
The B2B platform for the best purchasing descision. Identify and compare relevant B2B manufacturers, suppliers and retailers
Close
Filter
Result configuration
Continents
Select continent
Locations
Result types
Company type
Select company type
Industries
Select industry
Company status
Select company status preset
Number of employees
Min.
Max.
Founding year
Trusted Twin
Poland
B
1-10 Employees
2021
Key takeaway
Trusted Twin offers a secure, privacy-centric environment for data collaboration, enabling Data Providers to share customer data with control and compliance. Their platform facilitates real-time data access and collaboration while ensuring privacy and data integrity, making it a valuable resource for businesses looking to enhance their operations through trusted data sharing.
Reference
Core business
Trusted Twin - Trusted Twin
Developer platform for secure data sharing with multiple partners powered by Digital Twins.
Secfense
Krakow, Poland
B
1-10 Employees
2018
Key takeaway
Secfense offers a robust solution for implementing passwordless authentication and multi-factor authentication (MFA), enhancing user access security in line with Zero Trust principles. Their deployment as a reverse proxy ensures that security measures are effectively integrated between users and applications, addressing modern security challenges.
Reference
Core business
Fast Track to Passwordless Authentication | Secfense
Secfense is the fast track to passwordless authentication. We help companies implement strong MFA in a no-code way and at large scale.
Guardanet
Łódź, Poland
B
1-10 Employees
2017
Key takeaway
Guardanet specializes in defining secure architectures for both cloud-based and on-premise workloads, aligning with security best practices to support business objectives. With expertise in areas like AWS Cloud Security and IAM, they are well-equipped to implement a Zero Trust approach.
Reference
Core business
Guardanet | Security Architecture | Public Cloud Security | Kubernetes Security
Looking for more accurate results?
Find the right companies for free by entering your custom query!
25M+ companies
250M+ products
Free to use
APN Promise
Warsaw, Poland
B
101-250 Employees
1991
Key takeaway
The company is a major provider of Microsoft solutions and a certified distributor of top technology suppliers, indicating its strong expertise in digital development and technology consulting. This background may support a robust understanding of Zero Trust principles within their offerings.
Reference
Core business
CloudTeam – APN Promise S.A.
ID Karma
Poland
B
1-10 Employees
2020
Key takeaway
The company emphasizes ultimate privacy and security for users through decentralized user profiles and verifiable credentials, aligning with the principles of a Zero Trust approach. Their OwlMeans Credentials Interaction Server facilitates secure, encrypted communication and peer-to-peer interactions, ensuring data privacy and adherence to standards like DIDComm.
Reference
Product
OwlMeans Credentials Interaction Server
The OwlMeans Credentials Interaction Server enables secure encrypted communication between users and services. It supports peer-to-peer interaction using Verifiable Credentials and Decentralized Identities. Messages and data are encrypted client-side and transferred securely via the server, adhering to the DIDComm standard. OwlMeans Credentials enables the transmission of Verifiable Credentials with binary data between end consumers, ensuring data privacy.
Cyberus Labs
Katowice, Poland
B
1-10 Employees
-
Key takeaway
Cyberus Labs offers a tokenized cybersecurity solution designed to proactively eliminate cyber threats rather than just react to them. Their innovative approach, which includes unique audio-token technology, significantly reduces hacking attacks, making it relevant for organizations looking to adopt a Zero Trust security model.
Reference
Core business
O firmie - Cyberus LabsCyberus Labs
Dostarczamy rozwiązania w dziedzinie cyberbezpieczeństwa. Nasz cel to eliminowanie źródła cyber zagrożeń, a nie jedynie reakcja na nie. Łączymy technologię zapr
Cloud Services ☁️
Sopot, Poland
B
51-100 Employees
2009
Key takeaway
The company, Cloud Services, emphasizes its expertise in implementing and maintaining IT systems, which could align with a Zero Trust approach by highlighting their focus on secure and efficient cloud transformation and data management. Their experience in supporting banking products suggests a strong understanding of security requirements in digital transactions.
Reference
Product
Cloud transformation | Cloud Services
ESYSCO
Środa Wielkopolska, Poland
B
11-50 Employees
2013
Key takeaway
ESYSCO provides innovative cryptographic solutions focused on high-quality technology and security. Their expertise in areas such as Identity and Access Management and PKI directly supports the principles of Zero Trust by protecting sensitive data and ensuring secure access.
Reference
Product
Nexus CM - ESYSCO
Flexible multitenant public key infrastructure (PKI) platform from Nexus Group. Complete and smooth implementation and service.
CQURE Academy
Warsaw, Poland
B
11-50 Employees
2008
Key takeaway
The company emphasizes its commitment to cybersecurity through services like IT security audits and penetration tests, highlighting the shortage of skilled professionals in the field. With a focus on training and implementing advanced security measures, they offer specialized programs that align with the principles of Zero Trust, particularly through the expertise of their certified trainers and the implementation of Privileged Access Workstations.
Reference
Core business
Home | CQURE Academy
Trainings, workshops & certification programs for Windows security professionals who aspire to become experts in their field.
SafeWave.ai
Warsaw, Poland
B
11-50 Employees
1998
Key takeaway
Silverfort emphasizes the importance of safeguarding access and authentication, particularly through Active Directory, which aligns with the principles of a Zero Trust approach. Their focus on protecting identities and preventing data breaches highlights their commitment to enhancing cybersecurity in modern enterprises.
Reference
Core business
HOME - SafeWave
AI-ntelligent cybersecurity Prevent breaches in AI/ML Models, Data Fabric, Identity Fabric, Applications & APIs. Assess your risk Protect Microsofthybrid identity. Continue reading Prevent data breaches. Also in the cloud. Continue reading Stop AI-targeted attacks. Inline with MLSec. Continue reading Microsoft hybrid identity protection and MFA. Read more Proactive data access protection. Also in the cloud. […]
Technologies which have been searched by others and may be interesting for you:
A selection of suitable products and services provided by verified companies according to your search.
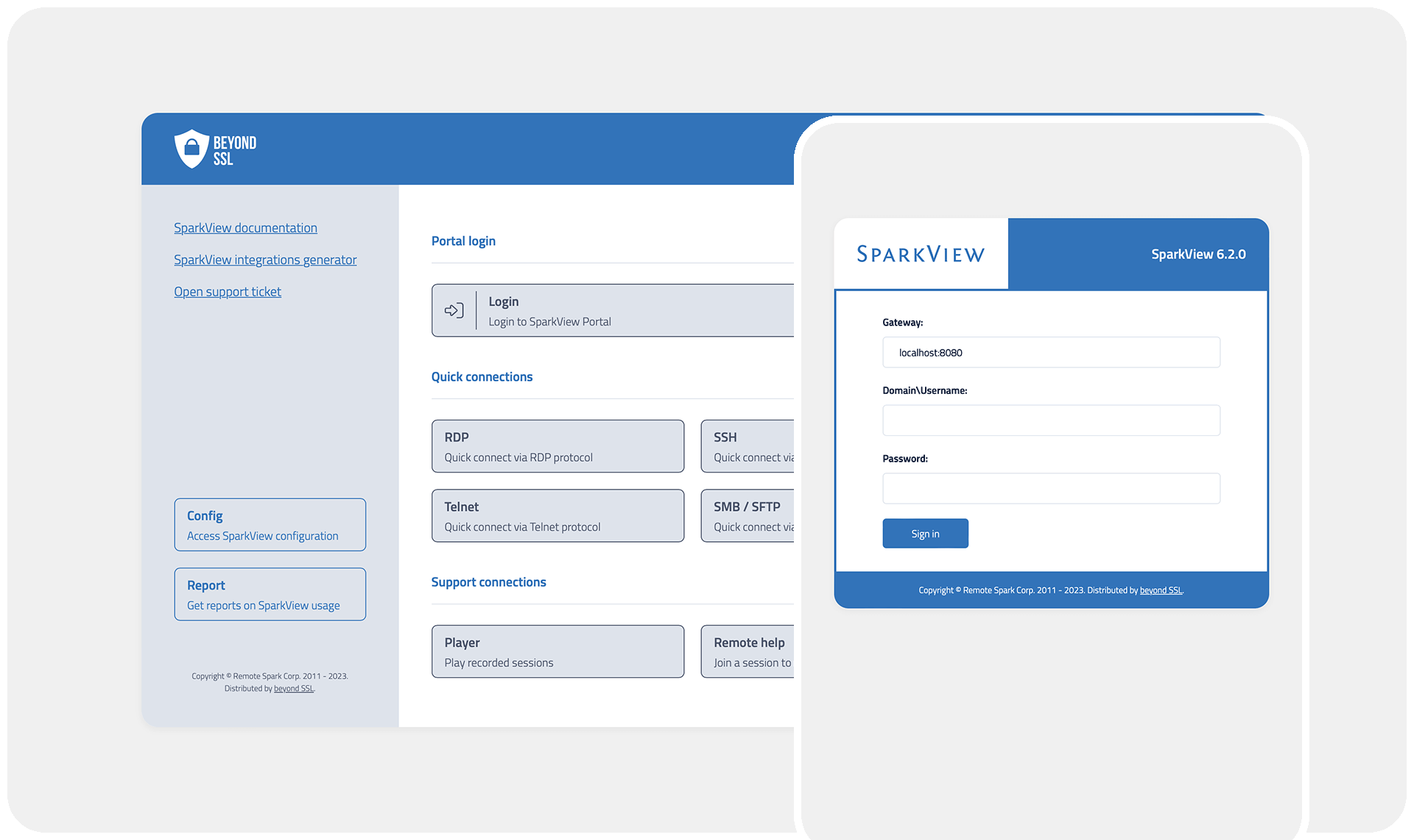
Product
SparkView ZTNA
Go to product
A selection of suitable use cases for products or services provided by verified companies according to your search.

Use case
Access any app on your Chromebook—even if it's not ChromeOS-native
Education, Gov, All Industries
SparkView lets you get even more out of your Chromebooks! SparkView is easy to use via the browser or as an app (PWA) and gives your Chromebook superpowers: you get secure and fast access to internal company apps, desktops, and servers directly in your browser. With SparkView, you can also seamlessly access non-ChromeOS-native apps—whether they’re specially developed applications, legacy systems, Windows apps, macOS apps, and more—ensuring you have the right tools at your fingertips, no matter the platform. And best of all: no data leaves the company!
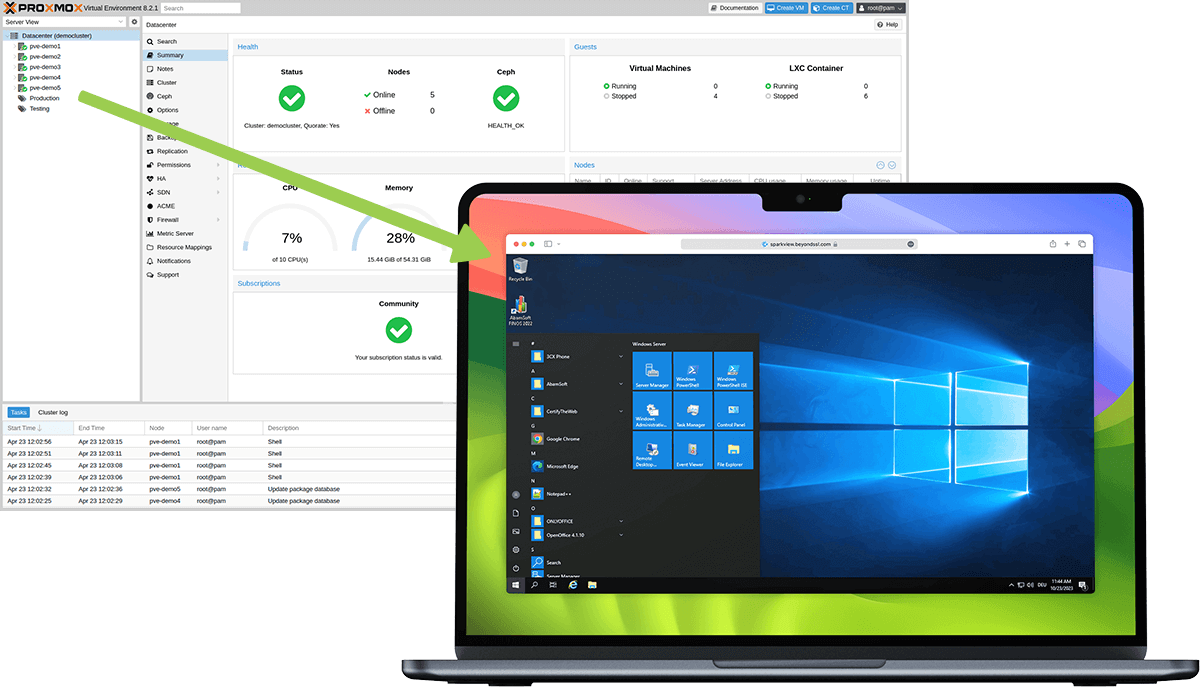
Use case
Secure Remote Access to Your Virtualization Environment with Proxmox
all
The Perfect Combination: SparkView and Proxmox for Secure and Efficient IT Infrastructures. With Zero Trust and virtualization, you can eliminate VPN security risks, reduce administrative complexity, and minimize the cost pressures of traditional solutions. Maximum security through Zero Trust > SparkView grants access to Proxmox resources only after strict authentication. >Each access package is checked individually, which prevents lateral movement. Simple administration >Proxmox offers centralized management for VMs and containers. >SparkView enables administrators to easily control access rights for Proxmox services - without separate client software. Cost efficiency >Proxmox and SparkView offer excellent value. >No need for expensive VPN licenses or additional hardware.
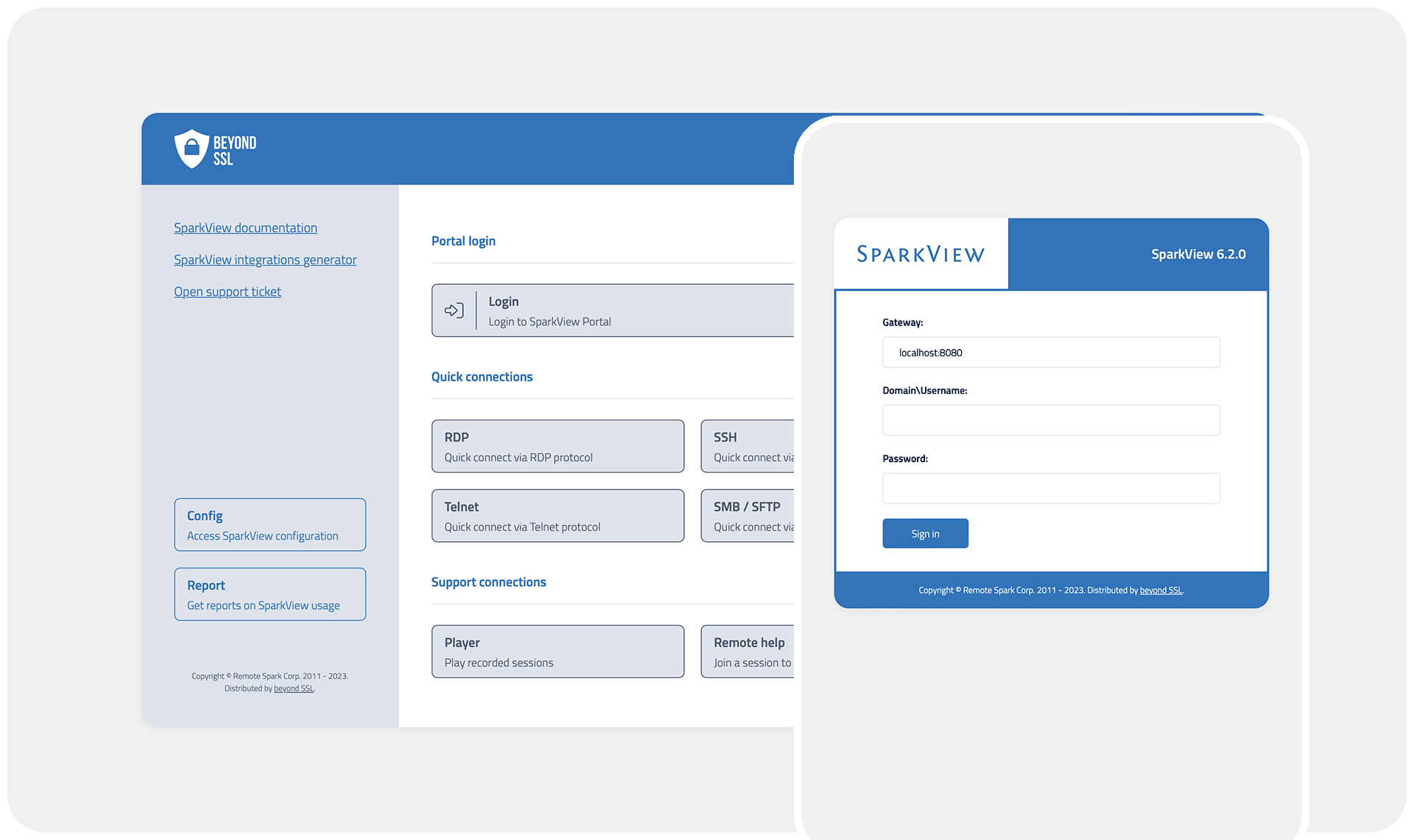
Use case
Clientless ZTNA-compliant Remote Access - without VPN
all
Traditional VPNs are no longer sufficient for securing remote access. SparkView offers a clientless Zero Trust Network Access (ZTNA) solution, enabling secure, browser-based access to internal applications and desktops—without the complexity of VPNs. Users can connect seamlessly from any device while organizations maintain granular access control and zero trust security principles, ensuring that only authorized users gain entry to corporate resources. SparkView enhances security, flexibility, and user experience, making remote work efficient and risk-free.

Use case
Access any app on your Chromebook—even if it's not ChromeOS-native
Education, Gov, All Industries
SparkView lets you get even more out of your Chromebooks! SparkView is easy to use via the browser or as an app (PWA) and gives your Chromebook superpowers: you get secure and fast access to internal company apps, desktops, and servers directly in your browser. With SparkView, you can also seamlessly access non-ChromeOS-native apps—whether they’re specially developed applications, legacy systems, Windows apps, macOS apps, and more—ensuring you have the right tools at your fingertips, no matter the platform. And best of all: no data leaves the company!
When exploring the Zero Trust industry in Poland, several key considerations should be taken into account. Firstly, the regulatory landscape is crucial, particularly with the implementation of the EU's General Data Protection Regulation (GDPR) and the NIS Directive, which emphasizes cybersecurity measures and incident reporting. Understanding these regulations helps in assessing compliance levels among potential partners or vendors. Challenges in this sector include the need for robust infrastructure and skilled professionals, as the demand for Zero Trust solutions grows amidst increasing cyber threats. However, this also presents opportunities for innovation and the development of new technologies tailored to local businesses' specific needs. The competitive landscape is evolving, with both domestic and international players vying for market share. Companies must differentiate themselves through unique offerings and integration capabilities. Additionally, Poland's strategic position within Europe enhances its relevance in the global market, making it an attractive location for investments in cybersecurity solutions. Environmental concerns related to data centers and energy consumption are also emerging as important topics. As more organizations adopt Zero Trust architectures, ensuring that these implementations are sustainable will be a significant factor in long-term viability. Overall, a comprehensive understanding of these factors will provide valuable insights for anyone interested in the Zero Trust industry in Poland.
Some interesting numbers and facts about your company results for Zero Trust
| Country with most fitting companies | Poland |
| Amount of fitting manufacturers | 33 |
| Amount of suitable service providers | 29 |
| Average amount of employees | 11-50 |
| Oldest suiting company | 1991 |
| Youngest suiting company | 2021 |
Some interesting questions that has been asked about the results you have just received for Zero Trust
What are related technologies to Zero Trust?
Based on our calculations related technologies to Zero Trust are Big Data, E-Health, Retail Tech, Artificial Intelligence & Machine Learning, E-Commerce
Who are Start-Ups in the field of Zero Trust?
Start-Ups who are working in Zero Trust are Trusted Twin
Which industries are mostly working on Zero Trust?
The most represented industries which are working in Zero Trust are IT, Software and Services, Consulting, Education, Marketing Services, Cyber Security
How does ensun find these Zero Trust Companies?
ensun uses an advanced search and ranking system capable of sifting through millions of companies and hundreds of millions of products and services to identify suitable matches. This is achieved by leveraging cutting-edge technologies, including Artificial Intelligence.