
The B2B platform for the best purchasing descision. Identify and compare relevant B2B manufacturers, suppliers and retailers
Close
Filter
Result configuration
Continents
Select continent
Locations
Result types
Company type
Select company type
Industries
Select industry
Company status
Select company status preset
Number of employees
Min.
Max.
Founding year
AI Cyber Solutions
Orlando, United States
B
11-50 Employees
-
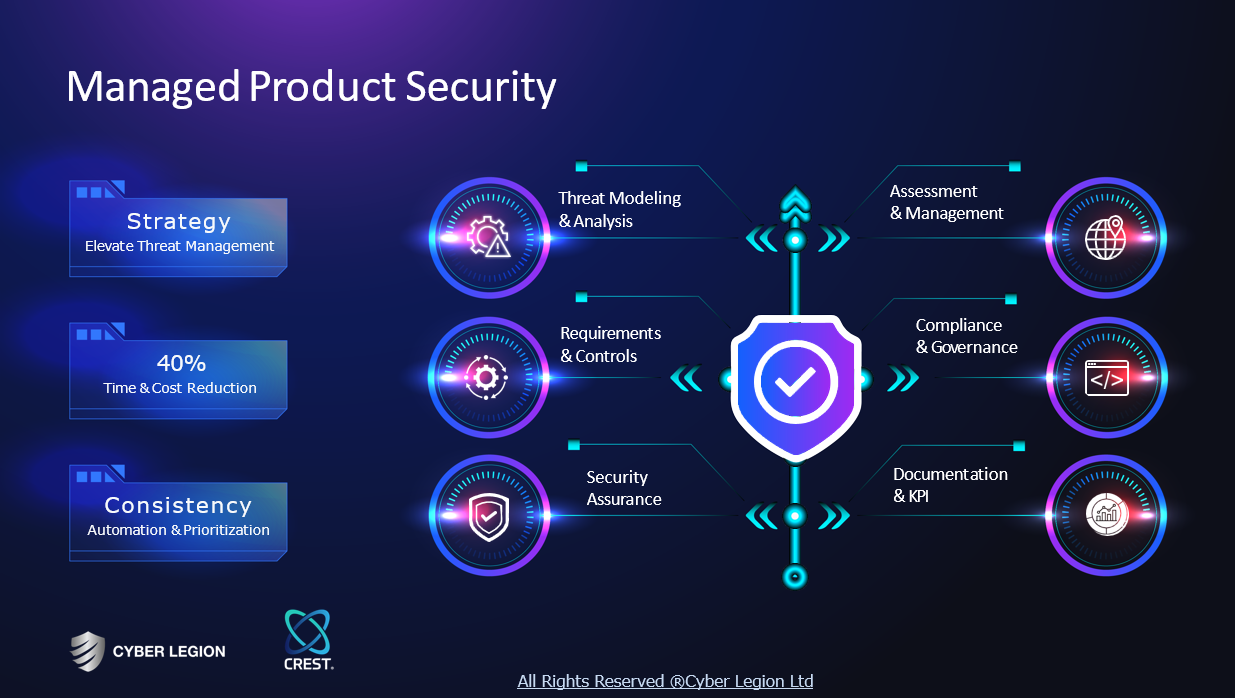
Key takeaway
AI Cyber Solutions offers advanced AI-based cybersecurity solutions that can quickly identify cyber threats and proactively detect issues before they occur. Their commitment to professionalism and easy integration ensures that businesses receive effective automation solutions tailored to their needs.
Reference
Core business
AI Cyber Solutions – AI Based Cyber Security Solutions in USA
AI Cyber Solutions is the top AI based cyber security solution provider in USA. Our objective is to provide you the right level of service at right time.
AiCyberWatch
Faridabad, India
D
51-100 Employees
2019
Key takeaway
AiCyberWatch, the cybersecurity initiative of NGBPS LIMITED, specializes in enhancing cyber security through innovative managed security and assessment services, addressing a wide range of needs from basic perimeter security to complex incident management. Their commitment to excellence and tailored solutions positions them as a leader in safeguarding businesses against evolving cyber threats.
Reference
Core business
Aicyberwatch Keeping You Ahead Of Cyber
AiCyberWatch is the leader in cyber security services and we're here to help you build a better cyber security posture. AiCyberWatch, combines Best of Breed Security Tools from world leaders like LogRhythm, Seceon, F5, Cloudflare, etc
ARIA Cybersecurity Solutions
-
51-100 Employees
1968
Key takeaway
ARIA Cybersecurity Solutions emphasizes its commitment to innovative security approaches, particularly in monitoring internal network traffic and enhancing existing security tools. Their experience and award-winning technology position them as a leading provider in the AI cybersecurity landscape, dedicated to strengthening defenses against potential breaches.
Reference
Core business
Cybersecurity Solution - Cloud Security Products | ARIA Cybersecurity
Improve cybersecurity with our award-winning ARIA SDS technology. We are a top cybersecurity provider committed to securing your digital world. Request a demo!
Looking for more accurate results?
Find the right companies for free by entering your custom query!
25M+ companies
250M+ products
Free to use
Ai Computing Systems
Mandaluyong, Philippines
D
11-50 Employees
-
Key takeaway
Ai Computing Systems Corporation offers tailored cybersecurity solutions and services, backed by a team of technical experts and partnerships with leading providers. They are recognized for their vulnerability assessment and penetration testing, emphasizing their commitment to addressing diverse security needs.
Reference
Service
Ai Computing Systems
Ambassadors Cyber Technology Ltd (ACT)
Lagos, Nigeria
E
1-10 Employees
2018
Key takeaway
Ambassadors Cyber Technology Ltd (ACT) is a prominent IT and OT security service provider in Nigeria, offering a range of cybersecurity solutions that include AI-driven security, vulnerability assessments, incident response, and data protection. Their collaboration with top cybersecurity vendors ensures they deliver innovative and comprehensive security services across various industries.
Reference
Product
Cyber Security Services & Solution | IT Security | ACT

Cyber Defence Service Ltd
United Kingdom
A
1-10 Employees
2016
Key takeaway
The company specializes in AI-driven cybersecurity solutions, particularly through its Overt AI system, which utilizes machine learning to enhance real-time situational awareness and detect adversary activities. Their expertise in cyber environments aims to reduce attack surfaces and bolster defenses for various sectors, including military and law enforcement.
Reference
Product
Overt Ai - Cyber Defence Service
AIShield
Bengaluru, India
D
11-50 Employees
2022
Key takeaway
AIShield, a Bosch start-up, focuses on securing AI systems and enhancing digital trust through its advanced technology that protects against adversarial attacks. Their AI Security product offers robust solutions for vulnerability assessment and defense, ensuring explainable and responsible AI systems.
Reference
Product
AIShield API Product | AI Security Solutions
API based AI Security Vulnerability assessment and defense
A I R
London, United Kingdom
A
1-10 Employees
2020
Key takeaway
AIR is a software tool that leverages AI to enhance cybersecurity by identifying and addressing the most critical threats, ultimately leading to safer environments. Its AI-driven risk reporting and incident management streamline workflows, making it a valuable solution for organizations focused on effective security risk management.
Reference
Product
Product | AIR
Alias IT
Melbourne, Australia
A
1-10 Employees
2006
Key takeaway
Alias IT specializes in cybersecurity consulting, architecture, and design services for both enterprise-scale and IoT technology systems, making it well-equipped to address AI cybersecurity needs.
Reference
Core business
Alias IT
McAfee Enterprise
-
1001-5000 Employees
-
Key takeaway
Skyhigh Security positions itself as a leader in cybersecurity, emphasizing that their approach integrates security into every digital initiative, enhancing rather than hindering transformation. Their focus on adaptive data protection and extending security to data use ensures that sensitive information is safeguarded effectively.
Reference
Product
AI Applications - Skyhigh Security
Technologies which have been searched by others and may be interesting for you:
A selection of suitable products and services provided by verified companies according to your search.
Service
Security Consultant
Go to product
Service
Product Security
Go to product

Product
enclaive vHSM
Go to product

Service
EMCP
Go to product
A selection of suitable use cases for products or services provided by verified companies according to your search.

Use case
Cybersecurity
All
Cybersecurity is the act of protecting your digital assets against bad actors attack. This is a vast field which starts by identifying the risk in your industry and mitigating these risks on the best of your ability. There is always the probability that a bad actor will penetrate your defense system, in that case you should have in place a response plan. Are your digital assets protected?

Use case
Cybersecurity
All
Cybersecurity is the act of protecting your digital assets against bad actors attack. This is a vast field which starts by identifying the risk in your industry and mitigating these risks on the best of your ability. There is always the probability that a bad actor will penetrate your defense system, in that case you should have in place a response plan. Are your digital assets protected?
AI Cybersecurity utilizes artificial intelligence technologies to enhance the protection of systems, networks, and data from cyber threats. By leveraging machine learning algorithms, these solutions can analyze vast amounts of data to identify patterns, detect anomalies, and respond to potential security breaches in real time. Additionally, AI Cybersecurity tools can adapt to evolving threats, improving defense mechanisms continuously without human intervention. This proactive approach allows organizations to stay ahead of cybercriminals, safeguarding sensitive information and maintaining operational integrity.
AI enhances threat detection in cybersecurity by utilizing advanced algorithms and machine learning techniques to analyze vast amounts of data in real time. By identifying patterns and anomalies that deviate from typical user behavior, AI systems can swiftly detect potential threats, including malware and phishing attacks. Additionally, these systems continuously learn from new threats and adapt their detection methods accordingly. This adaptability allows AI to improve its accuracy over time, reducing false positives and ensuring that security teams can focus on genuine threats. Overall, AI-driven threat detection provides a proactive approach to cybersecurity, significantly enhancing an organization's ability to respond to emerging risks.
1. Enhanced Threat Detection
AI in cybersecurity solutions significantly improves the ability to detect threats. By leveraging machine learning algorithms, these systems can analyze vast amounts of data in real-time, identifying patterns and anomalies that may indicate a security breach. This proactive approach allows organizations to respond to potential threats more swiftly and effectively.
2. Automated Response
Automation is another key advantage of AI integration in cybersecurity. AI-driven solutions can automatically respond to incidents, reducing the time taken to mitigate threats. This capability not only helps in minimizing damage but also frees up IT security personnel to focus on more strategic tasks, enhancing overall operational efficiency.
AI cybersecurity plays a crucial role in preventing data breaches by employing advanced algorithms to detect anomalies in network traffic and user behavior. By analyzing vast amounts of data in real-time, AI systems can identify patterns that signify potential threats, such as unauthorized access attempts or unusual data transfers. Furthermore, these systems can adapt and learn from new threats, continuously improving their detection capabilities. As a result, AI-driven cybersecurity solutions not only enhance the speed and accuracy of threat identification but also enable organizations to respond proactively to vulnerabilities, significantly reducing the risk of data breaches.
Implementing AI in cybersecurity presents several challenges that organizations must navigate. One significant issue is the complexity of integration, as combining AI systems with existing security infrastructure can be technically demanding and resource-intensive. This often requires specialized knowledge and skills, which may not be readily available within the organization. Another major challenge is data quality and availability. AI systems rely heavily on vast amounts of high-quality data to function effectively. In many cases, organizations may struggle to gather, clean, and maintain the necessary data, leading to potential inaccuracies in threat detection and response. Additionally, the evolving nature of cyber threats means that AI models must be continually updated and trained, which can strain resources and complicate implementation efforts.
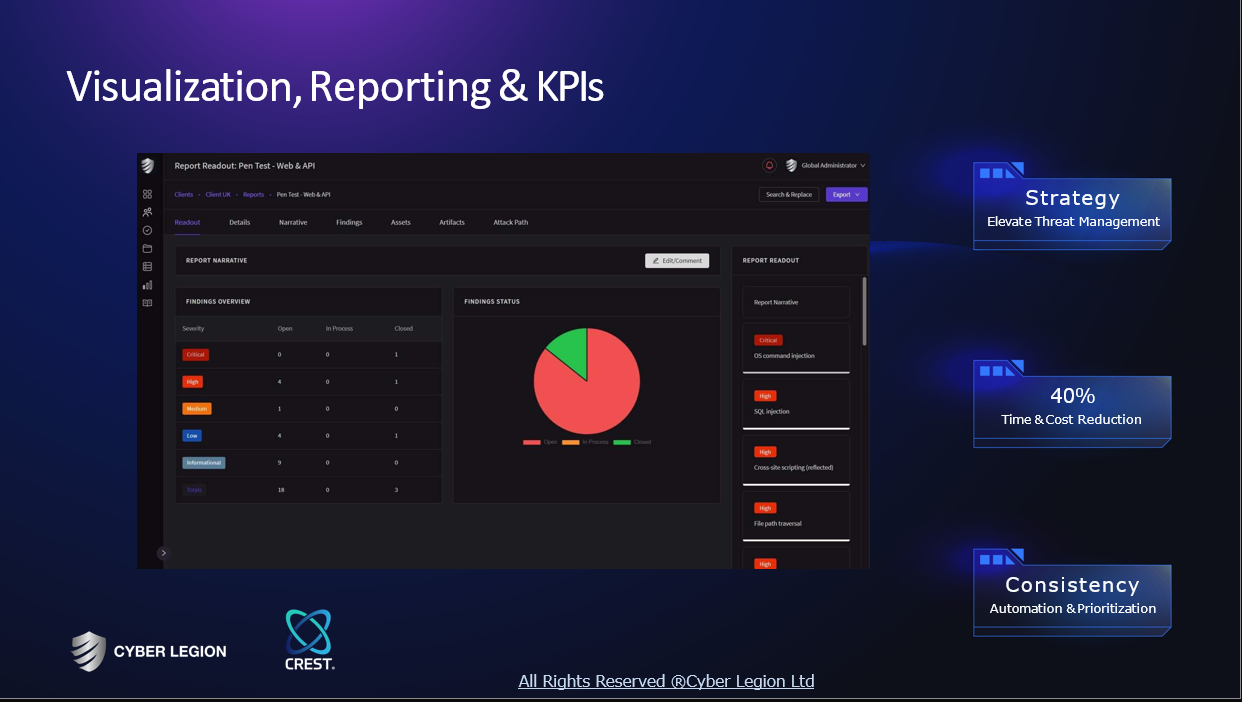
Some interesting numbers and facts about your company results for AI Cybersecurity
| Country with most fitting companies | United States |
| Amount of fitting manufacturers | 10000 |
| Amount of suitable service providers | 10000 |
| Average amount of employees | 11-50 |
| Oldest suiting company | 1968 |
| Youngest suiting company | 2022 |
20%
40%
60%
80%
Some interesting questions that has been asked about the results you have just received for AI Cybersecurity
What are related technologies to AI Cybersecurity?
Based on our calculations related technologies to AI Cybersecurity are Big Data, E-Health, Retail Tech, Artificial Intelligence & Machine Learning, E-Commerce
Who are Start-Ups in the field of AI Cybersecurity?
Start-Ups who are working in AI Cybersecurity are AIShield
Which industries are mostly working on AI Cybersecurity?
The most represented industries which are working in AI Cybersecurity are IT, Software and Services, Other, Defense, Consulting, Telecommunications
How does ensun find these AI Cybersecurity Companies?
ensun uses an advanced search and ranking system capable of sifting through millions of companies and hundreds of millions of products and services to identify suitable matches. This is achieved by leveraging cutting-edge technologies, including Artificial Intelligence.