
The B2B platform for the best purchasing descision. Identify and compare relevant B2B manufacturers, suppliers and retailers
Close
Filter
Result configuration
Continents
Select continent
Locations
Result types
Company type
Select company type
Industries
Select industry
Company status
Select company status preset
Number of employees
Min.
Max.
Founding year
Recorded Future
Somerville, United States
B
501-1000 Employees
2009
Key takeaway
Recorded Future is a leading intelligence company that offers comprehensive threat intelligence, enabling organizations to proactively identify and monitor relevant threats. With a vast array of interlinked threat data sets, they provide critical insights into external threats, helping clients stay informed and secure against potential attacks.
Reference
Product
Threat Intelligence | Recorded Future
Recorded Future threat intelligence provides a window into the world of your adversary so you can identify, prioritize, and monitor relevant threats to your organization.
Threat Informant
Anchorage, United States
B
1-10 Employees
-
Key takeaway
Threat Informant specializes in cybersecurity solutions for the Alaskan market, focusing on protecting enterprises from major threats and providing the latest IT security knowledge. With a commitment to advanced security research, they develop products that address the specific needs of their clients.
Reference
Service
Threat Informant -
Threat Intelligence Platform
Irvine, United States
B
1-10 Employees
2017
Key takeaway
The Threat Intelligence Platform offers comprehensive insights by integrating multiple threat intelligence sources, making it a valuable resource for enhancing cybersecurity measures. It provides user-friendly APIs that allow for seamless integration with existing systems, enabling capabilities like domain malware detection and reputation scoring.
Reference
Core business
Threat Intelligence Platform (TIP) | Integrate #1 Cyber Threat Intel APIs
Use TIP APIs to integrate domain malware detection, SSL cert/config analysis, domain reputation scoring, reverse IP and more capabilities.
Looking for more accurate results?
Find the right companies for free by entering your custom query!
25M+ companies
250M+ products
Free to use
Stellar Cyber
United States
B
51-100 Employees
2015
Key takeaway
The company offers a robust Threat Intelligence platform that aggregates multiple commercial, open-source, and government threat intelligence feeds, providing security analysts with enhanced capabilities for automated threat hunting and real-time insights. Their focus on intelligent automation and customization ensures that security teams can effectively leverage this intelligence to gain an advantage over attackers.
Reference
Product
Threat Intelligence Platform, Automated threat hunting
Our threat Intelligence platform aggregates multiple commercial, open-source and government threat intelligence feeds together. Get key features of threat Intelligence platform
Center for Threat Intelligence
Kirkland, United States
B
1-10 Employees
2017
Key takeaway
The Center for Threat Intelligence, led by CEO Janet Lawless, specializes in developing comprehensive threat intelligence programs through customized training, consulting, and certifications for both corporations and government organizations. This focus on tailored education and resources highlights their commitment to enhancing organizational preparedness against cyber threats.
Reference
Core business
About - Center for Threat Intelligence
About - Center for Threat Intelligence
Advise Cyber Solutions
Phoenix, United States
B
1-10 Employees
2018
Key takeaway
The company offers a comprehensive cyber security experience, emphasizing their expertise in threat intelligence through their partnership with top security manufacturers. This ensures businesses have access to advanced security solutions and support, allowing them to focus on their core operations.
Reference
Product
Threat Intelligence – Advise Cyber Solutions LLC
Nehemiah Security
United States
B
101-250 Employees
2015
Key takeaway
ThreatConnect emphasizes the importance of integrating threat intelligence into security operations, offering a platform that enables teams to collect, analyze, and operationalize threat data effectively. Their focus on automation allows organizations to quantify cyber risk, enhancing overall security posture.
Reference
Core business
Cyber Threat Intelligence Company | ThreatConnect
Learn how we enable cyber threat intelligence and security operations teams to act on the highest fidelity intelligence and automate processes. Get a demo.
zvelo, Inc.
Greenwood Village, United States
B
51-100 Employees
1984
Key takeaway
The company enhances in-house threat intelligence capabilities through faster and more effective threat detection, providing curated, high-veracity data on phishing and malicious indicators of compromise (IOCs). This robust threat intelligence supports a comprehensive security suite, empowering teams to accelerate cyber maturity and operational efficiency.
Reference
Product
Powering Threat Research
Intrusion
Richardson, United States
B
11-50 Employees
1983
Key takeaway
Intrusion is dedicated to enhancing your IT team's ability to proactively identify and counteract malicious activities within your network. With a focus on advanced threat intelligence and a robust Global Threat Engine that compiles extensive IP records, Intrusion equips businesses with the insights and technology needed to secure their networks effectively.
Reference
Core business
Threat Intelligence Experts | Intrusion
We are seasoned threat intelligence experts who deliver advanced threat intelligence, malicious traffic identification, and automated threat response.
Advantage Factory
Bellingham, United States
B
1-10 Employees
2001
Key takeaway
Advantage Factory's Threat Management Intelligence System enhances security by actively monitoring various data sources and delivering targeted analytics and reporting, which helps in mitigating potential threat risks to your business and personnel. They offer both out-of-the-box and custom threat risk intelligence software solutions.
Reference
Product
Custom Intelligence Threat Risk Software Solutions
Advantage Factory designs and develops out of box and custom threat risk intelligence solutions
Technologies which have been searched by others and may be interesting for you:
A selection of suitable products and services provided by verified companies according to your search.
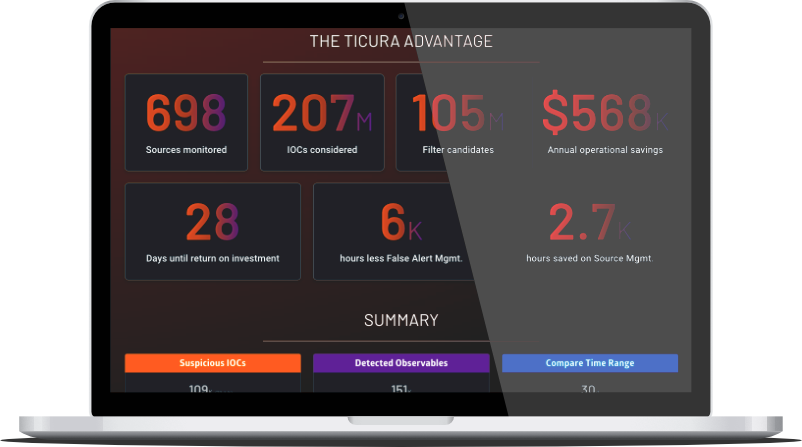
Service
Source Recommendation Assessment
Go to product
A selection of suitable use cases for products or services provided by verified companies according to your search.
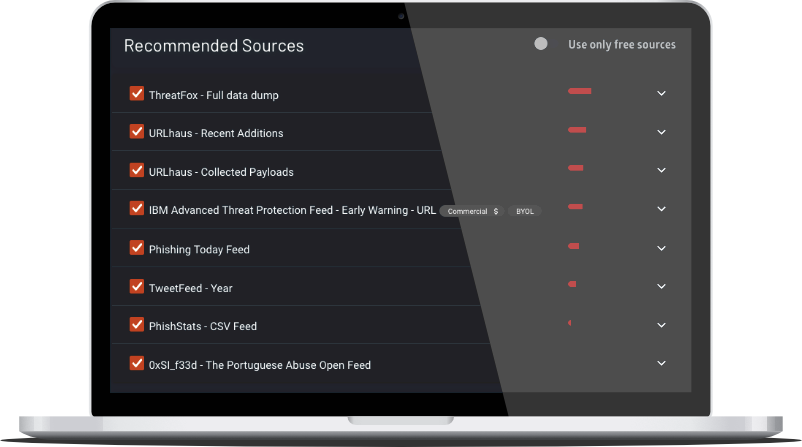
Use case
FInding the optimal Threat Intelligence
MSSP, Security
Ticura enriches existing threat intelligence programs with data from over 870 sources of network, public cloud, SaaS, endpoint and identity telemetry. Then, leveraging its proprietary detection engine, data science and machine learning, Ticura analyzes and surfaces the anomalies, incidents and threats to deliver optimal protection for your organization.

Use case
FInding the optimal Threat Intelligence
MSSP, Security
Ticura enriches existing threat intelligence programs with data from over 870 sources of network, public cloud, SaaS, endpoint and identity telemetry. Then, leveraging its proprietary detection engine, data science and machine learning, Ticura analyzes and surfaces the anomalies, incidents and threats to deliver optimal protection for your organization.
When exploring the Threat Intelligence industry in the United States, several key considerations come into play. First, understanding the regulatory environment is crucial, as compliance with laws such as the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA) can significantly impact operations. The industry faces challenges like the rapid evolution of cyber threats and the need for real-time data analysis, which requires advanced technologies and skilled personnel. Opportunities abound, particularly with the increasing demand for cybersecurity solutions across various sectors, driven by the rise in cyberattacks and data breaches. The competitive landscape is characterized by a mix of established companies and innovative startups, each vying for market share. It's essential to consider the unique offerings and differentiators of these companies, as well as their partnerships and collaborations. Additionally, environmental concerns are gaining traction, with a focus on sustainable practices in technology development. The global relevance of the U.S. Threat Intelligence market cannot be overstated, as it sets trends that influence international standards and practices. Staying informed about these aspects will provide a comprehensive understanding of the industry and help in making informed decisions when researching companies within this dynamic field.
Some interesting numbers and facts about your company results for Threat Intelligence
| Country with most fitting companies | United States |
| Amount of fitting manufacturers | 4228 |
| Amount of suitable service providers | 4380 |
| Average amount of employees | 11-50 |
| Oldest suiting company | 1983 |
| Youngest suiting company | 2018 |
Some interesting questions that has been asked about the results you have just received for Threat Intelligence
What are related technologies to Threat Intelligence?
Based on our calculations related technologies to Threat Intelligence are Big Data, E-Health, Retail Tech, Artificial Intelligence & Machine Learning, E-Commerce
Which industries are mostly working on Threat Intelligence?
The most represented industries which are working in Threat Intelligence are IT, Software and Services, Other, Defense, Consulting, Finance and Insurance
How does ensun find these Threat Intelligence Companies?
ensun uses an advanced search and ranking system capable of sifting through millions of companies and hundreds of millions of products and services to identify suitable matches. This is achieved by leveraging cutting-edge technologies, including Artificial Intelligence.