
The B2B platform for the best purchasing descision. Identify and compare relevant B2B manufacturers, suppliers and retailers
Close
Filter
Result configuration
Continents
Select continent
Locations
Result types
Company type
Select company type
Industries
Select industry
Company status
Select company status preset
Number of employees
Min.
Max.
Founding year
XplicitTrust GmbH
Karlsruhe, Germany
A
1-10 Employees
2021
Key takeaway
XplicitTrust offers a Zero Trust VPN service that simplifies network access and enhances security, making it as easy as making a video call. Their commitment to innovative network security solutions positions them as key players in addressing cybersecurity threats.
Reference
Core business
XplicitTrust · Zero Trust VPN Service
As easy as making a video call: XplicitTrust simplifies network access, making VPNs and network security less of a hassle.
Palo Alto Networks DACH
Germany
A
- Employees
-
Key takeaway
Zero Trust is a cybersecurity approach that completely abandons implicit trust and continuously checks and verifies every phase of digital interactions. The Prisma Cloud platform is specifically designed to provide the necessary control, security, and scalability for the cloud.
Reference
Service
Services - Palo Alto Networks
BSlash GmbH
Ettlingen, Germany
A
1-10 Employees
-
Key takeaway
BSlash GmbH is a certified Cisco Security Partner focused on implementing next-generation security solutions, highlighting their commitment to innovative IT projects and a collaborative approach to security. Their emphasis on "zero trust" aligns with contemporary security practices.
Reference
Service
Security – BSlash GmbH
Looking for more accurate results?
Find the right companies for free by entering your custom query!
25M+ companies
250M+ products
Free to use
Unosecur
Berlin, Germany
A
1-10 Employees
2021
Key takeaway
Unosecur focuses on developing a comprehensive cloud security solution that addresses identity risks, making it relevant to the concept of Zero Trust. Their platform enables quick remediation of identity and access permissions gaps, essential for maintaining a secure environment.
Reference
Core business
Unosecur
NCP engineering, Inc.
Nuremberg, Germany
A
51-100 Employees
1986
Key takeaway
NCP offers a Zero Trust Security solution that emphasizes the principle of "never trust, always verify," ensuring total network security through advanced VPN products. Their approach distinguishes itself by providing a robust framework for organizations to implement Zero Trust strategies effectively.
Reference
Product
Zero Trust Security from NCP: Never trust, always verify!

NT Systems
Böblingen, Germany
A
11-50 Employees
1996
Key takeaway
The company emphasizes its expertise in establishing a secure Active Directory infrastructure and implementing a Zero Trust model, which includes identity protection and data security measures. Their specialized knowledge in Microsoft networking and back-office solutions enables them to effectively manage complex projects, ensuring a robust security framework.
Reference
Service
Microsoft Azure Cloud - NT Systems
www.enclaive.io
Berlin, Germany
A
11-50 Employees
2022
Key takeaway
enclaive GmbH specializes in protecting sensitive data through Confidential Computing, ensuring Zero Trust security by encrypting data in use and isolating applications from infrastructure providers. This approach allows businesses to securely build and deploy applications in untrusted cloud environments without altering existing processes.
Reference
Product
enclaive vHSM
The enclaive vHSM is a comprehensive cloud-based security solution designed to provide the highest levels of data protection and cryptographic operations without the need for traditional physical hardware. Combining the robust capabilities of Vault and Nitride, vHSM offers an all-in-one platform for secure key management, encryption, and identity protection. It ensures that your secrets, keys, and machine identities are safeguarded through hardware-rooted identities, automated workload authentication, and access control management. Built on HSMs validated at FIPS 140-2 Level 3, vHSM leverages advanced confidential execution environment technology to protect data in use, offering organizations crypto-agility, elasticity, and cloud-ready security. Whether you’re managing sensitive data on-premises or in the cloud, enclaive vHSM meets the strictest security standards, holding certifications such as FIPS 140-2, ISO 27001:2013, PCI-DSS, CIS, and SOC 2.

system.de - System & Project GmbH
Berlin, Germany
A
1-10 Employees
-
Key takeaway
Fortra emphasizes the importance of a Zero Trust security model, which operates on the principle that no user or application is inherently trustworthy. This approach helps organizations enhance their cybersecurity posture by implementing rigorous security measures that proactively address threats.
Reference
Product
Zero Trust: Was es ist, warum es wichtig ist und wie man sich anpassen kann | Fortra
Zero Trust ist ein Rahmen, in dem Organisationen mit einem Sicherheitsdenken arbeiten und technische Lösungen anwenden, so dass kein Benutzer oder keine Anwendung standardmäßig vertrauenswürdig ist.
Protelion GmbH
Berlin, Germany
A
11-50 Employees
-
Key takeaway
Protelion has developed its Security Platform based on Zero Trust principles, emphasizing innovative security solutions that enhance protection and flexibility for digital communications. Their products incorporate strong encryption and are designed to secure access and protect data across the evolving digital landscape.
Reference
Product
Endpoint Security
n3k Informatik GmbH
Heilbronn, Germany
A
51-100 Employees
-
Key takeaway
N3K specializes in DDI & DNS Security, Active Directory & Cloud Management, and Privileged Access Management & Security, employing a Zero Trust approach that includes Zero Passwords and Zero Attack Surface. Their expertise and solutions, such as HYPR Multi-Factor Authentication, support IT organizations throughout the project lifecycle, ensuring comprehensive security for over half of Germany's DAX companies.
Reference
Product
N3K: HYPR Multi Faktor Authentifizierung
Technologies which have been searched by others and may be interesting for you:
A selection of suitable products and services provided by verified companies according to your search.
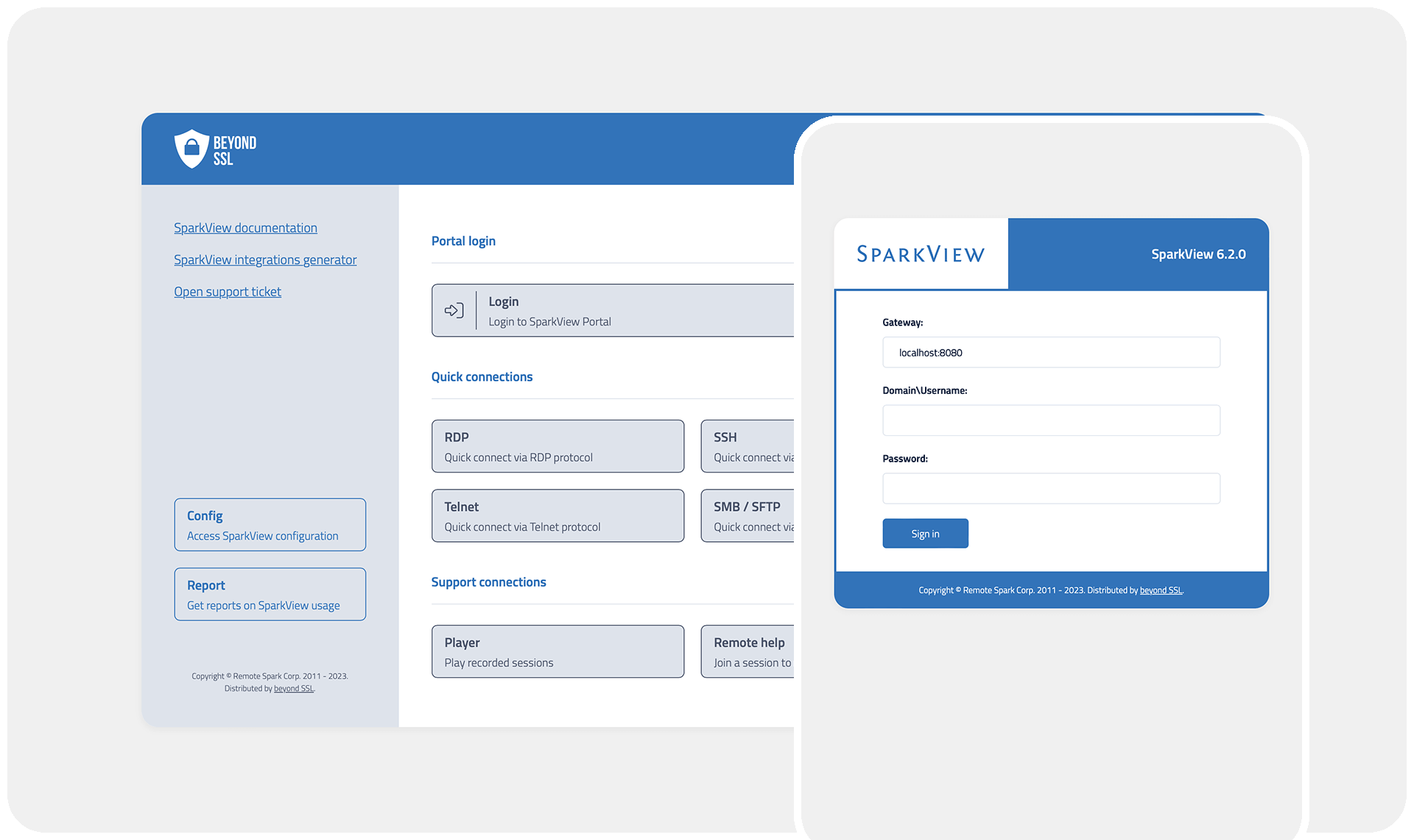
Product
SparkView ZTNA
Go to product
A selection of suitable use cases for products or services provided by verified companies according to your search.

Use case
Access any app on your Chromebook—even if it's not ChromeOS-native
Education, Gov, All Industries
SparkView lets you get even more out of your Chromebooks! SparkView is easy to use via the browser or as an app (PWA) and gives your Chromebook superpowers: you get secure and fast access to internal company apps, desktops, and servers directly in your browser. With SparkView, you can also seamlessly access non-ChromeOS-native apps—whether they’re specially developed applications, legacy systems, Windows apps, macOS apps, and more—ensuring you have the right tools at your fingertips, no matter the platform. And best of all: no data leaves the company!
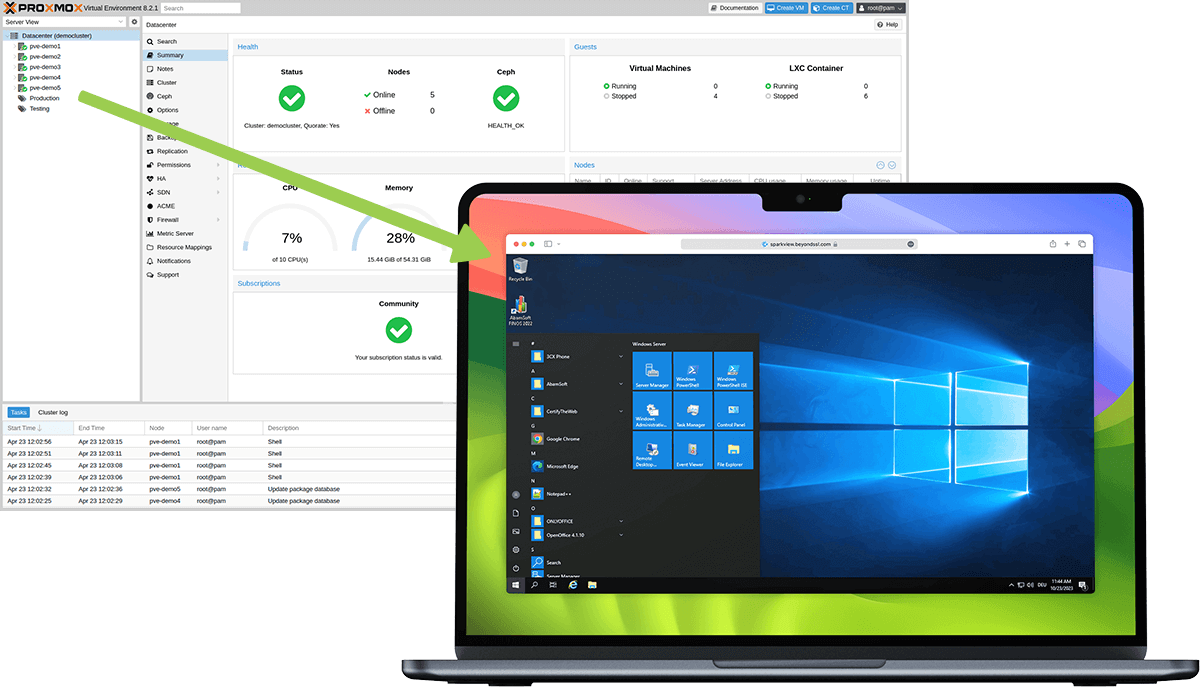
Use case
Secure Remote Access to Your Virtualization Environment with Proxmox
all
The Perfect Combination: SparkView and Proxmox for Secure and Efficient IT Infrastructures. With Zero Trust and virtualization, you can eliminate VPN security risks, reduce administrative complexity, and minimize the cost pressures of traditional solutions. Maximum security through Zero Trust > SparkView grants access to Proxmox resources only after strict authentication. >Each access package is checked individually, which prevents lateral movement. Simple administration >Proxmox offers centralized management for VMs and containers. >SparkView enables administrators to easily control access rights for Proxmox services - without separate client software. Cost efficiency >Proxmox and SparkView offer excellent value. >No need for expensive VPN licenses or additional hardware.
Use case
Clientless ZTNA-compliant Remote Access - without VPN
all
Traditional VPNs are no longer sufficient for securing remote access. SparkView offers a clientless Zero Trust Network Access (ZTNA) solution, enabling secure, browser-based access to internal applications and desktops—without the complexity of VPNs. Users can connect seamlessly from any device while organizations maintain granular access control and zero trust security principles, ensuring that only authorized users gain entry to corporate resources. SparkView enhances security, flexibility, and user experience, making remote work efficient and risk-free.

Use case
Access any app on your Chromebook—even if it's not ChromeOS-native
Education, Gov, All Industries
SparkView lets you get even more out of your Chromebooks! SparkView is easy to use via the browser or as an app (PWA) and gives your Chromebook superpowers: you get secure and fast access to internal company apps, desktops, and servers directly in your browser. With SparkView, you can also seamlessly access non-ChromeOS-native apps—whether they’re specially developed applications, legacy systems, Windows apps, macOS apps, and more—ensuring you have the right tools at your fingertips, no matter the platform. And best of all: no data leaves the company!
When exploring the Zero Trust industry in Germany, several key factors should be taken into account. The regulatory landscape is crucial, as Germany is known for its stringent data protection laws, including the General Data Protection Regulation (GDPR), which impacts how companies manage identity and access controls. Organizations must ensure compliance with these regulations to avoid hefty fines and maintain customer trust. There are challenges related to the implementation of Zero Trust models, particularly in legacy systems integration and the need for extensive employee training. However, opportunities abound as organizations increasingly recognize the importance of securing their networks against sophisticated cyber threats. The competitive landscape includes both established players and emerging startups, each offering innovative solutions tailored to local market needs. Germany's positioning within the European Union enhances its relevance in the global Zero Trust market, as many companies seek to align with EU-wide security standards. Additionally, environmental concerns are rising, prompting companies to consider sustainable practices in their technology deployment. As cyber threats evolve, the Zero Trust framework is becoming increasingly vital for organizations aiming to protect sensitive data and maintain operational integrity in a rapidly changing digital environment.
Some interesting numbers and facts about your company results for Zero Trust
| Country with most fitting companies | Germany |
| Amount of fitting manufacturers | 252 |
| Amount of suitable service providers | 251 |
| Average amount of employees | 11-50 |
| Oldest suiting company | 1986 |
| Youngest suiting company | 2022 |
Some interesting questions that has been asked about the results you have just received for Zero Trust
What are related technologies to Zero Trust?
Based on our calculations related technologies to Zero Trust are Big Data, E-Health, Retail Tech, Artificial Intelligence & Machine Learning, E-Commerce
Who are Start-Ups in the field of Zero Trust?
Start-Ups who are working in Zero Trust are XplicitTrust GmbH, Unosecur, www.enclaive.io
Which industries are mostly working on Zero Trust?
The most represented industries which are working in Zero Trust are IT, Software and Services, Other, Telecommunications, Consulting, Defense
How does ensun find these Zero Trust Companies?
ensun uses an advanced search and ranking system capable of sifting through millions of companies and hundreds of millions of products and services to identify suitable matches. This is achieved by leveraging cutting-edge technologies, including Artificial Intelligence.