
The B2B platform for the best purchasing descision. Identify and compare relevant B2B manufacturers, suppliers and retailers
Close
Filter
Result configuration
Continents
Select continent
Locations
Result types
Company type
Select company type
Industries
Select industry
Company status
Select company status preset
Number of employees
Min.
Max.
Founding year
Portnox
Raanana, Israel
B
11-50 Employees
2007
Key takeaway
Portnox offers a comprehensive zero trust solution that integrates passwordless authentication, authorization, risk monitoring, and compliance enforcement, ensuring secure access to networks and infrastructure. Their Portnox Cloud delivers advanced zero trust security capabilities, making it suitable for organizations of all sizes.
Reference
Product
Zero Trust Network Access (ZTNA) - Portnox
Protect your corporate network layers from cyber threats of all kinds with powerful cloud-native ZTNA from Portnox.
Safe-T
Herzliya, Israel
B
11-50 Employees
2013
Key takeaway
TerraZone is pioneering a Zero Trust security approach that enhances protection for the hybrid workforce by ensuring that users have access only to the resources they need, based on identity and context. Their truePass platform offers secure access management and micro-segmentation, addressing the growing need for robust security in today's distributed work environments.
Reference
Service
truePass Zero Trust | TerraZone
truePass Zero Network means that each user only has access to the resources they need and that this access depends on identity and context. Within our truePass dashboard, you can quickly segment your users into groups and create policies that define which of your connected resources (Hybrid, on-prem servers or apps, public cloud apps etc.) are accessible to specific groups.
Infinipoint
Tel-Aviv, Israel
B
- Employees
2019
Key takeaway
Infinipoint is a key player in enabling Zero Trust security through its Device-Identity-as-a-Service (DIaaS) solution, which ensures that only verified users and devices with updated security postures gain access. This approach significantly reduces vulnerabilities and enhances device security, aligning with the core principles of Zero Trust.
Reference
Core business
Enable True Zero Trust Security for Device Access | Infinipoint
Infinipoint is the pioneer and creator of Device-Identity-as-a-Service (DIaaS), a comprehensive device identity and security posture solution that is a critical part of a Zero Trust approach to secure device access.
Looking for more accurate results?
Find the right companies for free by entering your custom query!
25M+ companies
250M+ products
Free to use
Cyolo
Tel-Aviv, Israel
B
1-10 Employees
2019
Key takeaway
Cyolo offers a robust zero trust solution that ensures secure asset access for on-premises, remote, and third-party users, addressing vulnerabilities in traditional network access methods. With a focus on integrating seamlessly with existing technologies, Cyolo empowers security leaders to manage access effectively while enhancing overall cybersecurity.
Reference
Core business
Cyolo | Zero Trust Built for the Real World | Cyolo
Created by CISOs for CISOs, Cyolo enables zero trust for the real world, extending modern controls to your most challenging users, systems, and apps.
Zero Networks
Tel-Aviv, Israel
B
11-50 Employees
2019
Key takeaway
Zero Networks offers a fully automated platform that simplifies network security through MFA-based microsegmentation, enabling least privilege networking for users and machines both on-premises and in the cloud. This approach aligns with the principles of Zero Trust by enhancing security through segmentation and automated access control.
Reference
Product
Product | Zero Networks | MFA-based Microsegmentation
Achieve least privilege networking automatically and in a scalable way for every user and machine – on prem and in the cloud – without agents. How? Automate.
SecuPi
Ramat Gan, Israel
B
11-50 Employees
2014
Key takeaway
SecuPi emphasizes a Zero Trust cybersecurity architecture that focuses on data centricity and conditional access, ensuring that access to data and resources is granted only on a need-to-know basis. This approach aligns with their commitment to data-centric security and compliance, particularly in the context of GDPR.
Reference
Product
Zero Trust 2.0 - SecuPi
Zero trust cybersecurity architecture introduces new security concepts such as data centricity and conditional access to achieve the core concept of never trusting a request for data, applications, or resources. The US Department of Defense (DoD), recently released an update to its Zero Trust (ZT) Reference Architecture. The updated approach to cybersecurity has been updated […]
ReSec Technologies
Hof HaCarmel Regional Council, Israel
B
11-50 Employees
2012
Key takeaway
Resec's Zero Trust platform effectively eliminates all file-based malware threats, both known and unknown, by blocking malicious files and creating threat-free replicas. This approach ensures top-notch security without sacrificing usability, allowing organizations to maintain productivity while preventing potential cyber threats.
Reference
Core business
Zero-Trust Gateway Security | Resec
Resec's Zero Trust platform eliminates all known and unknown (“Zero Day”) file-based malware threats at the organization's gateway.
Cato Networks
Tel-Aviv, Israel
B
251-500 Employees
2015
Key takeaway
Cato Networks has been recognized as a leader in Zero Trust Edge Solutions, highlighting its innovative cloud-native architecture that integrates security and networking. Their Cato Client offers risk-based zero trust network access, ensuring comprehensive protection for all traffic across various environments.
Reference
Product
Cloud Access Security Broker (CASB) | Cato Networks
Catos Cloud Access Security Broker (CASB) provides in depth visibility into SaaS usage and enables IT leaders to better cope with shadow IT.
Secret Double Octopus
Tel-Aviv, Israel
B
11-50 Employees
2015
Key takeaway
Secret Double Octopus emphasizes its commitment to enhancing security through a passwordless multi-factor authentication (MFA) approach. This aligns with the principles of Zero Trust by eliminating passwords, thereby reducing vulnerabilities and creating a more secure environment for organizations.
Reference
Product
Passwordless MFA - Secret Double Octopus
Industry-leading passwordless MFA solutions for workforce authentication with flexible options for embarking on the passwordless journey. Click here for more!
Authomize
Tel-Aviv, Israel
B
11-50 Employees
2020
Key takeaway
Authomize's Cloud Infrastructure Entitlements Management (CIEM) solution emphasizes the importance of achieving Least Privilege and enhancing security posture through advanced analytics, which aligns with the principles of Zero Trust. Their focus on controlling privilege sprawl and managing access risks in multi-cloud environments reinforces a secure access strategy.
Reference
Product
Cloud Infrastructure Entitlements Management (CIEM) | Authomize.com
Authomize's CIEM solution provides unprecedented visibility and control over access risks in multi-cloud environments. Achieve Least Privilege and harden your security posture with advanced analytics. Request a demo today.
Technologies which have been searched by others and may be interesting for you:
A selection of suitable products and services provided by verified companies according to your search.
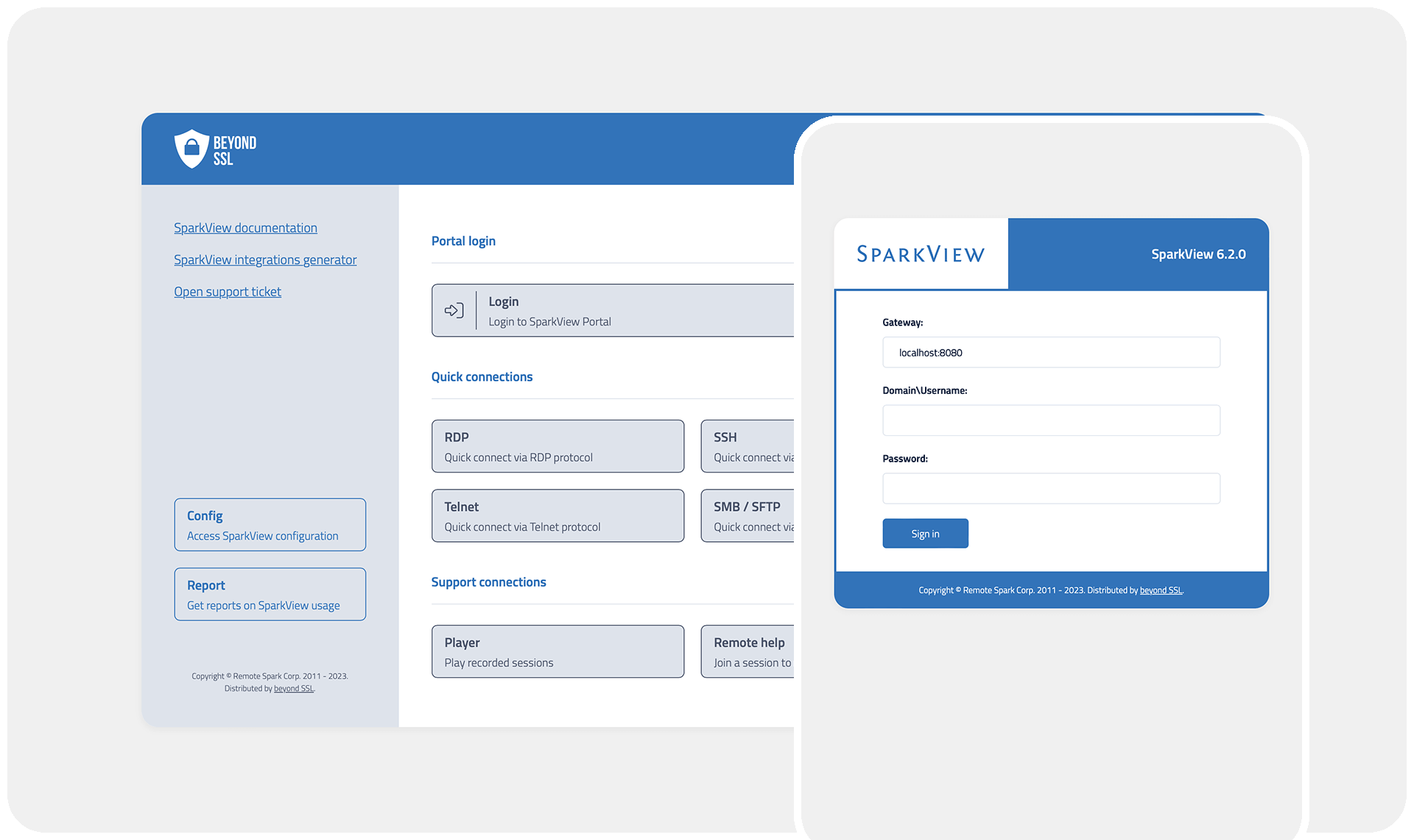
Product
SparkView ZTNA
Go to product
A selection of suitable use cases for products or services provided by verified companies according to your search.

Use case
Access any app on your Chromebook—even if it's not ChromeOS-native
Education, Gov, All Industries
SparkView lets you get even more out of your Chromebooks! SparkView is easy to use via the browser or as an app (PWA) and gives your Chromebook superpowers: you get secure and fast access to internal company apps, desktops, and servers directly in your browser. With SparkView, you can also seamlessly access non-ChromeOS-native apps—whether they’re specially developed applications, legacy systems, Windows apps, macOS apps, and more—ensuring you have the right tools at your fingertips, no matter the platform. And best of all: no data leaves the company!
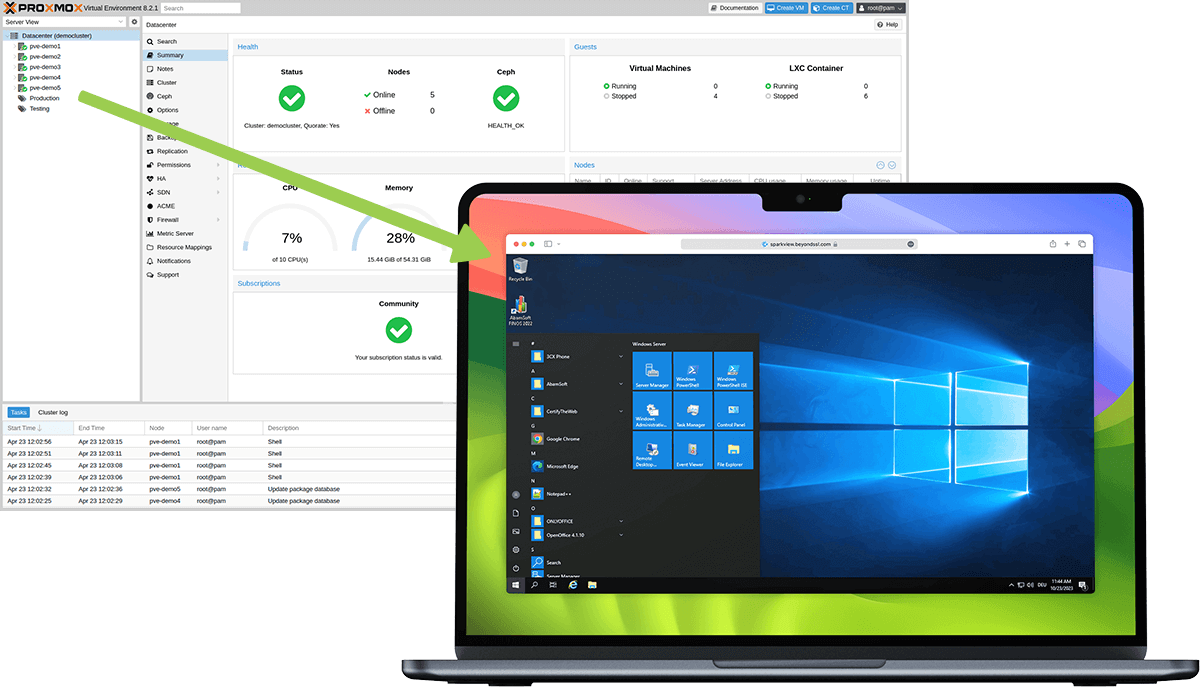
Use case
Secure Remote Access to Your Virtualization Environment with Proxmox
all
The Perfect Combination: SparkView and Proxmox for Secure and Efficient IT Infrastructures. With Zero Trust and virtualization, you can eliminate VPN security risks, reduce administrative complexity, and minimize the cost pressures of traditional solutions. Maximum security through Zero Trust > SparkView grants access to Proxmox resources only after strict authentication. >Each access package is checked individually, which prevents lateral movement. Simple administration >Proxmox offers centralized management for VMs and containers. >SparkView enables administrators to easily control access rights for Proxmox services - without separate client software. Cost efficiency >Proxmox and SparkView offer excellent value. >No need for expensive VPN licenses or additional hardware.
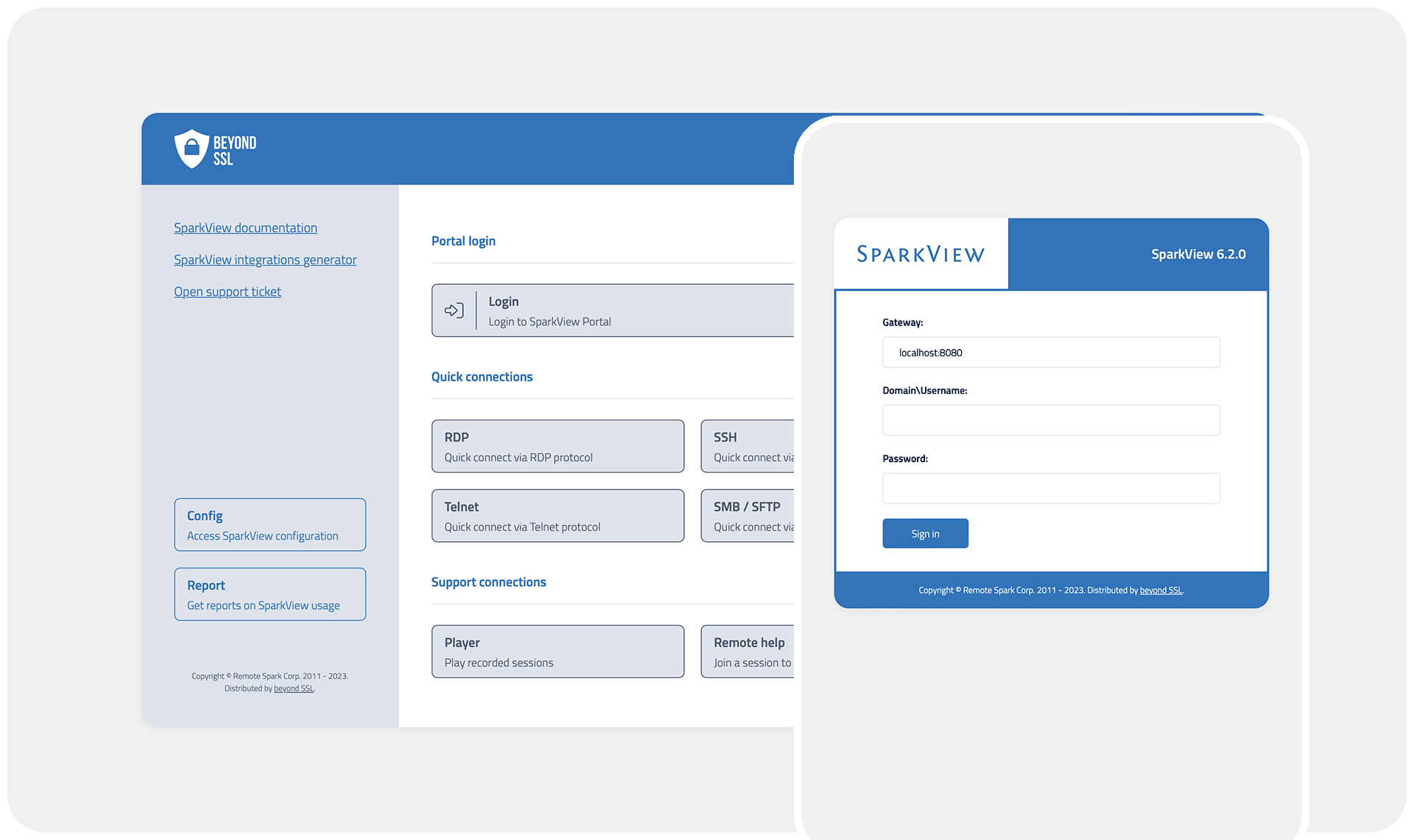
Use case
Clientless ZTNA-compliant Remote Access - without VPN
all
Traditional VPNs are no longer sufficient for securing remote access. SparkView offers a clientless Zero Trust Network Access (ZTNA) solution, enabling secure, browser-based access to internal applications and desktops—without the complexity of VPNs. Users can connect seamlessly from any device while organizations maintain granular access control and zero trust security principles, ensuring that only authorized users gain entry to corporate resources. SparkView enhances security, flexibility, and user experience, making remote work efficient and risk-free.

Use case
Access any app on your Chromebook—even if it's not ChromeOS-native
Education, Gov, All Industries
SparkView lets you get even more out of your Chromebooks! SparkView is easy to use via the browser or as an app (PWA) and gives your Chromebook superpowers: you get secure and fast access to internal company apps, desktops, and servers directly in your browser. With SparkView, you can also seamlessly access non-ChromeOS-native apps—whether they’re specially developed applications, legacy systems, Windows apps, macOS apps, and more—ensuring you have the right tools at your fingertips, no matter the platform. And best of all: no data leaves the company!
When exploring the Zero Trust industry in Israel, several key considerations emerge. The regulatory environment is crucial, especially as Israel is known for its robust cybersecurity laws and compliance requirements. Understanding the implications of these regulations can help in evaluating potential partners and solutions. The competitive landscape is vibrant, with numerous startups and established firms innovating in Zero Trust security solutions. It’s important to assess the technological advancements these companies are making, as Israel is a global leader in cybersecurity due to its military tech background and extensive R&D investments. Challenges in the Zero Trust space include the integration of legacy systems with new security protocols and the ongoing adaptation to evolving cyber threats. However, the opportunities are significant, as organizations increasingly recognize the need for more sophisticated security frameworks, especially in light of recent high-profile breaches. Furthermore, the global market relevance of Zero Trust is growing, as companies worldwide look to adopt these strategies to enhance their cyber defenses. Environmental concerns are also gaining traction in the tech industry, emphasizing the need for sustainable practices in cybersecurity solutions. By considering these factors, individuals can make informed decisions when researching companies and solutions in the Zero Trust sector in Israel.
Some interesting numbers and facts about your company results for Zero Trust
| Country with most fitting companies | Israel |
| Amount of fitting manufacturers | 115 |
| Amount of suitable service providers | 72 |
| Average amount of employees | 11-50 |
| Oldest suiting company | 2007 |
| Youngest suiting company | 2020 |
Some interesting questions that has been asked about the results you have just received for Zero Trust
What are related technologies to Zero Trust?
Based on our calculations related technologies to Zero Trust are Big Data, E-Health, Retail Tech, Artificial Intelligence & Machine Learning, E-Commerce
Which industries are mostly working on Zero Trust?
The most represented industries which are working in Zero Trust are IT, Software and Services, Other, Telecommunications, Finance and Insurance, Consulting
How does ensun find these Zero Trust Companies?
ensun uses an advanced search and ranking system capable of sifting through millions of companies and hundreds of millions of products and services to identify suitable matches. This is achieved by leveraging cutting-edge technologies, including Artificial Intelligence.