
The B2B platform for the best purchasing descision. Identify and compare relevant B2B manufacturers, suppliers and retailers
Close
Filter
Result configuration
Continents
Select continent
Locations
Result types
Company type
Select company type
Industries
Select industry
Company status
Select company status preset
Number of employees
Min.
Max.
Founding year
Rootfloe
London, United Kingdom
A
1-10 Employees
2017
Key takeaway
Rootfloe offers comprehensive threat intelligence services as part of its cybersecurity solutions. With a focus on safeguarding organizational infrastructure from attacks, Rootfloe provides detailed analysis and expertise to enhance security measures.
Reference
Service
Threat Intelligence Services - Rootfloe
WorldStack
Biñan, Philippines
D
1-10 Employees
2014
Key takeaway
WorldStack offers comprehensive cyber threat intelligence solutions that provide actionable insights into threats targeting your organization. Their expertise in online research and investigation, combined with a deep understanding of human behavior, equips your security team with critical context to navigate and respond to threats effectively.
Reference
Product
Cyber Threat Intelligence — WorldStack
ticura GmbH
Kassel, Germany
A
1-10 Employees
2022
Key takeaway
Ticura offers a unique, real-time view of global cyber threat intelligence, providing an optimized program that enhances threat detection and protection for subscribers' specific environments.
Reference
Service
Source Recommendation Assessment
- Select threat intelligence sources you like to be compared, optionally upload a set of sample events to take the relevance of your environment into account. - Our analytics compares vendor-independently characteristics like coverage, timeliness, uniqueness based on your selection with our continuously growing repository of 870+ commercial and free threat intelligence Sources. - The report shows the best combination of sources, ordered by efficiency based on timely coverage, with the highest relevance for you.
Looking for more accurate results?
Find the right companies for free by entering your custom query!
25M+ companies
250M+ products
Free to use
CTM360
Manama, Bahrain
D
51-100 Employees
2014
Key takeaway
CTM360® is a leading threat intelligence partner that specializes in identifying vulnerabilities and managing threats across the Surface, Deep, and Dark Web. Their platform is aligned with MITRE ATT&CK and STIX, providing comprehensive insights into adversary behavior and enabling organizations to detect and respond effectively to relevant threats.
Reference
Product
Cyber Threat Intelligence | MITRE ATT&CK | STIX 2.1 | ThreatCover | CTM360
Threat Intelligence Platform aligned to MITRE ATT&CK and STIX with a focus on attack patterns & TTPs. Detect & respond to the most relevant threats with ThreatCover. Learn more.
ADMINUSLABS LLP
India
D
1-10 Employees
2009
Key takeaway
ADMINUSLabs offers DEEPINSIGHT™, a Cyber Threat Intelligence service that provides decision-makers with accurate and actionable insights on malicious code, vulnerabilities, and global threats. Their threat intelligence feed equips security teams with real-time data to effectively address emerging threats, enhancing organizational cyber defense and security awareness.
Reference
Service
Services | ADMINUSLabs
ADMINUSLabs Threat Intelligence services allow you to overcome the pace of malware creation. Find out why cyber-security threats can't hide from us.
NexVision Lab
London, United Kingdom
A
11-50 Employees
2020
Key takeaway
NexVision specializes in providing valuable threat intelligence by leveraging advanced algorithms and the GPT model to analyze data from the Deep and Dark Web. Their services enhance cybersecurity efforts and offer real-time insights, making them a crucial resource for organizations seeking to mitigate risks associated with illegal activities and counterfeiting.
Reference
Service
NexVision Web Threat Intelligence - Services
Intelligence Fusion
United Kingdom
A
11-50 Employees
2014
Key takeaway
The company emphasizes its commitment to advanced threat intelligence by providing fast, accurate, and in-depth data analysis. With a focus on developing intuitive intelligence tools and real-time incident reporting, they ensure clients receive reliable and actionable insights to enhance their security posture.
Reference
Product
Threat Intelligence Platform - Intelligence Fusion
Intelligence Fusion can build your ideal solution to threat intelligence to suit your needs and goals. Find out more.
Vulidity GmbH
Burghausen, Germany
A
1-10 Employees
2018
Key takeaway
The company's Threat Intelligence solutions, recognized with the "Security Made in Germany" seal, are developed by certified experts and receive continuous updates, providing optimal preventive protection against cyber threats for all industries and business sizes. Their tools automate comprehensive risk analyses, enhancing cybersecurity measures effectively.
Reference
Core business
Vulidity - Cyber-Sicherheit durch unsere Threat Intelligence Tools
Unsere Threat Intelligence Tools liefern Ihnen automatisiert ganzheitliche Risikoanalysen zur Cyber-Sicherheit in Ihrem Unternehmen.
Center for Threat Intelligence
Kirkland, United States
B
1-10 Employees
2017
Key takeaway
The Center for Threat Intelligence, led by CEO Janet Lawless, specializes in developing comprehensive threat intelligence programs through customized training, consulting, and certifications for both corporations and government organizations. This focus on tailored education and resources highlights their commitment to enhancing organizational preparedness against cyber threats.
Reference
Core business
About - Center for Threat Intelligence
About - Center for Threat Intelligence
iSOC24 B.V.
Culemborg, Netherlands
A
11-50 Employees
2012
Key takeaway
iSOC24 emphasizes the importance of Cyber Threat Intelligence as a crucial component of a robust cybersecurity strategy. They focus on real-time risk monitoring and provide organizations with advanced security tools through strategic partnerships, making them well-equipped to address threats effectively.
Reference
Product
Threat Intelligence
Technologies which have been searched by others and may be interesting for you:
A selection of suitable products and services provided by verified companies according to your search.
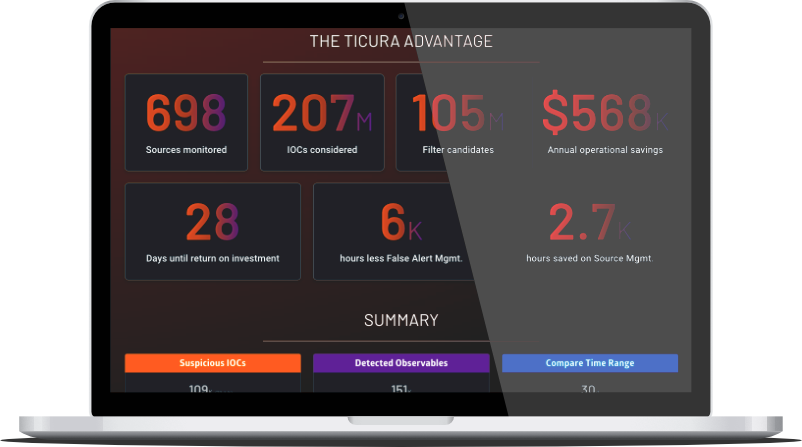
Service
Source Recommendation Assessment
Go to product
A selection of suitable use cases for products or services provided by verified companies according to your search.
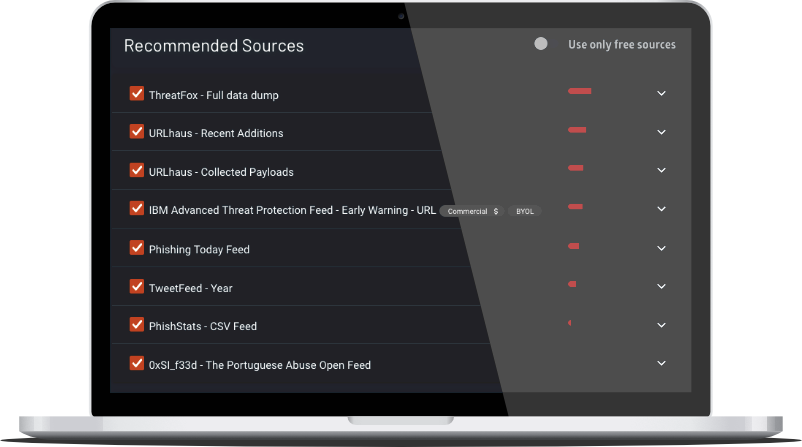
Use case
FInding the optimal Threat Intelligence
MSSP, Security
Ticura enriches existing threat intelligence programs with data from over 870 sources of network, public cloud, SaaS, endpoint and identity telemetry. Then, leveraging its proprietary detection engine, data science and machine learning, Ticura analyzes and surfaces the anomalies, incidents and threats to deliver optimal protection for your organization.

Use case
FInding the optimal Threat Intelligence
MSSP, Security
Ticura enriches existing threat intelligence programs with data from over 870 sources of network, public cloud, SaaS, endpoint and identity telemetry. Then, leveraging its proprietary detection engine, data science and machine learning, Ticura analyzes and surfaces the anomalies, incidents and threats to deliver optimal protection for your organization.
Threat intelligence refers to the collection and analysis of information regarding potential or current threats to an organization's security. This data can include information about cyberattacks, malware, vulnerabilities, and threat actors. By utilizing threat intelligence, organizations can proactively identify and mitigate risks, enhance their security posture, and improve incident response capabilities. Effective threat intelligence integrates data from various sources, including open-source information, industry reports, and proprietary data feeds. This comprehensive approach allows organizations to gain insights into emerging threats, enabling them to make informed decisions about security strategies and investments.
Threat Intelligence enhances cybersecurity by providing organizations with actionable insights into potential threats and vulnerabilities. By analyzing data from various sources such as malware reports, attack patterns, and threat actor behavior, it helps in identifying emerging threats before they can cause harm. Additionally, this information allows security teams to prioritize their defenses, focusing on the most significant risks. Continuous monitoring and real-time alerts enable quicker incident response, reducing the impact of security breaches. Overall, leveraging Threat Intelligence leads to a proactive security posture, empowering organizations to stay one step ahead of cyber adversaries.
1. Enhanced Security Posture
Utilizing threat intelligence allows organizations to proactively identify and mitigate potential threats. By analyzing data about current and emerging threats, companies can strengthen their security measures and reduce vulnerabilities.
2. Improved Incident Response
Threat intelligence aids in accelerating incident response times. With access to real-time data on threats, security teams can quickly assess and address issues, minimizing the impact of security breaches and ensuring a more effective response strategy.
1. Define Clear Objectives
Companies should start by identifying specific goals for their threat intelligence initiatives. This includes understanding the types of threats they face and prioritizing the most relevant intelligence sources.
2. Integrate with Existing Security Systems
Effective implementation involves integrating threat intelligence with current security infrastructure. This ensures that insights can be utilized in real-time, enhancing the organization's ability to respond to threats promptly.
3. Foster Collaboration
Encouraging collaboration between IT, security teams, and other departments can enhance the effectiveness of threat intelligence. Sharing insights and experiences helps to create a comprehensive defense strategy.
4. Regular Training and Awareness
Ongoing training for staff on threat intelligence tools and strategies is essential. By keeping the team informed about the latest threats and mitigation techniques, companies can better safeguard their assets.
5. Evaluate and Adapt
Companies should continuously evaluate the effectiveness of their threat intelligence efforts. Adapting strategies based on evolving threat landscapes ensures that the organization remains resilient against new vulnerabilities.
1. Security Information and Event Management (SIEM)
These tools aggregate and analyze security data from across an organization’s infrastructure, assisting in the identification of potential security threats.
2. Threat Intelligence Platforms (TIP)
These platforms are designed to collect, analyze, and share threat data, providing organizations with actionable intelligence to enhance their security posture.
3. Endpoint Detection and Response (EDR)
EDR solutions monitor endpoints for suspicious activities and provide real-time analysis and response capabilities, essential for detecting and mitigating threats.
4. Vulnerability Management Tools
These tools identify and prioritize vulnerabilities within systems and applications, helping organizations address weaknesses that attackers could exploit.
5. Open Source Intelligence (OSINT) Tools
OSINT tools gather publicly available information from various sources to provide insights into potential threats, enhancing overall situational awareness.
6. Incident Response Tools
These tools are vital for managing and responding to security incidents, allowing organizations to contain and remediate threats effectively.
Some interesting numbers and facts about your company results for Threat Intelligence
| Country with most fitting companies | United States |
| Amount of fitting manufacturers | 31 |
| Amount of suitable service providers | 28 |
| Average amount of employees | 1-10 |
| Oldest suiting company | 2009 |
| Youngest suiting company | 2022 |
20%
40%
60%
80%
Some interesting questions that has been asked about the results you have just received for Threat Intelligence
What are related technologies to Threat Intelligence?
Based on our calculations related technologies to Threat Intelligence are Big Data, E-Health, Retail Tech, Artificial Intelligence & Machine Learning, E-Commerce
Who are Start-Ups in the field of Threat Intelligence?
Start-Ups who are working in Threat Intelligence are ticura GmbH
Which industries are mostly working on Threat Intelligence?
The most represented industries which are working in Threat Intelligence are IT, Software and Services, Other, Defense, Cyber Security
How does ensun find these Threat Intelligence Companies?
ensun uses an advanced search and ranking system capable of sifting through millions of companies and hundreds of millions of products and services to identify suitable matches. This is achieved by leveraging cutting-edge technologies, including Artificial Intelligence.