
The B2B platform for the best purchasing descision. Identify and compare relevant B2B manufacturers, suppliers and retailers
Close
Filter
Result configuration
Continents
Select continent
Locations
Result types
Company type
Select company type
Industries
Select industry
Company status
Select company status preset
Number of employees
Min.
Max.
Founding year
PREBYTES
Leżajsk, Poland
B
11-50 Employees
2009
Key takeaway
PREBYTES offers a comprehensive Cyber Threat Intelligence Feed, which serves as a real-time source of information about online threats, essential for enhancing cybersecurity. Their solutions are designed to address key challenges that organizations face in protecting their operations from cyber risks.
Reference
Product
CTI Feed | Cyber Threat Intelligence Feed | PREBYTES
Cyber Threat Intelligence Feed - CTI Feed is an information database that provides up-to-date data on cyber threats.
PANDORA COGNITIVE CYBERSECURITY S.A.
Gdynia, Poland
B
251-500 Employees
-
Key takeaway
Pandora Cognitive Cybersecurity employs advanced artificial intelligence and machine learning to enhance threat intelligence by enabling immediate detection of suspicious data traffic through behavioral analysis. Their systems, including the Autonomous Data Traffic Analyzer, are designed to monitor and identify malicious activities, providing cybersecurity experts with powerful tools to respond to threats effectively.
Reference
Core business
Pandora Cognitive Cybersecurity
4Sync Solutions IT Security VAD
Warsaw, Poland
B
1-10 Employees
2010
Key takeaway
The company specializes in IT security and offers a comprehensive platform that includes threat detection and response, network traffic analysis, and digital forensics. Their solutions, such as Fidelis Network and Fidelis Endpoint, focus on proactive threat hunting and rapid incident response, making them well-equipped for effective threat intelligence.
Reference
Product
Fidelis Cybersecurity - 4sync
DETECT. HUNT. RESPOND. —————————– Jedna platforma. Wiele możliwości. Fidelis Network®Analiza ruchu sieciowego na wszystkich portach i protokołach. Klasyfikacja zasobów. DLP. Wykrywanie ataków i skuteczna reakcja. Fidelis Endpoint®EDR – skrócenie czasu wykrycia zagrożenia, dogłębna analiza zdarzenia, automatyzacja odpowiedzi. Fidelis Deception®Inteligentna dezinformacja i dezorientacja atakujących. Automatyczne tworzenie fałszywych środowisk i wabienie atakujących do systemów-pułapek. Fidelis Elevate łączy […]
Looking for more accurate results?
Find the right companies for free by entering your custom query!
25M+ companies
250M+ products
Free to use
Optimatiq
Poland
B
1-10 Employees
2019
Key takeaway
OPTIMATIQ is a consultancy specializing in security solutions, including conducting security audits and penetration testing. With a focus on creating a secure web infrastructure, they offer services like DDoS protection and web application security, ensuring that businesses are well-prepared against potential threats.
Reference
Core business
OPTIMATIQ - OPTIMATIQ Web Security Company
ServicesWeb securityDDoS ProtectionWAFSoftwarePerformance testingCloudSolutionsCloudflareThreatBiteAbout Us ServicesWeb securityDDoS ProtectionWAFSoftwarePerformance testingCloudSolutionsCloudflareThreatBiteAbout UsContact Us Contact with usSend Secure. Efficient. Reliable.Your web infrastructure is our business.We believe having a secure web infrastructure is important. But not more important than your business. Many companies spend precious time and resources on security solutions that slow the company down and don’t scale… Continue reading OPTIMATIQ
Immunity Systems
Warsaw, Poland
B
11-50 Employees
2015
Key takeaway
The company emphasizes its team's extensive experience in both offensive and defensive IT security, which is crucial for effective threat intelligence. Their commitment to security over marketing underscores their focus on safeguarding systems and verifying security levels.
Reference
Core business
Immunity Systems | Strona główna
Cyberus Labs
Katowice, Poland
B
1-10 Employees
-
Key takeaway
Cyberus Labs is a cybersecurity expert that focuses on reducing cyber threats and data breaches through innovative solutions. Their unique audio-token technology prevents 80 percent of hacking attacks, making it highly relevant for those interested in threat intelligence.
Reference
Core business
O firmie - Cyberus LabsCyberus Labs
Dostarczamy rozwiązania w dziedzinie cyberbezpieczeństwa. Nasz cel to eliminowanie źródła cyber zagrożeń, a nie jedynie reakcja na nie. Łączymy technologię zapr
Cryptomage
Wrocław, Poland
B
11-50 Employees
2016
Key takeaway
The company emphasizes its advanced threat intelligence capabilities through comprehensive packet inspection and integration with SIEM systems. Their Cryptomage Cyber Eye™ solution provides in-depth analysis of network traffic and behaviors, going beyond traditional methods to enhance incident analysis and threat detection.
Reference
Core business
Cryptomage – where AI meets cybersecurity
Sagenso
Rzeszów, Poland
B
11-50 Employees
2019
Key takeaway
Sagenso provides real-time threat visibility and expert support to effectively manage various types of threats. Their innovative SaaS system, Telescope, enhances cybersecurity management and includes a proactive approach to protecting against emerging threats like ZERO-day ransomware.
Reference
Core business
Sagenso - Ensure security and business continuity
The IT security of your company is our problem! We relieve your company of the burden of cybersecurity management. Conduct a free IT security audit.
Onesys Sp. z o.o.
Toruń, Poland
B
1-10 Employees
2021
Key takeaway
Onesys specializes in IT security and provides services related to threat intelligence, including a dedicated Security Operation Center (SOC) that continuously monitors infrastructure to detect and respond to security incidents. They also offer expertise in penetration testing and Security Information Event Management (SIEM), enhancing an organization's ability to manage and respond to threats effectively.
Reference
Core business
Onesys: Data Driven Solutions
Vector Synergy
Poland
B
11-50 Employees
-
Key takeaway
Vector Synergy provides expert services in IT security and Cyber Defence, ensuring comprehensive solutions for organizations that require security clearance. Their highly qualified specialists are equipped to support the execution of international projects, enhancing the overall security posture of their clients.
Reference
Core business
Vector Synergy: Consultancy Services, Cyber Defence Services | Vector Synergy dostarcza firmom i organizacjom ekspertów do realizacji projektów, które wymagają posiadania certyfikatu bezpieczeństwa oraz oferuje kompleksowe usługi i więcej niż zaawansowane rozwiązania w zakresie bezpieczeństwa informatycznego Klientów.
Technologies which have been searched by others and may be interesting for you:
A selection of suitable products and services provided by verified companies according to your search.
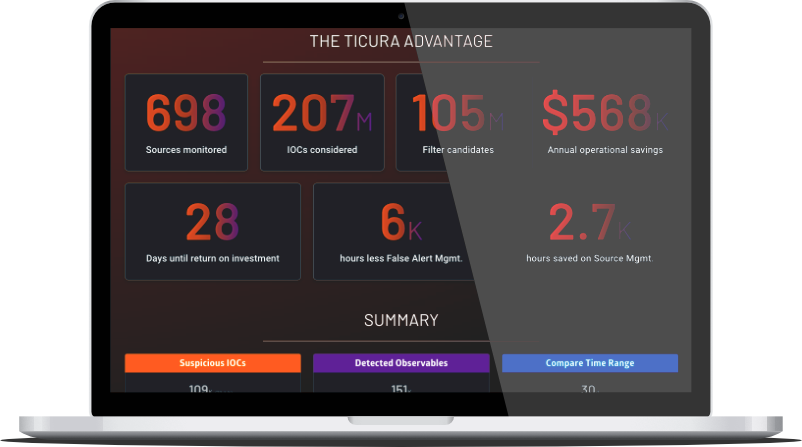
Service
Source Recommendation Assessment
Go to product
A selection of suitable use cases for products or services provided by verified companies according to your search.
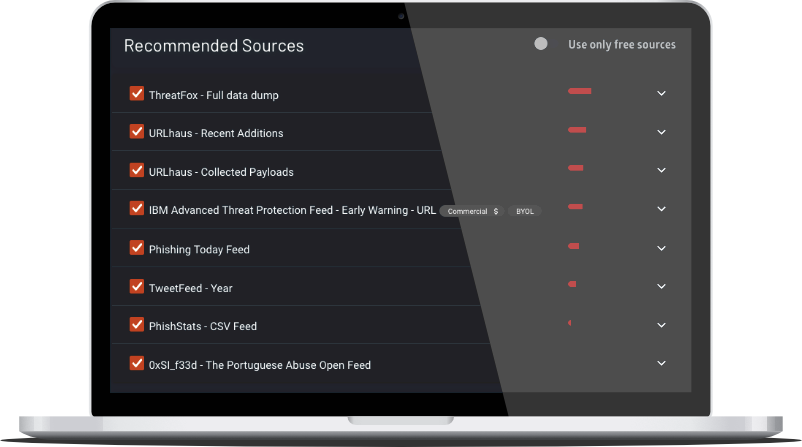
Use case
FInding the optimal Threat Intelligence
MSSP, Security
Ticura enriches existing threat intelligence programs with data from over 870 sources of network, public cloud, SaaS, endpoint and identity telemetry. Then, leveraging its proprietary detection engine, data science and machine learning, Ticura analyzes and surfaces the anomalies, incidents and threats to deliver optimal protection for your organization.

Use case
FInding the optimal Threat Intelligence
MSSP, Security
Ticura enriches existing threat intelligence programs with data from over 870 sources of network, public cloud, SaaS, endpoint and identity telemetry. Then, leveraging its proprietary detection engine, data science and machine learning, Ticura analyzes and surfaces the anomalies, incidents and threats to deliver optimal protection for your organization.
When exploring the Threat Intelligence industry in Poland, several key considerations come into play. The regulatory environment is crucial, as compliance with both European Union directives and local data protection laws, such as the GDPR, is mandatory for companies operating in this space. Understanding these regulations can significantly impact operational strategies. The industry faces challenges, including a shortage of skilled professionals and the constantly evolving nature of cyber threats, necessitating continuous training and adaptation. However, there are ample opportunities for growth, especially as businesses increasingly prioritize cybersecurity measures in response to rising cybercrime incidents. The competitive landscape in Poland is becoming more dynamic, with both local startups and established international firms vying for market share. This competition drives innovation and can lead to collaborative opportunities between companies. Additionally, Poland's strategic location within Europe enhances its relevance in the global market, making it a key player for cybersecurity solutions. Environmental concerns, while less prominent in this sector, are gaining traction as sustainability becomes a priority across industries. Overall, potential entrants to the Threat Intelligence field in Poland should consider these factors to navigate the complexities of the market effectively.
Some interesting numbers and facts about your company results for Threat Intelligence
| Country with most fitting companies | Poland |
| Amount of fitting manufacturers | 39 |
| Amount of suitable service providers | 33 |
| Average amount of employees | 11-50 |
| Oldest suiting company | 2009 |
| Youngest suiting company | 2021 |
Some interesting questions that has been asked about the results you have just received for Threat Intelligence
What are related technologies to Threat Intelligence?
Based on our calculations related technologies to Threat Intelligence are Big Data, E-Health, Retail Tech, Artificial Intelligence & Machine Learning, E-Commerce
Who are Start-Ups in the field of Threat Intelligence?
Start-Ups who are working in Threat Intelligence are Onesys Sp. z o.o.
Which industries are mostly working on Threat Intelligence?
The most represented industries which are working in Threat Intelligence are IT, Software and Services, Consulting, Other, Biotechnology, Cyber Security
How does ensun find these Threat Intelligence Companies?
ensun uses an advanced search and ranking system capable of sifting through millions of companies and hundreds of millions of products and services to identify suitable matches. This is achieved by leveraging cutting-edge technologies, including Artificial Intelligence.