
The B2B platform for the best purchasing descision. Identify and compare relevant B2B manufacturers, suppliers and retailers
Close
Filter
Result configuration
Continents
Select continent
Locations
Result types
Company type
Select company type
Industries
Select industry
Company status
Select company status preset
Number of employees
Min.
Max.
Founding year
S2W
Seongnam-si, South Korea
A
- Employees
2018
Key takeaway
S2W utilizes AI-based detection technology to conduct thorough analyses of virtual asset transactions and monitor illegal activities, making it a key player in threat intelligence. Their platform specifically addresses a range of threats, including those related to cryptocurrency and ransomware, by quickly detecting and analyzing leak information to protect customers from external threats.
Reference
Service
Threat Intelligence
TI quickly detects various leak information by reviewing and analyzing DDW threat data and protects customers from external threats.
Mandiant Korea
Seoul, South Korea
A
11-50 Employees
-
Key takeaway
Mandiant, now part of Google Cloud, specializes in cyber threat intelligence, offering products and services that support their mission to defend against cybercrime. Their Mandiant Breach Analytics for Chronicle combines industry-leading threat intelligence with advanced security operations, enabling early detection of threats and providing insights into critical areas of cyber defense.
Reference
Core business
Cyber Security Threat Intelligence Solutions & Managed Services
Mandiant provides solutions that protect organizations against cyber security attacks, leveraging innovative technology and expertise from the frontlines.
NORMA Inc.
Seoul, South Korea
A
11-50 Employees
2011
Key takeaway
Norma, a global IoT and quantum security specialist, enhances information security through ISMS-P certification, compliance models, and penetration testing, while also fostering a strong security culture within organizations. Their expertise in cloud security certification and innovative solutions positions them as a key player in the threat intelligence landscape.
Reference
Product
글로벌 IoT & 양자 보안 전문 기업 - 노르마
IoT 보안 솔루션과 컨설팅 서비스를 제공하는 양자 보안 전문 기업입니다.
Looking for more accurate results?
Find the right companies for free by entering your custom query!
25M+ companies
250M+ products
Free to use
지니언스(GENIANS)
Anyang-si, South Korea
A
51-100 Employees
2005
Key takeaway
Genians integrates with IBM's Resilient SOAR system to analyze threat intelligence, allowing for the rapid and secure isolation of nodes with identified security threats in the network. This approach aims to protect the network services of clients effectively.
Reference
Product
IBM - Resilient 연동 - Genians
SOAR 시스템인 IBM사의 Resilient에서 분석한 위협정보를 근거로 보안위협이 존재하는 노드를 네트워크에서 격리하여, 고객사의 네트워크 서비스를 신속하고 안전하게 보호하기 위해 연동하는것이 목적입니다.
SNTWORKS Inc.
South Korea
A
1-10 Employees
2016
Key takeaway
SNTWorks specializes in embedded device security and digital forensics, offering services such as security assessments and IP infringement investigations. With a strong background in reverse engineering, the company applies various techniques to address dynamic security challenges.
Reference
Core business
SNTWorks
SNTWorks
Suprema
Seongnam-si, South Korea
A
501-1000 Employees
2000
Key takeaway
Suprema is a prominent global innovator in cybersecurity, specializing in access control and AI-based biometric solutions, highlighting its expertise in security technology.
Reference
Product
Suprema | Security & Biometrics
Suprema is a global leader in biometrics and securities technology.
Lockin Company
Seongnam-si, South Korea
A
11-50 Employees
2013
Key takeaway
LIAPP is a robust mobile app security solution that offers advanced hacking defense and threat detection features. It provides detailed reports on device information and connections, which are essential for effective threat intelligence.
Reference
Core business
LIAPP | The easiest and powerful mobile app security solution
ust one click for source code encryption and obfuscation,Anti-Tamper,Unity protection,rooting detection, string encryption, etc
Insignary
Seoul, South Korea
A
11-50 Employees
2016
Key takeaway
Insignary focuses on enhancing security through its Clarity solution, which identifies security and compliance issues in open source code by using unique fingerprint matching technology. This capability is crucial for threat intelligence, as it allows for the examination of binary code against known vulnerabilities in open source components.
Reference
Core business
insignary
Solution for Identifying Open Source Security and Compliance Issues in Binary Code
Erudite Risk
Seoul, South Korea
A
11-50 Employees
2013
Key takeaway
Erudite Risk offers customized intelligence products that address various areas of the risk ecosystem, emphasizing their commitment to providing relevant and actionable insights. Their trained personnel ensure that the intelligence provided aligns with the specific goals and needs of organizations.
Reference
Service
Security – Erudite Risk
eNsecure
Seoul, South Korea
A
11-50 Employees
2008
Key takeaway
The company emphasizes its commitment to continuous growth in the IT security sector, which is crucial for addressing emerging threats. They have developed a real-time diagnostic system and implemented code security analysis, highlighting their proactive approach to threat intelligence.
Reference
Product
모바일 DNA 보안
Zimperium - 짐페리움
Technologies which have been searched by others and may be interesting for you:
A selection of suitable products and services provided by verified companies according to your search.
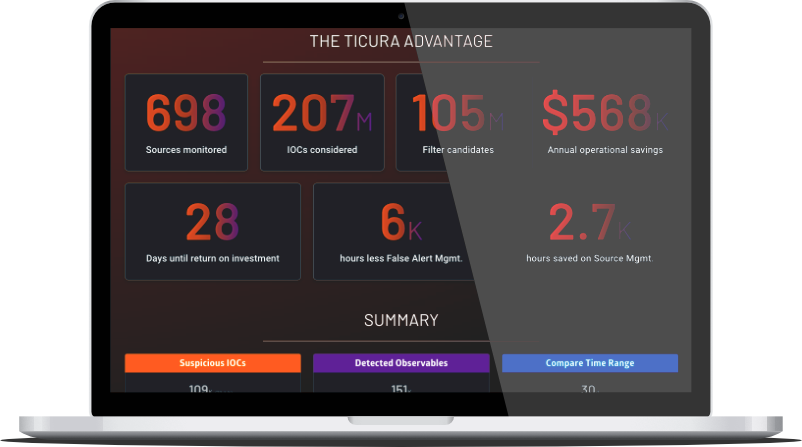
Service
Source Recommendation Assessment
Go to product
A selection of suitable use cases for products or services provided by verified companies according to your search.
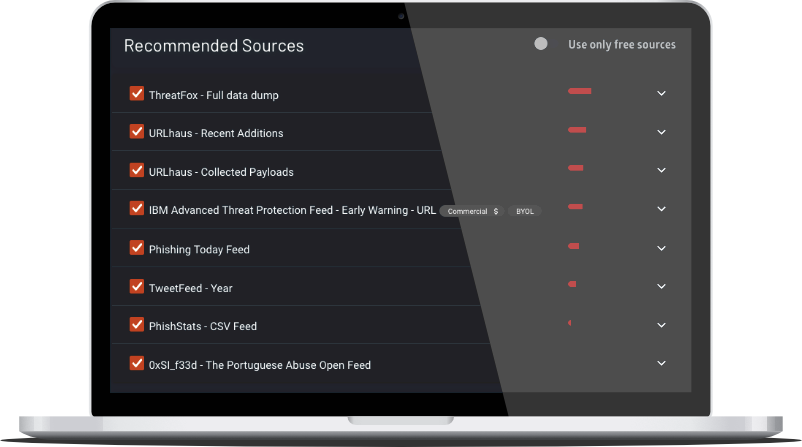
Use case
FInding the optimal Threat Intelligence
MSSP, Security
Ticura enriches existing threat intelligence programs with data from over 870 sources of network, public cloud, SaaS, endpoint and identity telemetry. Then, leveraging its proprietary detection engine, data science and machine learning, Ticura analyzes and surfaces the anomalies, incidents and threats to deliver optimal protection for your organization.

Use case
FInding the optimal Threat Intelligence
MSSP, Security
Ticura enriches existing threat intelligence programs with data from over 870 sources of network, public cloud, SaaS, endpoint and identity telemetry. Then, leveraging its proprietary detection engine, data science and machine learning, Ticura analyzes and surfaces the anomalies, incidents and threats to deliver optimal protection for your organization.
When exploring the Threat Intelligence industry in South Korea, several key considerations emerge. The regulatory landscape is crucial, as the country has stringent data protection laws, including the Personal Information Protection Act (PIPA), which impacts how companies handle sensitive information. Understanding these regulations is vital for compliance and operational success. The competitive landscape is marked by a mix of established firms and emerging startups, creating opportunities for innovation and collaboration. The increasing frequency of cyber threats has heightened demand for threat intelligence solutions, making it a promising sector for investment and growth. Additionally, South Korea's advanced technology infrastructure supports the development of sophisticated threat detection and response systems. Environmental concerns related to data centers and technology use are gaining attention, prompting firms to adopt greener practices. Companies must also consider the global market relevance, as South Korea plays a significant role in the Asia-Pacific region's cybersecurity efforts. Collaborating with international partners can enhance capabilities and expand market reach. Overall, a comprehensive understanding of regulatory requirements, market dynamics, and technological advancements is essential for anyone aiming to enter the Threat Intelligence industry in South Korea.
Some interesting numbers and facts about your company results for Threat Intelligence
| Country with most fitting companies | South Korea |
| Amount of fitting manufacturers | 6 |
| Amount of suitable service providers | 10 |
| Average amount of employees | 11-50 |
| Oldest suiting company | 2000 |
| Youngest suiting company | 2018 |
Some interesting questions that has been asked about the results you have just received for Threat Intelligence
What are related technologies to Threat Intelligence?
Based on our calculations related technologies to Threat Intelligence are Big Data, E-Health, Retail Tech, Artificial Intelligence & Machine Learning, E-Commerce
Which industries are mostly working on Threat Intelligence?
The most represented industries which are working in Threat Intelligence are IT, Software and Services, Defense, Other, Research
How does ensun find these Threat Intelligence Companies?
ensun uses an advanced search and ranking system capable of sifting through millions of companies and hundreds of millions of products and services to identify suitable matches. This is achieved by leveraging cutting-edge technologies, including Artificial Intelligence.