cybersecurity Solutions
Healthcare practices have big challenges with cybersecurity, protecting data and maintaining business systems. Alexio Defender is Canada's award-winning solution.
Medicare Network
London, United Kingdom
A
11-50 Employees
2005
Key takeaway
Medicare Network is dedicated to enhancing the cybersecurity culture within healthcare organizations by providing innovative cyber security solutions and services tailored to meet regulatory and compliance standards. With a focus on protecting medical facilities and pharmaceutical organizations from digital and physical threats, the company emphasizes collaboration with healthcare entities to effectively manage and mitigate risks.
Reference
Core business
Cybersecurity | Medicare Network | United Kingdom
Medicare Network is a global cyber security services company specializing in cybersecurity, risk management and managed security services.
Looking for more accurate results?
Find the right companies for free by entering your custom query!
25M+ companies
250M+ products
Free to use
BlackRidge Technology
Reno, United States
B
11-50 Employees
2010
Key takeaway
BlackRidge provides advanced cyber security solutions specifically designed to protect enterprise networks and cloud services, addressing the growing threat of cyber-attacks in the healthcare sector. Their identity-based, zero trust approach enhances data protection for sensitive patient information, which is increasingly vulnerable due to legacy systems and interconnected devices.
Reference
Product
Healthcare | BlackRidge Technology
Cyber security has become a dominant issue in healthcare. The high value of patient and proprietary information, often created and managed by legacy devices and systems that lack of effective security access controls, is exposing members of the healthcare continuum to an increasing threat of cyber-attacks. As healthcare systems and clinical devices now produce and manage more sensitive patient health information than ever before, even the savviest CISO’s are challenged to protect this data as these systems become more connected and the regulatory environment continues to shift.
ITHealth
Gedling, United Kingdom
A
11-50 Employees
1992
Key takeaway
ITHealth specializes in cybersecurity solutions for NHS organizations, emphasizing their commitment to protecting systems, data, and staff. With Cyber Essentials Plus accreditation and a focus on ensuring safe and efficient care delivery, ITHealth empowers healthcare providers to maintain the integrity of their digital operations.
Reference
Core business
ITHealth | Protect patient safety with proven cyber security
Keeping NHS systems and data secure, easy to access and simple to manage, so healthcare providers can continue to function optimally.
CYBERSALUS
Reston, United States
B
11-50 Employees
2012
Key takeaway
CyberSalus is dedicated to addressing healthcare cybersecurity challenges, allowing medical staff to concentrate on patient care. With expertise in protecting IoT and OT devices, CyberSalus offers comprehensive security solutions that leverage AI and a zero-trust framework to safeguard healthcare organizations from emerging threats.
Reference
Core business
CyberSalus – 360 Degrees of Cyber Protection
Titania Ltd
Worcester, United Kingdom
A
51-100 Employees
2009
Key takeaway
Titania is dedicated to enhancing healthcare cybersecurity through its Nipper solutions, which automatically map security checks to compliance frameworks and provide evidence of adherence to industry standards. With over a decade of experience supporting critical national infrastructure, Titania's Nipper software offers valuable insights for cyber leaders to identify and remediate vulnerabilities in network infrastructure.
Reference
Product
Healthcare Cybersecurity Solutions - Titania
Cyber Legion Ltd
London, United Kingdom
A
1-10 Employees
2021
Key takeaway
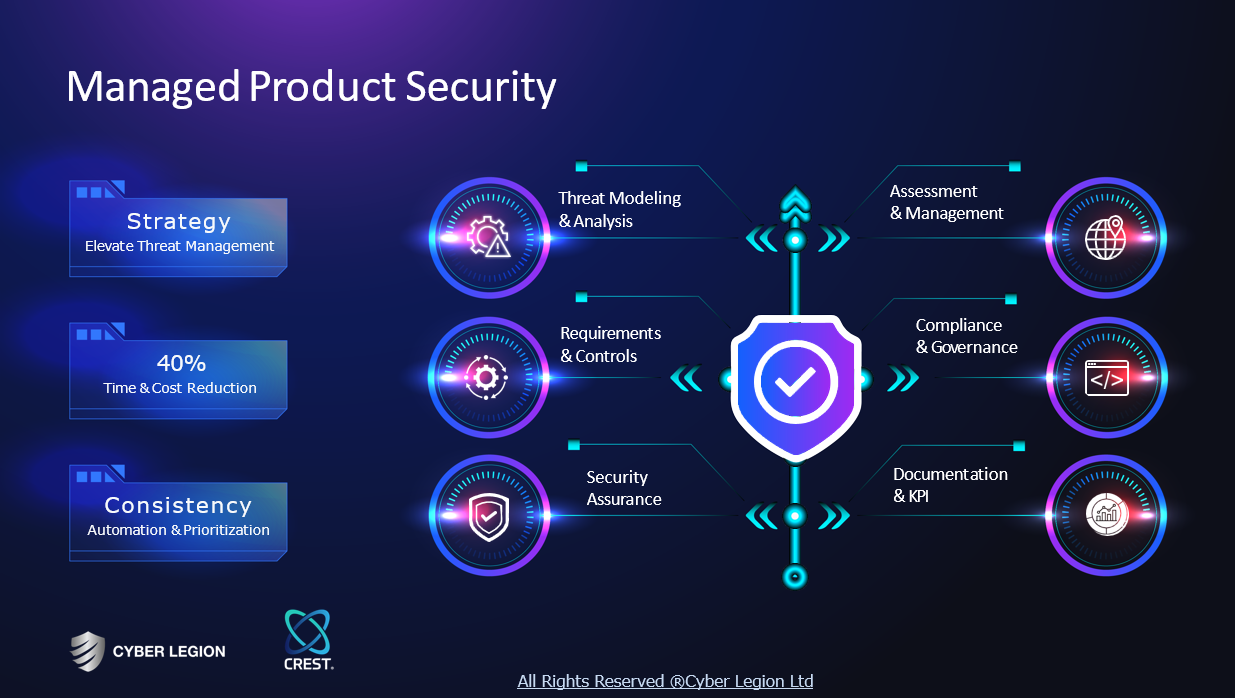
Cyber Legion Ltd is a UK-EU-based cybersecurity company that specializes in advanced cybersecurity testing and consultancy services, particularly focusing on the unique challenges posed by remote work environments. They are committed to enhancing cyber resilience and business continuity, making them a valuable partner for organizations looking to strengthen their cybersecurity posture.
Reference
Service
Security Consultant
At Cyber Legion, we are dedicated to providing top-notch cybersecurity consultancy to protect your business from evolving threats. Our offerings include a meticulous gap analysis and remediation strategy development, aimed at uncovering vulnerabilities and forging robust plans to mitigate them. Leveraging OSINT (Open Source Intelligence) and cutting-edge threat intelligence, we empower your organization to preemptively neutralize potential security threats. Moreover, we specialize in the formulation of Key Performance Indicators (KPIs) and deliver detailed reporting on your security infrastructure's efficacy. This enables you to monitor your cybersecurity posture's evolution and identify key areas for ongoing improvement. At Cyber Legion, we are dedicated to providing top-notch cybersecurity consultancy to protect your business from evolving threats. Our team of experts will work closely with you to develop a tailored security strategy that meets your specific needs. Contact us today for a free consultation! Staying ahead in security challenges and Get in Touch with Cyber Legion or Get a Free Quote
Exelegent
Freehold, United States
B
51-100 Employees
2009
Key takeaway
Exelegent is a specialized cybersecurity and compliance company that focuses on healthcare, providing essential services to safeguard sensitive information. With a dedicated team of security professionals and a commitment to industry standards like HIPAA and NIST, Exelegent helps healthcare organizations maintain a secure environment against evolving cyber threats.
Reference
Service
Cybercare for Healthcare - Exelegent
We Are Here to Make Your Life Secure Exelegent is committed to helping healthcare companies implement and maintain a secure environment. Our team of security professionals works 24/7 to ensure our clients are always ready for the continually evolving demands of cybersecurity. Why Healthcare? Healthcare organizations store an abundance of sensitive information that […]
Techumen Inc
New York, United States
B
11-50 Employees
2009
Key takeaway
Techumen specializes in simplifying healthcare security, focusing exclusively on protecting health information and navigating complex clinical workflows. Their expertise in healthcare regulations enables them to provide targeted risk management solutions, optimize security spending, and address privacy and security concerns, making them a vital partner for healthcare institutions.
Reference
Core business
Healthcare IT Security Company - Techumen
At our Healthcare IT Security Company, we have a thorough understanding that keeping all health information secure with help from industry...
Technologies which have been searched by others and may be interesting for you:
A selection of suitable products and services provided by verified companies according to your search.
Service
Security Consultant
Go to product

Service
EMCP
Go to product

Service
Cybersecurity
Go to product
A selection of suitable use cases for products or services provided by verified companies according to your search.

Use case
Cybersecurity
All
Cybersecurity is the act of protecting your digital assets against bad actors attack. This is a vast field which starts by identifying the risk in your industry and mitigating these risks on the best of your ability. There is always the probability that a bad actor will penetrate your defense system, in that case you should have in place a response plan. Are your digital assets protected?

Use case
Cybersecurity
All
Cybersecurity is the act of protecting your digital assets against bad actors attack. This is a vast field which starts by identifying the risk in your industry and mitigating these risks on the best of your ability. There is always the probability that a bad actor will penetrate your defense system, in that case you should have in place a response plan. Are your digital assets protected?
Healthcare cyber security refers to the protective measures and protocols implemented to safeguard sensitive medical data and systems from cyber threats. This field encompasses a variety of practices, including the use of firewalls, encryption, and authentication protocols to ensure that patient records, clinical data, and healthcare infrastructure remain secure against unauthorized access and breaches. As healthcare providers increasingly rely on digital systems for managing patient information, the importance of robust cyber security becomes paramount. Effective healthcare cyber security not only protects patient confidentiality but also maintains the integrity of healthcare operations, ensuring that critical services remain uninterrupted in the face of evolving cyber threats.
Healthcare Cyber Security is critical for hospitals and clinics due to the sensitive nature of patient data. Medical institutions handle vast amounts of personal health information, which makes them prime targets for cyberattacks. A successful breach can lead to unauthorized access to medical records, resulting in identity theft, insurance fraud, and even compromised patient care. Additionally, healthcare facilities are mandated to comply with regulations like HIPAA, which protect patient information. Failure to secure data not only risks patient trust but can also lead to substantial financial penalties and legal ramifications. Therefore, investing in robust cyber security measures is essential for safeguarding patient data and maintaining the integrity of healthcare services.
Healthcare organizations face numerous threats in the realm of cyber security. Ransomware attacks are particularly prevalent, where attackers encrypt critical data and demand payment for its release, potentially crippling operations. Another significant threat stems from phishing schemes, where malicious actors trick employees into revealing sensitive information, often through deceptive emails or messages. Additionally, data breaches pose a constant risk, as unauthorized access to patient records can lead to identity theft and loss of patient trust. These threats highlight the urgent need for robust cyber security measures in the healthcare sector.
Healthcare Cyber Security employs a variety of strategies to safeguard patient data from unauthorized access and breaches. By utilizing advanced encryption methods, sensitive information is transformed into a secure format, making it unreadable to those without the proper decryption keys. Additionally, implementing robust authentication protocols ensures that only authorized personnel can access patient records, which minimizes the risk of insider threats. Furthermore, continuous monitoring and threat detection systems are in place to identify and respond to potential cyber threats in real-time. Regular security assessments and updates to software and systems also help in closing vulnerabilities that could be exploited by cybercriminals. Overall, a comprehensive approach combining technology, policies, and employee training is essential for maintaining the integrity and confidentiality of patient data in the healthcare sector.
1. Conduct Regular Risk Assessments
Performing frequent evaluations of potential vulnerabilities in healthcare systems is crucial. This process helps identify weak points that could be exploited by cyber threats, allowing healthcare organizations to address these issues proactively.
2. Implement Strong Access Controls
Restricting access to sensitive information ensures that only authorized personnel can view or modify critical data. Utilizing multi-factor authentication and role-based access enhances security by adding layers of protection against unauthorized access.
3. Educate Staff on Security Awareness
Training employees on the latest cybersecurity threats and safe practices can significantly reduce the risk of human error. Regular workshops and updates on phishing scams and secure data handling will keep staff informed and vigilant.
4. Maintain Up-to-Date Software
Regularly updating software applications and systems ensures that security patches are applied promptly. This practice helps protect against known vulnerabilities that cybercriminals may exploit.
5. Develop an Incident Response Plan
Having a clear and tested incident response strategy enables organizations to react swiftly to cyber incidents. This plan should outline roles, responsibilities, and procedures to mitigate damage and restore operations efficiently.
Some interesting numbers and facts about your company results for Healthcare Cyber Security
| Country with most fitting companies | United States |
| Amount of fitting manufacturers | 10000 |
| Amount of suitable service providers | 10000 |
| Average amount of employees | 11-50 |
| Oldest suiting company | 1992 |
| Youngest suiting company | 2021 |
20%
40%
60%
80%
Some interesting questions that has been asked about the results you have just received for Healthcare Cyber Security
What are related technologies to Healthcare Cyber Security?
Based on our calculations related technologies to Healthcare Cyber Security are Big Data, E-Health, Retail Tech, Artificial Intelligence & Machine Learning, E-Commerce
Who are Start-Ups in the field of Healthcare Cyber Security?
Start-Ups who are working in Healthcare Cyber Security are Hive Health, Cyber Legion Ltd
Which industries are mostly working on Healthcare Cyber Security?
The most represented industries which are working in Healthcare Cyber Security are IT, Software and Services, Healthcare, Other, Defense, Medical
How does ensun find these Healthcare Cyber Security Companies?
ensun uses an advanced search and ranking system capable of sifting through millions of companies and hundreds of millions of products and services to identify suitable matches. This is achieved by leveraging cutting-edge technologies, including Artificial Intelligence.