
The B2B platform for the best purchasing descision. Identify and compare relevant B2B manufacturers, suppliers and retailers
Close
Filter
Result configuration
Continents
Select continent
Locations
Result types
Company type
Select company type
Industries
Select industry
Company status
Select company status preset
Number of employees
Min.
Max.
Founding year
Datacloak
Shenzhen, China
D
11-50 Employees
2018
Key takeaway
DataCloak is a company focused on innovative data security technologies, emphasizing its commitment to preventing unauthorized access and disclosure of sensitive enterprise data. Their integrated data security platform, which utilizes cryptography and AI, aligns with the principles of Zero Trust by ensuring robust protection across various environments.
Reference
Product
DataCloak | Zero Trust|Data Security|DACS|Data Leakage Prevention|Secure Remote Office|Mobile Secure Office|Secure Cloud Desktop|Dynamic Security|Data Security Platform|Secure Workspace
Systex
Hong Kong Island, China
D
1001-5000 Employees
1997
Key takeaway
Systex specializes in integrated application solutions and has established strategic partnerships with leading companies, enhancing its technological capabilities and service offerings. This expertise positions Systex as a key player in providing comprehensive IT solutions, which may align with the principles of a Zero Trust approach.
Reference
Product
Netskope

TELSTRA INTERNATIONAL LIMITED
Hong Kong Island, China
D
51-100 Employees
2000
Key takeaway
The company emphasizes its commitment to safeguarding user data through security automation, which aligns with the principles of a Zero Trust approach. By ensuring secure connections to cloud environments and protecting account details, the company illustrates its focus on maintaining robust security measures.
Reference
Product
Cloud Connectivity | Telstra
Simply & securely connect to all your cloud environments from one place. Access 170+ providers with the first globally connected on-demand networking platform.
Looking for more accurate results?
Find the right companies for free by entering your custom query!
25M+ companies
250M+ products
Free to use
Skygear.io
Kowloon, China
D
51-100 Employees
2008
Key takeaway
Authgear.com emphasizes the importance of trust in data management, particularly through its robust identity and access management solutions. Their platform addresses security challenges by enabling seamless and secure external access to business applications, which is essential for implementing a Zero Trust framework.
Reference
Product
External Identity and Access Management - Authgear
Integrate your business applications with Authgear to centralize management of external and internal identities.
Huge Crown Technology Limited
Hong Kong Island, China
D
11-50 Employees
2013
Key takeaway
HCTL offers comprehensive cybersecurity solutions that encompass data protection, network security, and identity and access management, aligning with the principles of Zero Trust by emphasizing robust security measures throughout the organization's infrastructure. Their professional team provides consultative assistance and advanced security services to enhance your business's overall security posture.
Reference
Service
IT Consulting | Huge Crown Technology
From data protection to network security, from IoT security to Trust management and Identity and Access Management, discover how HCTL cybersecurity hardware and software solutions ensure the ultimate security for your business.
CYPHER
Kowloon, China
D
1-10 Employees
-
Key takeaway
CYPHER is a cyber security consultancy that emphasizes intelligence-based security assessments, which can align with the principles of a "Zero Trust" approach by identifying and addressing defense weaknesses through simulated hacker tests. Their tailored solutions make advanced cyber security more accessible, especially for SMEs looking to enhance their security posture.
Reference
Core business
Cypher | Security Testing, Security Consultant, Ethical Hacking
SDAP
Hong Kong Island, China
D
11-50 Employees
2012
Key takeaway
SDAP is an IT consultation firm specializing in network security assessment and incident response for SMEs. With a focus on evaluating risks related to data leakage and unauthorized access, SDAP provides comprehensive cybersecurity solutions that align with the principles of a "Zero Trust" approach.
Reference
Core business
SDAP – IT SECURITY
Hoplite Technology Ltd
Kowloon, China
D
1-10 Employees
2018
Key takeaway
Hoplite Tech emphasizes the importance of cyber security for everyday users, advocating for personal information anonymity as a universal right. Their mission is to empower individuals to protect their digital assets and online identity.
Reference
Core business
Hoplite Founding Story and Team
Build Trust via Risk Visibility
Network Box Corporation
Kowloon, China
D
101-250 Employees
2000
Key takeaway
Network Box is a leading global Managed Security Service Provider (MSSP) that emphasizes comprehensive and effective cybersecurity solutions. As they transition to a multi-tenanted cloud platform, their focus on next-generation managed security aligns with the principles of a Zero Trust approach, ensuring robust protection against evolving cyber threats.
Reference
Core business
About Us — Network Box Managed Security Services

北京微步在线科技有限公司
Dongcheng District, China
D
11-50 Employees
-
Key takeaway
ThreatBook is a leading provider of threat detection and response, offering comprehensive cybersecurity solutions that align with the principles of Zero Trust by ensuring robust protection across cloud, traffic, and endpoints.
Reference
Product
网络安全解决方案_赋能企业安全运营_微步在线
Technologies which have been searched by others and may be interesting for you:
A selection of suitable products and services provided by verified companies according to your search.
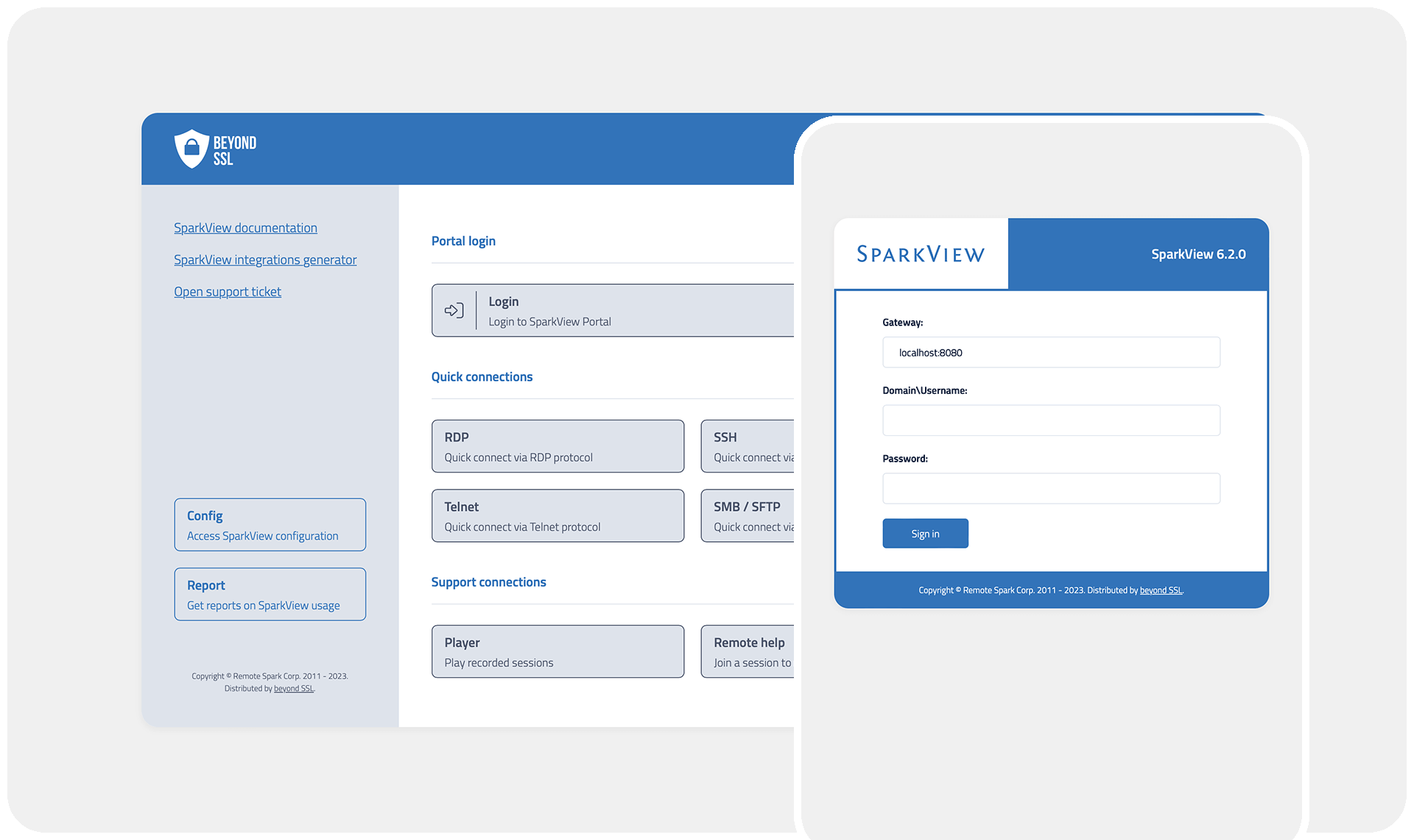
Product
SparkView ZTNA
Go to product
A selection of suitable use cases for products or services provided by verified companies according to your search.

Use case
Access any app on your Chromebook—even if it's not ChromeOS-native
Education, Gov, All Industries
SparkView lets you get even more out of your Chromebooks! SparkView is easy to use via the browser or as an app (PWA) and gives your Chromebook superpowers: you get secure and fast access to internal company apps, desktops, and servers directly in your browser. With SparkView, you can also seamlessly access non-ChromeOS-native apps—whether they’re specially developed applications, legacy systems, Windows apps, macOS apps, and more—ensuring you have the right tools at your fingertips, no matter the platform. And best of all: no data leaves the company!
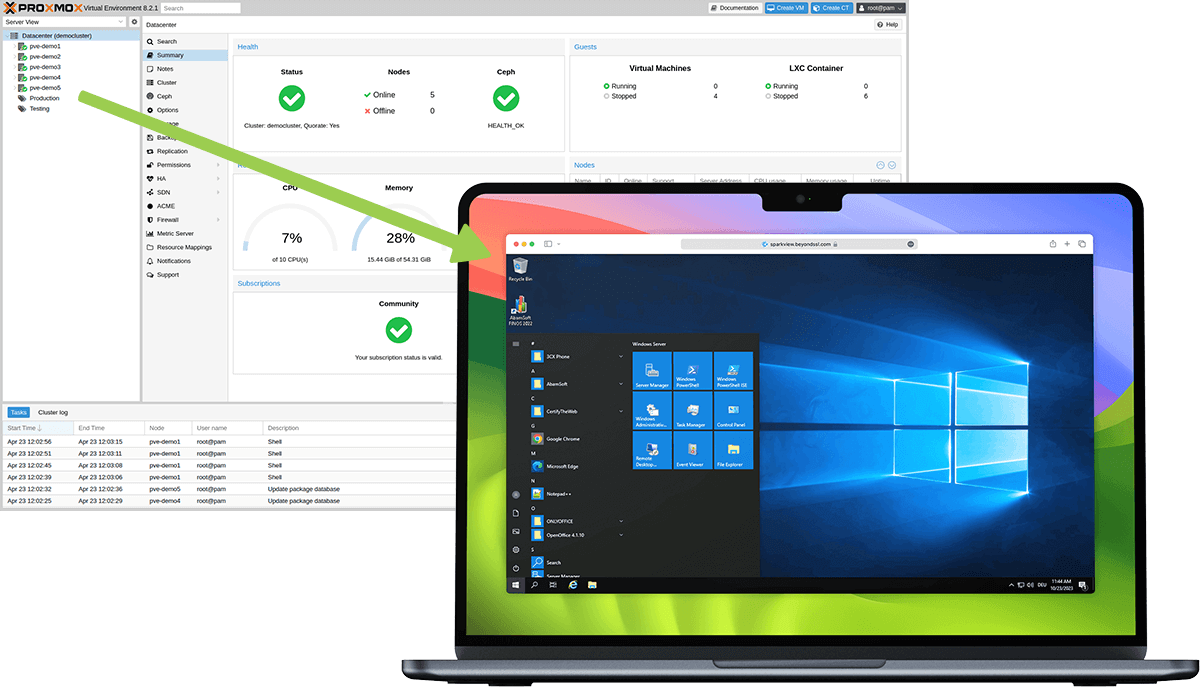
Use case
Secure Remote Access to Your Virtualization Environment with Proxmox
all
The Perfect Combination: SparkView and Proxmox for Secure and Efficient IT Infrastructures. With Zero Trust and virtualization, you can eliminate VPN security risks, reduce administrative complexity, and minimize the cost pressures of traditional solutions. Maximum security through Zero Trust > SparkView grants access to Proxmox resources only after strict authentication. >Each access package is checked individually, which prevents lateral movement. Simple administration >Proxmox offers centralized management for VMs and containers. >SparkView enables administrators to easily control access rights for Proxmox services - without separate client software. Cost efficiency >Proxmox and SparkView offer excellent value. >No need for expensive VPN licenses or additional hardware.
Use case
Clientless ZTNA-compliant Remote Access - without VPN
all
Traditional VPNs are no longer sufficient for securing remote access. SparkView offers a clientless Zero Trust Network Access (ZTNA) solution, enabling secure, browser-based access to internal applications and desktops—without the complexity of VPNs. Users can connect seamlessly from any device while organizations maintain granular access control and zero trust security principles, ensuring that only authorized users gain entry to corporate resources. SparkView enhances security, flexibility, and user experience, making remote work efficient and risk-free.

Use case
Access any app on your Chromebook—even if it's not ChromeOS-native
Education, Gov, All Industries
SparkView lets you get even more out of your Chromebooks! SparkView is easy to use via the browser or as an app (PWA) and gives your Chromebook superpowers: you get secure and fast access to internal company apps, desktops, and servers directly in your browser. With SparkView, you can also seamlessly access non-ChromeOS-native apps—whether they’re specially developed applications, legacy systems, Windows apps, macOS apps, and more—ensuring you have the right tools at your fingertips, no matter the platform. And best of all: no data leaves the company!
When exploring the Zero Trust industry in China, it is crucial to consider the regulatory environment, as the country has stringent cybersecurity laws that impact how companies operate. Understanding the Cybersecurity Law and the Data Security Law is essential, as they dictate compliance requirements for businesses, particularly those handling sensitive data. The competitive landscape is rapidly evolving, with both domestic and international players vying for market share. This competition fosters innovation but also presents challenges, such as the need for continuous adaptation to changing technologies and threats. Opportunities abound in sectors such as finance, healthcare, and government, where Zero Trust architectures can significantly enhance security. However, environmental considerations also play a role, as companies are increasingly looking to implement sustainable practices within their IT operations. Additionally, the global market relevance of Zero Trust solutions continues to grow, as organizations worldwide adopt this security framework to counter cyber threats. Thus, staying informed about international trends and advancements in Zero Trust strategies can provide a competitive edge. Networking with local industry experts and attending relevant conferences can also offer insights into best practices and emerging technologies in this dynamic field.
Some interesting numbers and facts about your company results for Zero Trust
| Country with most fitting companies | China |
| Amount of fitting manufacturers | 22 |
| Amount of suitable service providers | 20 |
| Average amount of employees | 11-50 |
| Oldest suiting company | 1997 |
| Youngest suiting company | 2018 |
Some interesting questions that has been asked about the results you have just received for Zero Trust
What are related technologies to Zero Trust?
Based on our calculations related technologies to Zero Trust are Big Data, E-Health, Retail Tech, Artificial Intelligence & Machine Learning, E-Commerce
Which industries are mostly working on Zero Trust?
The most represented industries which are working in Zero Trust are IT, Software and Services, Other, Telecommunications, Defense, Wholesale
How does ensun find these Zero Trust Companies?
ensun uses an advanced search and ranking system capable of sifting through millions of companies and hundreds of millions of products and services to identify suitable matches. This is achieved by leveraging cutting-edge technologies, including Artificial Intelligence.