
The B2B platform for the best purchasing descision. Identify and compare relevant B2B manufacturers, suppliers and retailers
Close
Filter
Result configuration
Continents
Select continent
Locations
Result types
Company type
Select company type
Industries
Select industry
Company status
Select company status preset
Number of employees
Min.
Max.
Founding year
Balasys It
Hungary
B
11-50 Employees
2000
Key takeaway
The company emphasizes the Zero Trust security concept, which asserts that organizations should not automatically trust anything inside or outside their perimeters. They have developed a comprehensive Zero Trust portfolio, including innovative solutions for network security and API management, highlighting their expertise in implementing this security framework.
Reference
Product
Zero Trust | Balasys IT Ltd.
Based on the thoughtful combination of best-of-breed security components, Balasys have designed an end-to-end Zero Trust solution that can be deployed either in greenfield projects, or through integrating certain elements into your existing architecture.
Zentera Systems
San Jose, United States
B
11-50 Employees
2012
Key takeaway
Zentera Systems, Inc. emphasizes the importance of a Zero Trust approach, highlighting their CoIP Platform that ensures all network access is authorized, thereby enhancing security without hindering productivity. Their solutions are designed to help businesses, regardless of size, effectively implement Zero Trust security, even for legacy applications and data.
Reference
Product
Zero Trust Security | Zentera Systems, Inc.
The CoIP overlay provides an instant on-ramp for Zero Trust, enabling companies to adopt a Zero Trust security posture for even legacy apps and data.
Riverside Research
Lexington, United States
B
501-1000 Employees
1967
Key takeaway
Riverside Research emphasizes its commitment to delivering innovative solutions for national security challenges, which aligns with the principles of Zero Trust by focusing on independent, trusted expertise and collaboration. Their mission to provide timely and cost-effective solutions may be relevant for organizations looking to implement Zero Trust strategies.
Reference
Service
Zero Trust
Looking for more accurate results?
Find the right companies for free by entering your custom query!
25M+ companies
250M+ products
Free to use
Trustgrid
Austin, United States
B
11-50 Employees
2016
Key takeaway
The Trustgrid platform incorporates zero trust remote user access (ZTNA) as part of its innovative networking and edge computing solutions. This approach enhances connectivity and application delivery across various environments, making it particularly relevant for managing secure connections in fintech applications.
Reference
Core business
Zero Trust Network Access Explained - trustgrid.io
VM Blog | Article
Ascent Solutions
Minneapolis, United States
B
101-250 Employees
2008
Key takeaway
The company emphasizes its commitment to cybersecurity, highlighting its partnership with experts dedicated to protecting organizations through essential plans and programs. This aligns with the principles of Zero Trust, which focuses on rigorous security measures to defend against evolving threats.
Reference
Product
Zero Trust
Ridge IT
Richmond, United States
B
1-10 Employees
-
Key takeaway
Ridge IT is a leading cybersecurity firm that emphasizes Zero Trust principles in its approach. They provide tailored cybersecurity solutions and managed services, ensuring comprehensive protection for clients across various sectors.
Reference
Product
Zero Trust – Ridge IT
Stygian Vortex Security Consultants
United States
B
1-10 Employees
2021
Key takeaway
Keith Glynn, with his extensive experience in enterprise security architecture and specialized knowledge in operational technology and IoT security, is well-equipped to assist manufacturers in implementing and operationalizing Zero Trust principles. His expertise in creating cybersecurity ecosystems helps protect supply chains from cyber-attacks, making him a valuable asset in the transition to a Zero Trust model.
Reference
Service
Zero Trust Implementation & Operationalization – Stygian Vortex Security Consultants
Portnox
Raanana, Israel
B
11-50 Employees
2007
Key takeaway
Portnox offers a comprehensive zero trust solution that integrates passwordless authentication, authorization, risk monitoring, and compliance enforcement, ensuring secure access to networks and infrastructure. Their Portnox Cloud delivers advanced zero trust security capabilities, making it suitable for organizations of all sizes.
Reference
Product
Zero Trust Network Access (ZTNA) - Portnox
Protect your corporate network layers from cyber threats of all kinds with powerful cloud-native ZTNA from Portnox.
ModernCyber
Melbourne, United States
B
1-10 Employees
2021
Key takeaway
ModernCyber emphasizes the importance of zero trust principles, such as least privilege and system integration, as critical factors in enhancing cybersecurity and preventing breaches. Their innovative services and expertise aim to provide organizations with scalable access control solutions that align with zero trust strategies.
Reference
Service
Zero Trust as a Service (ZTaaS) | ModernCyber
Zero Trust by Default
Gradient
Boston, United States
B
11-50 Employees
2018
Key takeaway
Gradient Cybersecurity Mesh (GCM) is a comprehensive zero-trust solution that integrates hardware-based roots of trust with advanced software to effectively eliminate credential-based cyberattacks. By continuously monitoring device identity and integrity, GCM ensures secure credential issuance and policy management, providing robust protection for enterprise environments.
Reference
Product
Gradient Technologies - Enterprise Zero Trust Access
Technologies which have been searched by others and may be interesting for you:
A selection of suitable products and services provided by verified companies according to your search.
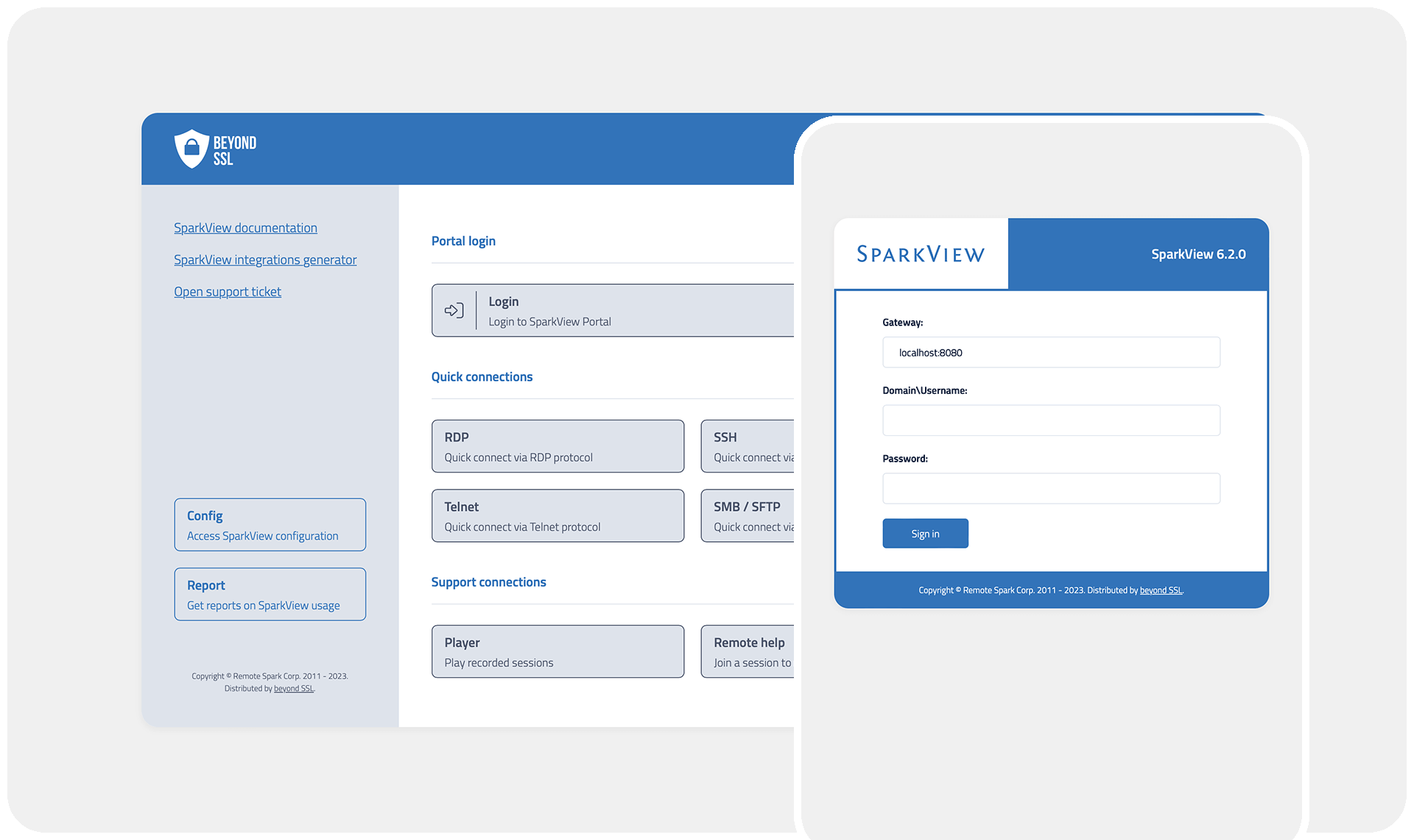
Product
SparkView ZTNA
Go to product
A selection of suitable use cases for products or services provided by verified companies according to your search.

Use case
Access any app on your Chromebook—even if it's not ChromeOS-native
Education, Gov, All Industries
SparkView lets you get even more out of your Chromebooks! SparkView is easy to use via the browser or as an app (PWA) and gives your Chromebook superpowers: you get secure and fast access to internal company apps, desktops, and servers directly in your browser. With SparkView, you can also seamlessly access non-ChromeOS-native apps—whether they’re specially developed applications, legacy systems, Windows apps, macOS apps, and more—ensuring you have the right tools at your fingertips, no matter the platform. And best of all: no data leaves the company!
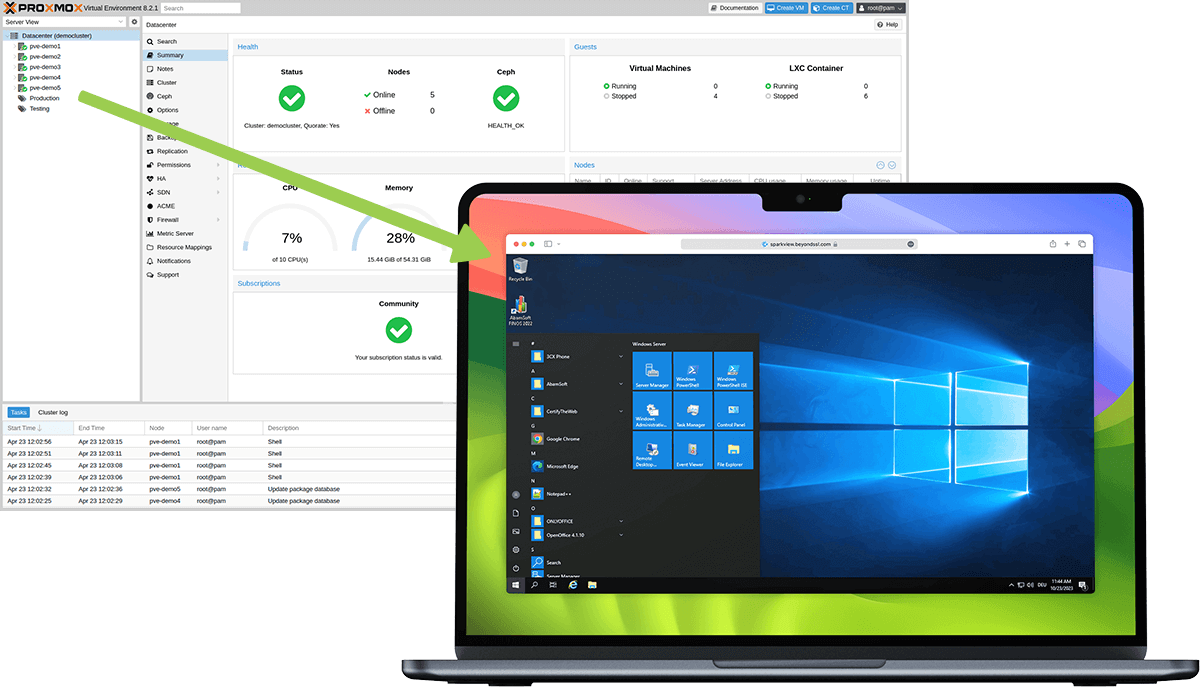
Use case
Secure Remote Access to Your Virtualization Environment with Proxmox
all
The Perfect Combination: SparkView and Proxmox for Secure and Efficient IT Infrastructures. With Zero Trust and virtualization, you can eliminate VPN security risks, reduce administrative complexity, and minimize the cost pressures of traditional solutions. Maximum security through Zero Trust > SparkView grants access to Proxmox resources only after strict authentication. >Each access package is checked individually, which prevents lateral movement. Simple administration >Proxmox offers centralized management for VMs and containers. >SparkView enables administrators to easily control access rights for Proxmox services - without separate client software. Cost efficiency >Proxmox and SparkView offer excellent value. >No need for expensive VPN licenses or additional hardware.
Use case
Clientless ZTNA-compliant Remote Access - without VPN
all
Traditional VPNs are no longer sufficient for securing remote access. SparkView offers a clientless Zero Trust Network Access (ZTNA) solution, enabling secure, browser-based access to internal applications and desktops—without the complexity of VPNs. Users can connect seamlessly from any device while organizations maintain granular access control and zero trust security principles, ensuring that only authorized users gain entry to corporate resources. SparkView enhances security, flexibility, and user experience, making remote work efficient and risk-free.

Use case
Access any app on your Chromebook—even if it's not ChromeOS-native
Education, Gov, All Industries
SparkView lets you get even more out of your Chromebooks! SparkView is easy to use via the browser or as an app (PWA) and gives your Chromebook superpowers: you get secure and fast access to internal company apps, desktops, and servers directly in your browser. With SparkView, you can also seamlessly access non-ChromeOS-native apps—whether they’re specially developed applications, legacy systems, Windows apps, macOS apps, and more—ensuring you have the right tools at your fingertips, no matter the platform. And best of all: no data leaves the company!
Zero Trust is a cybersecurity framework that operates on the principle of "never trust, always verify." This approach assumes that threats could be internal or external, and therefore, every access request must be authenticated and authorized, regardless of the requestor's location. It emphasizes strict identity verification and continuous monitoring, ensuring that users or devices are only granted the minimum necessary access to perform their tasks. By implementing Zero Trust, organizations can significantly reduce the risk of data breaches and enhance their overall security posture.
Zero Trust enhances security by adopting a strict verification model, ensuring that every user and device is authenticated and authorized before gaining access to any network resources. This approach minimizes the risk of unauthorized access, as trust is never assumed based on location or previous interactions. Furthermore, Zero Trust employs continuous monitoring and validation of user activity, which helps to detect and respond to potential threats in real-time. By segmenting access to resources and enforcing the principle of least privilege, organizations can effectively limit the potential impact of breaches and ensure that sensitive data remains protected.
Verify Identity Continuously In a Zero Trust model, continuous verification of user identity is essential. It requires that every user, device, and network connection is authenticated and authorized for access to resources, regardless of their location. This principle helps ensure that only legitimate users can access sensitive information. Least Privilege Access Implementing least privilege access means that users are given the minimum level of access necessary to perform their functions. This limits potential damage from compromised accounts and reduces the risk of unauthorized data exposure. By tightly controlling permissions, organizations can better safeguard their critical assets.
1. Assess Current Security Posture
Begin by evaluating the existing security framework to identify vulnerabilities and areas for improvement. This assessment should include a thorough review of network architecture, user access controls, and data protection measures.
2. Define the Protect Surface
Identify the critical assets, including sensitive data, applications, and services that need protection. Unlike traditional perimeter-based security, Zero Trust emphasizes safeguarding these protect surfaces rather than general network boundaries.
3. Implement Strong Identity and Access Management
Utilize robust identity and access management (IAM) solutions to enforce strict authentication and authorization protocols. Multi-factor authentication (MFA) should be standard to ensure that only verified users gain access to resources.
4. Micro-Segmentation
Adopt micro-segmentation to isolate workloads and limit lateral movement within the network. By creating smaller, manageable segments, organizations can enforce policies more effectively and reduce the attack surface.
5. Continuous Monitoring and Analytics
Establish continuous monitoring systems to analyze user behavior and detect anomalies. Employing advanced analytics can help in recognizing potential threats and responding swiftly to incidents.
6. Regularly Update Policies
Keep security policies up to date to reflect changes in the network environment and evolving threats. Regular reviews and updates ensure that the Zero Trust model remains effective against new challenges.
1. Enhanced Security
Adopting a Zero Trust model significantly improves security by assuming that threats can exist both outside and within the network. This model enforces strict access controls and continuous authentication, which reduces the risk of unauthorized access and data breaches.
2. Reduced Attack Surface
Zero Trust limits access to sensitive data and systems, minimizing the attack surface. By requiring verification for every access request, it makes it harder for attackers to move laterally within the network, thereby containing potential security incidents more effectively.
Some interesting numbers and facts about your company results for Zero Trust
| Country with most fitting companies | United States |
| Amount of fitting manufacturers | 7316 |
| Amount of suitable service providers | 8020 |
| Average amount of employees | 11-50 |
| Oldest suiting company | 1967 |
| Youngest suiting company | 2021 |
20%
40%
60%
80%
Some interesting questions that has been asked about the results you have just received for Zero Trust
What are related technologies to Zero Trust?
Based on our calculations related technologies to Zero Trust are Big Data, E-Health, Retail Tech, Artificial Intelligence & Machine Learning, E-Commerce
Who are Start-Ups in the field of Zero Trust?
Start-Ups who are working in Zero Trust are Stygian Vortex Security Consultants, ModernCyber
Which industries are mostly working on Zero Trust?
The most represented industries which are working in Zero Trust are IT, Software and Services, Other, Defense, Telecommunications, Finance and Insurance
How does ensun find these Zero Trust Companies?
ensun uses an advanced search and ranking system capable of sifting through millions of companies and hundreds of millions of products and services to identify suitable matches. This is achieved by leveraging cutting-edge technologies, including Artificial Intelligence.